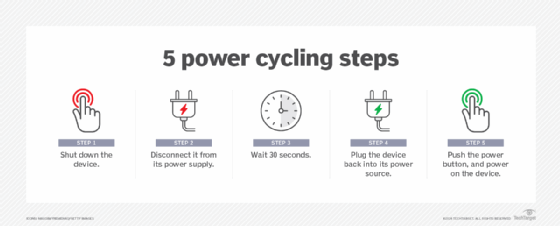
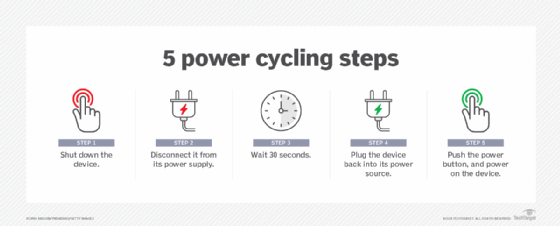
What is power cycling? Power cycling is the process of turning hardware off and then turning it on again. In the data center, technicians use power cycling to test the durability and reliability of network components. It is commonplace for servers to operate for months or even years without a reboot or disruption. These long […]
What is power cycling? Power cycling is the process of turning hardware off and then turning it on again. In the data center, technicians use power cycling to test the durability and reliability of network components. It is commonplace for servers to operate for months or even years without a reboot or disruption. These long […]
The security issue could lead to the exfiltration of process memory addresses, which could help attackers bypass protection mechanisms like Address Space Layout Randomization (ASLR).
The Pentagon is in the process of alerting an undisclosed number of current and former employees, job applicants and partners that their sensitive personal information may have been exposed online in a “data breach incident” that was first detected in early 2023. DefenseScoop viewed a notice — dated Feb. 1, 2024 and sent by the […]
Exploiting a vulnerable Minifilter Driver to create a process killer Pierluigi Paganini February 09, 2024 Researcher demonstrated how to exploit a signed Minifilter Driver in a BYOVD attack to terminate a specific process from the kernel. Exploiting a signed Minifilter Driver that can be used to used the BYOVD attack technique to a program able […]
Dec 18, 2023The Hacker NewsTechnology / Application Security Low-code/no-code (LCNC) and robotic process automation (RPA) have gained immense popularity, but how secure are they? Is your security team paying enough attention in an era of rapid digital transformation, where business users are empowered to create applications swiftly using platforms like Microsoft PowerApps, UiPath, ServiceNow, Mendix, […]
By Published: 12 Dec 2023 A server is a computer intended to process centralized enterprise-class applications and communicate within a busy… business network. Although any computer can function as a server, computers that are designed and built as servers typically provide high-end computing resources, including the fastest processors, extensive amounts of fast memory, local disk […]
By Published: 12 Dec 2023 A server is a computer intended to process centralized enterprise-class applications and communicate within a busy… business network. Although any computer can function as a server, computers that are designed and built as servers typically provide high-end computing resources, including the fastest processors, extensive amounts of fast memory, local disk […]
Dec 11, 2023NewsroomEndpoint Security / Malware A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response (EDR) systems. SafeBreach researcher Alon Leviev said the methods are “capable of working across all processes without any limitations, making them more […]