Cryptocurrency trading and investment firm Kronos Research said $26 million worth of cryptocurrency was stolen from its systems following a cyberattack. The company said on Saturday that it experienced “unauthorized access” to some of its application programming interface (API) keys, forcing it to pause trading and begin an investigation. By Sunday, the company confirmed that […]
According to recent research on employee offboarding, 70% of IT professionals say they’ve experienced the negative effects of incomplete IT offboarding, whether in the form of a security incident tied to an account that wasn’t deprovisioned, a surprise bill for resources that aren’t in use anymore, or a missed handoff of a critical resource or […]
Overview In 2022, NSFOCUS Research Labs revealed a large-scale APT attack campaign called DarkCasino and identified an active and dangerous aggressive threat actor. By continuously tracking and in-depth study of the attacker’s activities, NSFOCUS Research Labs has ruled out its link with known APT groups, confirmed its high-level persistent threat nature, and following the operational […]
ESET Research How ESET Research found a kill switch that had been used to take down one of the most prolific botnets out there 01 Nov 2023 • , 3 min. read In August 2023, the notorious Mozi botnet, infamous for exploiting vulnerabilities in hundreds of thousands of IoT devices each year, experienced a sudden […]
Key Findings Check Point Research (CPR) is monitoring an ongoing Iranian espionage campaign by Scarred Manticore, an actor affiliated with the Ministry of Intelligence and Security (MOIS). The attacks rely on LIONTAIL, an advanced passive malware framework installed on Windows servers. For stealth purposes, LIONTIAL implants utilize direct calls to Windows HTTP stack driver HTTP.sys […]
ESET Research ESET Research recommends updating Roundcube Webmail to the latest available version as soon as possible Matthieu Faou 25 Oct 2023 • , 5 min. read ESET Research has been closely tracking the cyberespionage operations of Winter Vivern for more than a year and, during our routine monitoring, we found that the group began […]
Last updated at Mon, 16 Oct 2023 15:02:23 GMT As part of our continuing research project into managed file transfer risk, including JSCAPE MFT and Fortra Globalscape EFT Server, Rapid7 discovered several vulnerabilities in South River Technologies’ Titan MFT and Titan SFTP servers. Although these require unusual circumstances or non-default configurations, as well as a […]
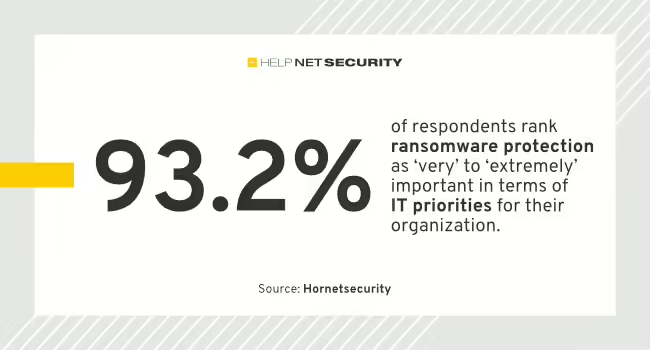
60% of companies are ‘very’ to ‘extremely’ concerned about ransomware attacks, according to latest research from Hornetsecurity. Businesses acknowledge ransomware risk Hornetsecurity revealed that 92.5% businesses are aware of ransomware’s potential for negative impact. Still, just 54% of respondents said their leadership is ‘actively involved in conversations and decision-making’ around preventing such attacks. 39.7% said […]
Research by: Jiri Vinopal Highlights Check Point Research (CPR) introduces a new method for running hidden implanted code in ReadyToRun (R2R) compiled .NET binaries, R2R stomping. We explain the implementation of R2R stomping with a focus on its internals. The resulting problems of the R2R stomping technique will affect the work of the reverse engineers […]