Docker has been one of the most popular default container runtime engines for users because of how straightforward it is. However, Red Hat has changed the way it supports running Docker, which causes users to switch to Podman. Security is a speculated reason why Red Hat changed its support for Docker. Podman is a close […]
A popular tool used by numerous state and local governments to manage public records requests contained defects that could have allowed hackers to download troves of unsecured files tethered to records inquiries, including highly sensitive personal information like IDs, fingerprints, child welfare documentation and medical reports, Nextgov/FCW has learned. The flaws, which have been remedied, […]
OffSec has released Kali Linux 2024.1, the latest version of its popular penetration testing and digital forensics platform. The new version comes with new tools, a fresh look (themes, wallpapers and icons for Kali and Kali Purple), a new image viewer for the Gnome desktop and a usability enhancement to the Xfce desktop (the ability […]
Feb 27, 2024NewsroomWebsite Security / Cryptojacking A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate Member that has more than 200,000 active installations. The vulnerability, tracked as CVE-2024-1071, carries a CVSS score of 9.8 out of a maximum of 10. Security researcher Christiaan Swiers has been credited with discovering and […]
Machine learning and artificial intelligence are popular buzzwords for today’s IT professionals, but in the case of your organization’s data centers, they hold real promise. ML software actively predicts situations faster than you or your team might notice them and maybe even solves them quicker. These systems are a logical extension of today’s hybrid data […]
Popular remote monitoring and management software company AnyDesk said all versions of its tool obtained from “official sources” are safe to use following a cyberattack that caused days of outages and concern among users. The cyberattack affected servers in Spain and Portugal but nowhere else, AnyDesk said. The company confirmed last Friday that a four-day […]
Last updated 9 February, 2024 VirtualDJ is a long-standing and popular piece of DJ software. In fact, it is the first piece of DJ software I personally used extensively, way back in 2004. It has a loyal user base, with a particularly strong following among mobile DJs, video DJs and karaoke DJs. That said, it […]
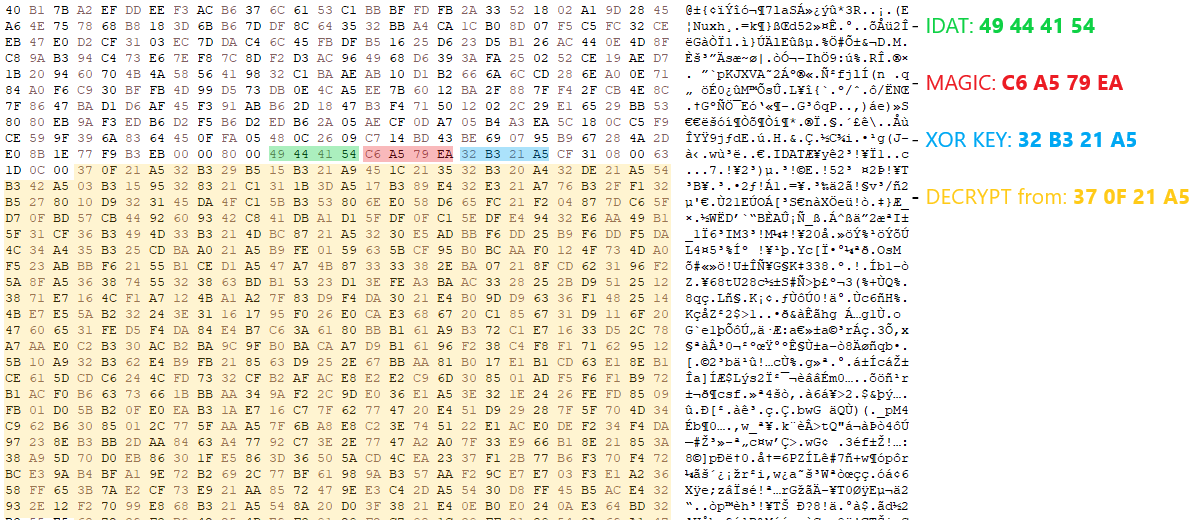
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its complexity and defense evasion CrowdStrike detects this new HijackLoader variant using machine learning and behavior-based detection capabilities CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion […]
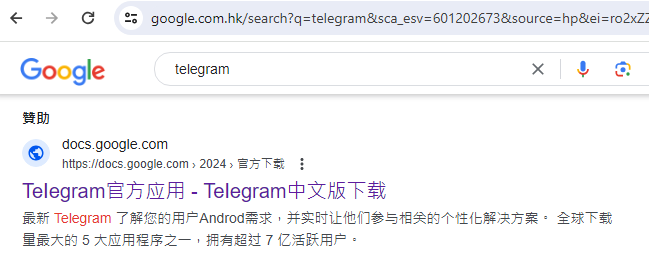
An ongoing campaign of malicious ads has been targeting Chinese-speaking users with lures for popular messaging applications such as Telegram or LINE with the intent of dropping malware. Interestingly, software like Telegram is heavily restricted and was previously banned in China. Many Google services, including Google search, are also either restricted or heavily censored in […]