Apr 04, 2024NewsroomVulnerability / Internet Protocol New research has found that the CONTINUATION frame in the HTTP/2 protocol can be exploited to conduct denial-of-service (DoS) attacks. The technique has been codenamed HTTP/2 CONTINUATION Flood by security researcher Bartek Nowotarski, who reported the issue to the CERT Coordination Center (CERT/CC) on January 25, 2024. “Many HTTP/2 […]
CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign
The decrypted request content is as follows: 1000|87|283|Yes|6.1.7|||” Conclusion In this research, a follow-up to our Water Hydra APT Zero Day campaign analysis, we explored how the DarkGate operators were able to exploit CVE-2024-21412 as a zero-day attack to deploy the complex and evolving DarkGate malware. We also explored how security bypass vulnerabilities can be […]
Iranian nation-state threat actors are targeting entities based in the U.S. and Israel, according to research that Google published Tuesday. According to a report about cyberwarfare surrounding the ongoing Israel-Hamas war that began in October, “Iran aggressively targeted Israel and the United States in the years leading up to Hamas’ attack on October 7” and […]
SiCat is an open-source tool for exploit research designed to source and compile information about exploits from open channels and internal databases. Its primary aim is to assist in cybersecurity, enabling users to search the internet for potential vulnerabilities and corresponding exploits. Akas Wisnu Aji, the creator of SiCat, outlined the key features of the […]
SiCat is an open-source tool for exploit research designed to source and compile information about exploits from open channels and internal databases. Its primary aim is to assist in cybersecurity, enabling users to search the internet for potential vulnerabilities and corresponding exploits. Akas Wisnu Aji, the creator of SiCat, outlined the key features of the […]
