Italian National Research Council Artificial intelligence (AI) is accelerating new discoveries across industries, from video production to medicine — and now, it’s expanding what we know about antiquity. On Tuesday, researchers at the University of Pisa in Italy announced that they have successfully used AI to decipher a papyrus scroll found in Herculaneum, a town near […]
In a result of its research investigation efforts, Security Explorations, a research lab of AG Security Research company, conducted security analysis of Microsoft Warbird and Protected Media Path technologies. This section of our website presents initial information regarding the project. Microsoft Warbird and Protected Media Path description Microsoft Protected Media Path (PMP) is a set […]
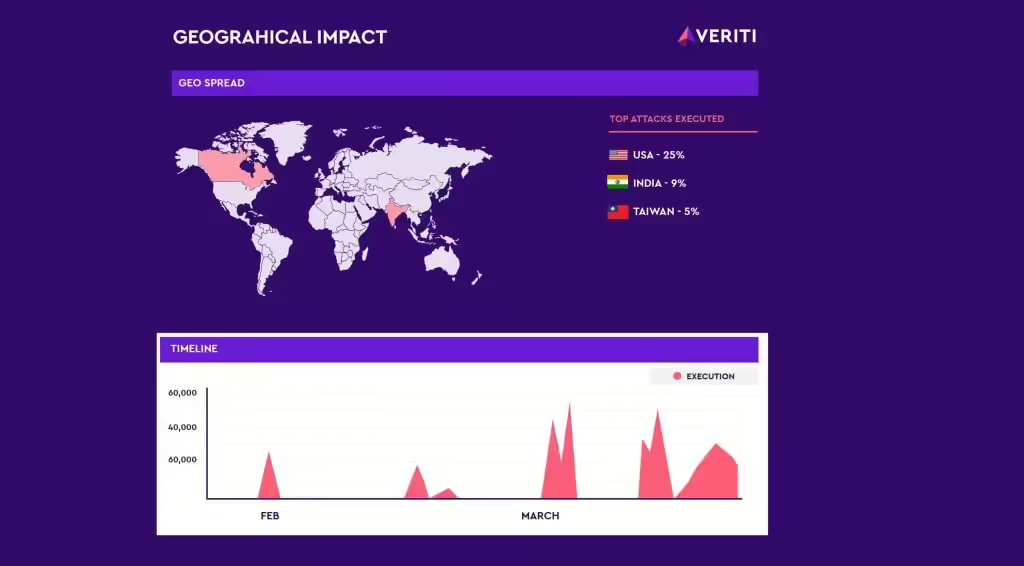
Veriti Research has discovered a surge in attacks from operators of the Androxgh0st malware family, uncovering over 600 servers compromised primarily in the U.S., India and Taiwan. According to Veriti’s blog post, the adversary behind Androxgh0st had their C2 server exposed, which could allow for a counterstrike by revealing the impacted targets. The researchers then […]
Apr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and processes. “When a user executes a function that has a path argument in Windows, the DOS path at which the file or […]
Apr 19, 2024NewsroomNetwork Security / Firmware Security Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for an updated version of modular backdoor dubbed Waterbear as well as its enhanced successor referred to […]
April 16, 2024 Greg Lesnewich, Crista Giering, and the Proofpoint Threat Research Team Key takeaways TA427 regularly engages in benign conversation starter campaigns to establish contact with targets for long-term exchanges of information on topics of strategic importance to the North Korean regime. In addition to using specially crafted lure content, TA427 heavily leverages think […]
Apr 16, 2024NewsroomCloud Security / DevSecOps New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant risks to organizations. The vulnerability has been codenamed LeakyCLI by cloud security firm Orca. “Some commands on Azure CLI, AWS CLI, and […]
A recent research study has shed light on the decade-long activities of a Romanian cyber threat group known as RUBYCARP, which uses techniques such as cryptocurrency mining and phishing. One of the key findings from the technical write-up, published by Sysdig today, is the group’s use of a script capable of simultaneously deploying multiple cryptocurrency […]
Apr 05, 2024NewsroomArtificial Intelligence / Supply Chain Attack New research has found that artificial intelligence (AI)-as-a-service providers such as Hugging Face are susceptible to two critical risks that could allow threat actors to escalate privileges, gain cross-tenant access to other customers’ models, and even take over the continuous integration and continuous deployment (CI/CD) pipelines. “Malicious […]