Endpoint Security , Governance & Risk Management , Information Sharing GAO Report Criticizes CISA’s Info Sharing Programs for Critical Infrastructure Prajeet Nair (@prajeetspeaks) • March 11, 2024 The U.S. Government Accountability Office has found inefficiencies in the Cybersecurity and Infrastructure Security Agency’s information-sharing practices with critical infrastructure stakeholders – warning that the agency […]
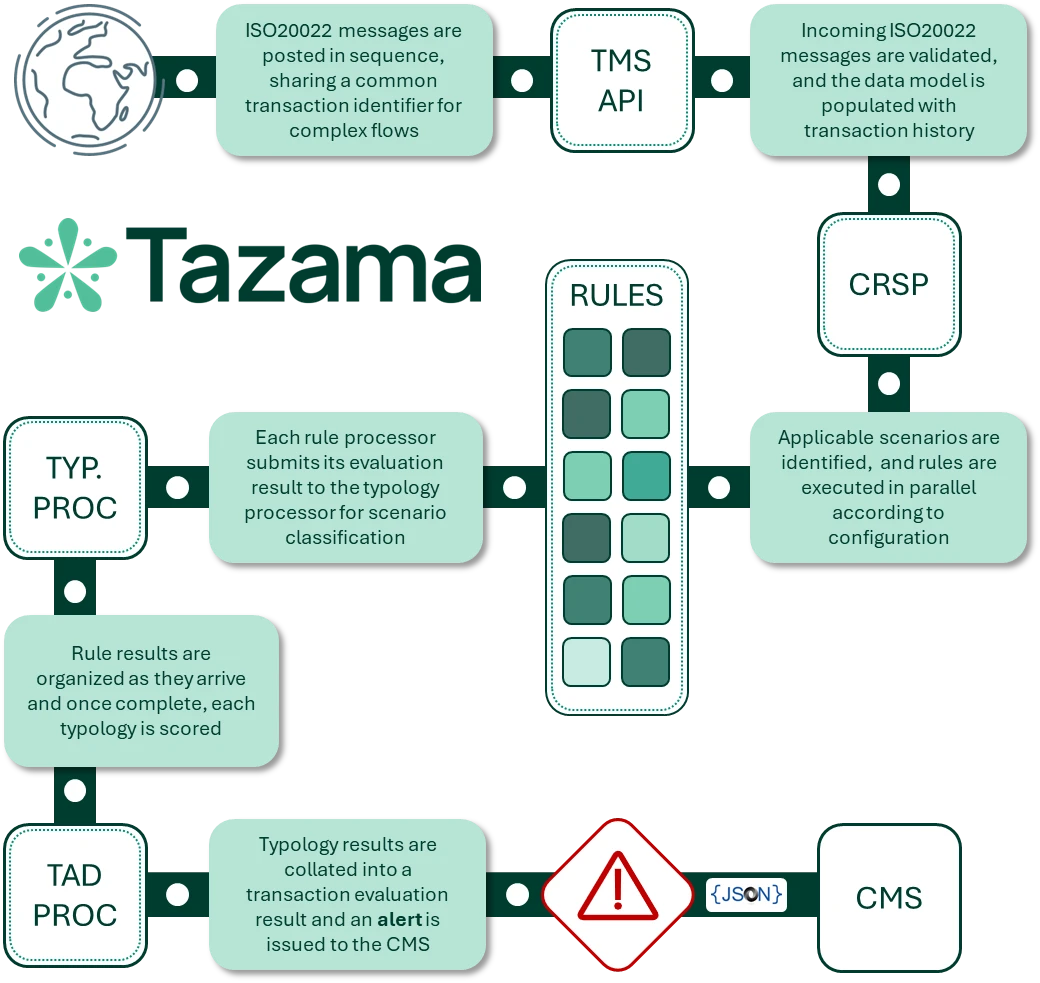
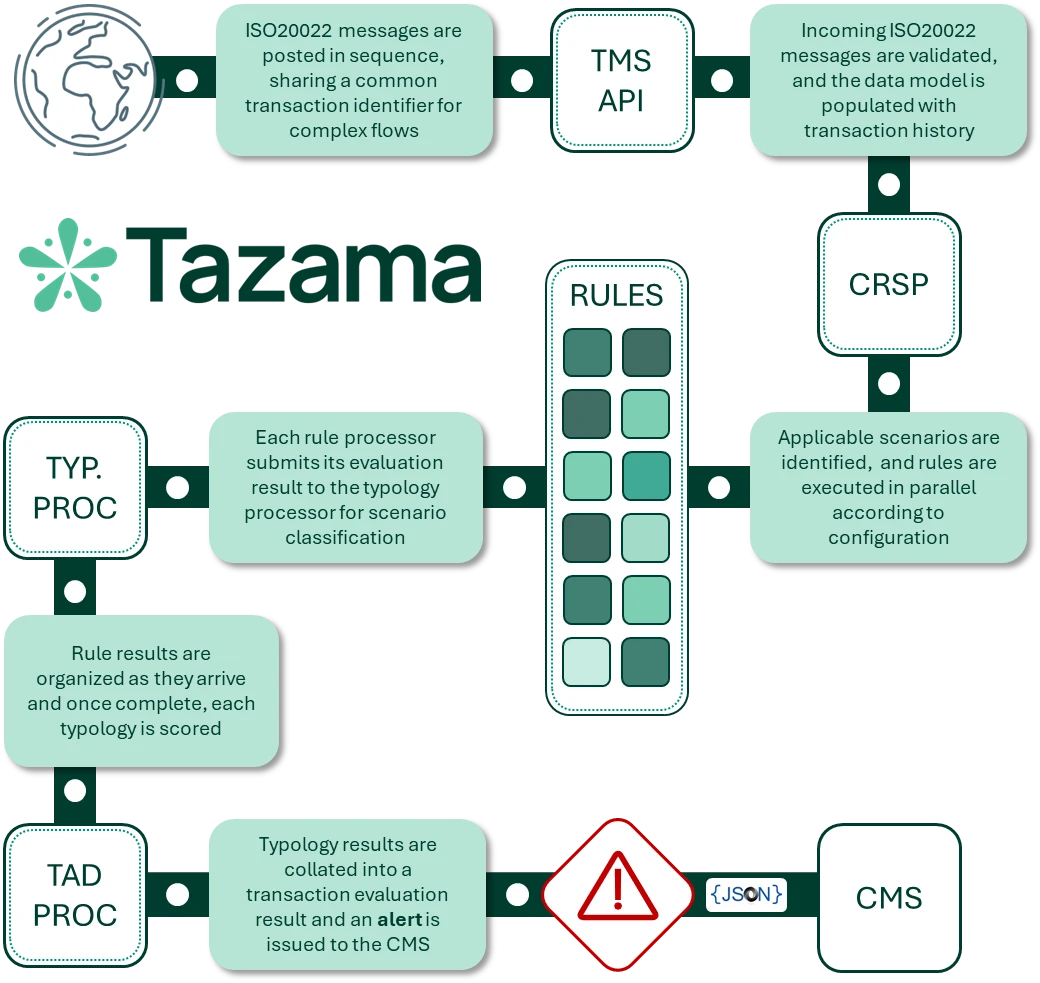
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in the approach to financial monitoring and compliance worldwide. Previously, the financial sector struggled with proprietary solutions that were both expensive and restrictive, impeding access and flexibility, particularly in developing economies. Tazama challenges this status quo […]
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in the approach to financial monitoring and compliance worldwide. Previously, the financial sector struggled with proprietary solutions that were both expensive and restrictive, impeding access and flexibility, particularly in developing economies. Tazama challenges this status quo […]
Mar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We’re all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let’s dispense with […]
Mar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We’re all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let’s dispense with […]
