The agency responsible for monitoring financial sanctions in Britain has never detected an illicit payment to an entity embargoed under the country’s counter-ransomware regime, according to information obtained by Recorded Future News. The sanctions regime explicitly prohibits victims from making any extortion payments to the 29 individuals and 5 entities listed under the United Kingdom’s […]
Axonius, one of the bigger players in the world of enterprise asset management — understanding and monitoring the digital assets and infrastructure that make up an organization’s network — has raised $200 million more in funding to expand its business on the heels of the company’s growth. The company, now nearly five years on from […]
Axonius, one of the bigger players in the world of enterprise asset management — understanding and monitoring the digital assets and infrastructure that make up an organization’s network — has raised $200 million more in funding to expand its business on the heels of the company’s growth. The company, now nearly five years on from […]
System monitoring tools, like Glances, offer data center administrators two advantages: Ensure the system is not overwhelmed and provide preventive maintenance. Today’s OSes provide many tools to make monitoring data centers easier. Common performance monitoring utilities include top and htop for Linux, top for macOS, and Task Manager and Resource Monitor for Windows. Glances is […]
Popular remote monitoring and management software company AnyDesk said all versions of its tool obtained from “official sources” are safe to use following a cyberattack that caused days of outages and concern among users. The cyberattack affected servers in Spain and Portugal but nowhere else, AnyDesk said. The company confirmed last Friday that a four-day […]
A blind SQL injection vulnerability (CVE-2023-51448) in Cacti, a widely-used network monitoring, performance and fault management framework, could lead to information disclosure and potentially remote code execution. Cacti is often used in network operation centers of telecoms and web hosting providers, to collect network performance data and store it in RRDtool, a logging and graphing […]
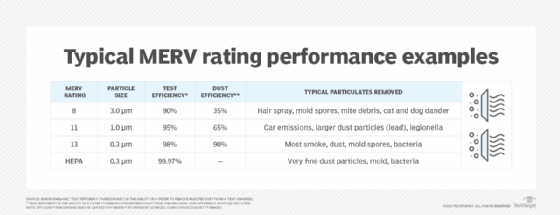
Monitoring indoor air quality is critical to the health of computing equipment in data centers. Outside air must circulate in the data center for the safety of people who occupy it at any time. However, outside air brings particulates and gaseous contaminants into a data center. To combat these harmful particulates damaging equipment, data centers […]
The National Telecommunication Monitoring Centre (NTMC) in Bangladesh has exposed a database to the open web. The types of data that leaked online were extensive, American technology magazine WIRED reports. The list of data is long: names, professions, blood groups, parents’ names, phone numbers, the length of calls, vehicle registrations, passport details and fingerprint photos, […]
Cloud monitoring, log management, and SIEM tools provider Sumo Logic is urging customers to change credentials following the discovery of a security breach. The company revealed on Tuesday that a “potential security incident” discovered on November 3 involved unauthorized access to a Sumo Logic AWS account through the use of compromised credentials. There is no […]
- 1
- 2