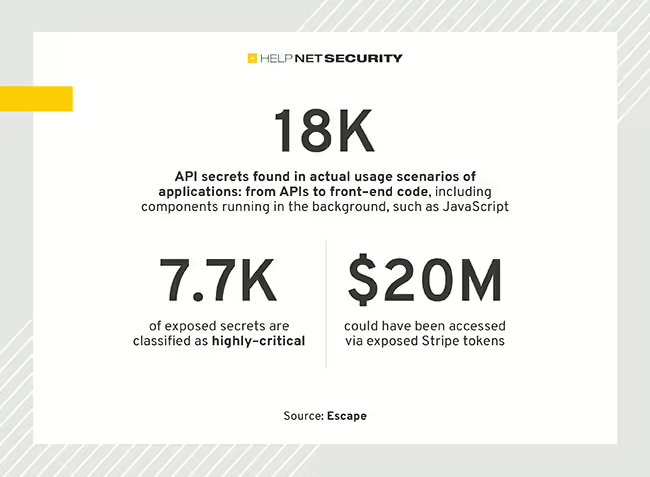
Escape’s security research team scanned 189.5 million URLs and found more than 18,000 exposed API secrets. 41% of exposed secrets were highly critical, i.e. could lead to financial risks for the organizations. Exposed API secrets The exposed secrets include hundreds of Stripe, GitHub/GitLab tokens, RSA private keys, OpenAI keys, AWS tokens, Twitch secret keys, cryptocurrency […]
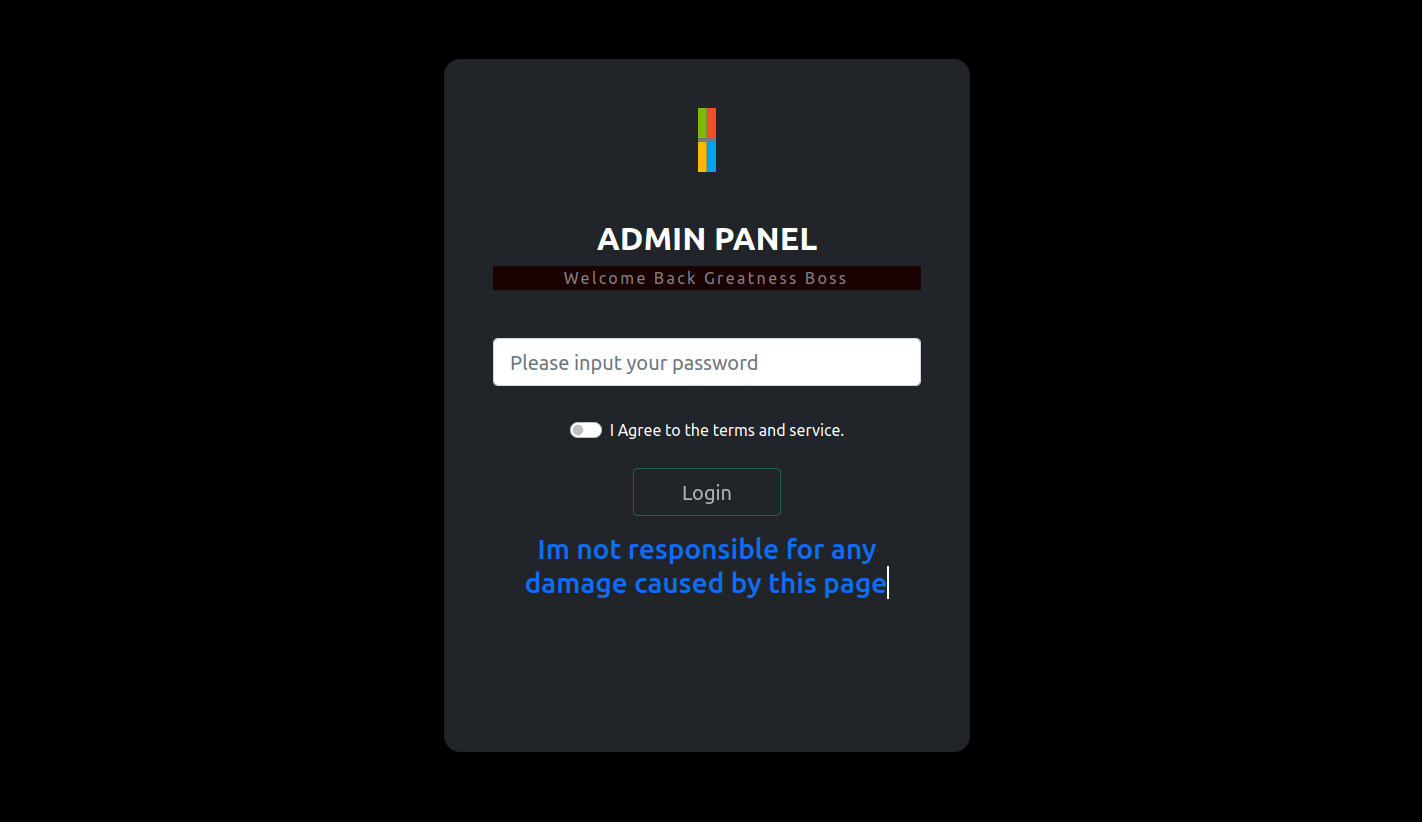
Emerging in 2022, a phishing tool known as Greatness has caught the attention of our research team due to its coordinated efforts to breach Microsoft 365 accounts and presence on compromised websites. More disturbingly, it has shown effectiveness against multi-factor authentication (MFA), elevating the potential threat level. Identified as a Phishing as a Service (PhaaS) […]
Pro-Ukraine hackers have reportedly breached a Russian scientific research center, Ukraine’s defense intelligence directorate (GUR) said. According to GUR’s report on Wednesday, the hacker group called “BO Team” attacked the State Research Center on Space Hydrometeorology, also known as “Planeta,” and destroyed its database and valuable equipment. Planeta is a Russian state enterprise that receives […]
This post is also available in: 日本語 (Japanese) Executive Summary During our research discovering threats in legitimate network traffic, activity generated by a certain type of Android Package Kit (APK) files kept hitting our radar. This activity led us to conduct an in-depth investigation on the associated APK files. Our research revealed a family of […]