Email Security & Protection , Fraud Management & Cybercrime , Governance & Risk Management Joint Hornetsecurity-Vade Will Have More Geographic Reach, Microsoft 365 Protection Michael Novinson (MichaelNovinson) • March 5, 2024 Georges Lotigier, CEO, Vade (Image: Vade) Hornetsecurity purchased French email security vendor Vade to expand its geographic footprint and protection capabilities around […]
Email Security & Protection , Fraud Management & Cybercrime , Governance & Risk Management Joint Hornetsecurity-Vade Will Have More Geographic Reach, Microsoft 365 Protection Michael Novinson (MichaelNovinson) • March 5, 2024 Georges Lotigier, CEO, Vade (Image: Vade) Hornetsecurity purchased French email security vendor Vade to expand its geographic footprint and protection capabilities around […]
DTEX Systems, a San Jose, CA-based insider risk management company, raised $50M in Series E funding. The round, which brought the total amount to $138M, was led by CapitalG. In conjunction with the funding, James Luo, partner at CapitalG who will be joining the DTEX board of directors. The company intends to use the funds […]
DTEX Systems, a San Jose, CA-based insider risk management company, raised $50M in Series E funding. The round, which brought the total amount to $138M, was led by CapitalG. In conjunction with the funding, James Luo, partner at CapitalG who will be joining the DTEX board of directors. The company intends to use the funds […]