In Recent years, Netflix and Apple TV+ have been duking it out to have the most prestigious film offerings, but some of the best movies are on Amazon Prime Video. The streamer was one of the first to go around picking up film festival darlings and other lovable favorites, and they’re all still there in […]
A recent incident in West Africa has once again brought attention to the persistent threat posed by the LockBit ransomware. Cybercriminals, armed with stolen administrator credentials, have deployed a customized variant of the encryption malware equipped with self-propagation capabilities. Exploiting privileged access, they breached corporate infrastructure, demonstrating the ongoing risk posed by the leaked LockBit […]
Security researchers have stopped a “credible” takeover attempt reminiscent of the recent XZ Utils backdoor incident — further highlighting the urgent need to address weaknesses in the management of open source software. Researchers at the OpenJS Foundation — which monitors JavaScript projects used by billions of websites worldwide — said Monday that they “received a […]
CISA is collaborating with private industry partners to respond to a recent compromise discovered by independent security researchers impacting Sisense, a company that provides data analytics services. CISA urges Sisense customers to: Reset credentials and secrets potentially exposed to, or used to access, Sisense services. Investigate—and report to CISA—any suspicious activity involving credentials potentially exposed […]
In recent months, we have encountered a number of cases where attackers inject malware into website software that allows for custom or miscellaneous code — for example, the miscellaneous scripts area of the Magento admin panel, or WordPress plugins such as Custom CSS & JS. Custom script editors are popular with bad actors because they […]
In a recent attack campaign, cybercriminals were discovered cleverly manipulating GitHub’s search functionality, and using meticulously crafted repositories to distribute malware. Key Points GitHub search manipulation: Attackers create malicious repositories with popular names and topics, using techniques like automated updates and fake stars to boost search rankings and deceive users. Malicious code is often hidden […]
A recent research study has shed light on the decade-long activities of a Romanian cyber threat group known as RUBYCARP, which uses techniques such as cryptocurrency mining and phishing. One of the key findings from the technical write-up, published by Sysdig today, is the group’s use of a script capable of simultaneously deploying multiple cryptocurrency […]
A recent analysis by Cyble has revealed a concerning escalation in the fake e-shop campaign, signaling a looming threat to banking security across various regions. Initially focused on Malaysian banks, this e-shop phishing campaign has now extended its reach to financial institutions in Vietnam and Myanmar. What sets this phishing campaign apart from others on […]
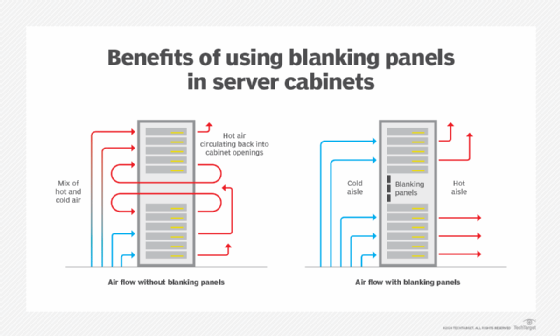
Advancements in modern data center operations lead to new capabilities and management challenges. Recent changes to modern data center standards and design maximize both operational and energy efficiency. The modern data center is far more sophisticated than its predecessors. With proper maintenance and management, today’s data centers can support new generations of hardware for years […]