The attackers utilized typosquatting and code modifications to trick developers into installing malicious packages and continuously refined their techniques to evade detection.
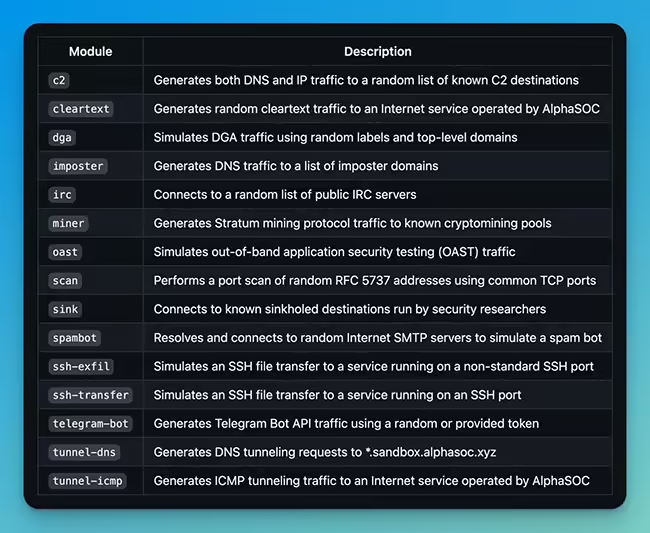
Network Flight Simulator is a lightweight utility that generates malicious network traffic and helps security teams evaluate security controls and network visibility. The tool performs tests to simulate DNS tunneling, DGA traffic, requests to known active C2 destinations, and other suspicious traffic patterns. “There’s so much snake oil within the security industry regarding threat detection […]
Nansen stopped the malicious activity shortly after the affected vendor informed them about the incident, but the ensuing investigation confirmed that user data was compromised.
Key Points A malicious Python package, “Culturestreak”, hijacks system resources for unauthorized cryptocurrency mining. The malicious package utilizes obfuscated code and random filenames to evade detection. The code runs in an infinite loop, making it a relentless threat that continually exploits system resources. The malicious code originates from an active GitLab repository, underscoring the ongoing […]
Sep 21, 2023THNVulnerability / Exploit A malicious actor released a fake proof-of-concept (PoC) exploit for a recently disclosed WinRAR vulnerability on GitHub with an aim to infect users who downloaded the code with Venom RAT malware. “The fake PoC meant to exploit this WinRAR vulnerability was based on a publicly available PoC script that exploited […]
Malicious actors have stolen more than $1m in a ‘pig butchering’ cryptocurrency scam in just three months, researchers from Sophos have found. The highly sophisticated operation used a total of 14 domains and dozens of nearly identical fraud sites, according to the investigation. The attackers utilized fake trading pools of cryptocurrency from decentralized finance (DeFi) […]
Summary Netskope Threat Labs is tracking a campaign that uses malicious Python scripts to steal Facebook users’ credentials and browser data. This campaign targets Facebook business accounts with bogus Facebook messages with a malicious file attached. The attacks are reaching victims mainly in Southern Europe and North America across different segments, led by the manufacturing […]
Attackers are targeting 3D modelers and graphic designers with malicious versions of a legitimate Windows installer tool in a cryptocurrency-mining campaign that’s been ongoing since at least November 2021. The campaign abuses Advanced Installer, a tool for creating software packages, to hide malware in legitimate installers for software used by creative professionals — such as […]