ESET Research has discovered a cluster of malicious Python projects being distributed in PyPI, the official Python package repository. The threat targets both Windows and Linux systems and usually delivers a custom backdoor. In some cases, the final payload is a variant of the infamous W4SP Stealer, or a simple clipboard monitor to steal cryptocurrency, […]
Insider threats, including both malicious attacks and unintentional risks, are on the rise, with privilege escalation exploits being a significant component of unauthorized activity.
Dec 11, 2023NewsroomData Security / Mobile Security Cybersecurity researchers have discovered 18 malicious loan apps for Android on the Google Play Store that have been collectively downloaded over 12 million times. “Despite their attractive appearance, these services are in fact designed to defraud users by offering them high-interest-rate loans endorsed with deceitful descriptions, all while […]
Dec 05, 2023NewsroomMobile Security / Spyware A new “post-exploitation tampering technique” can be abused by malicious actors to visually deceive a target into believing that their Apple iPhone is running in Lockdown Mode when it’s actually not and carry out covert attacks. The novel method, detailed by Jamf Threat Labs in a report shared with […]
The attacks involve the use of weaponized documents with malicious macros that create a reverse shell, allowing the attackers to gain control over the compromised systems.
Nov 24, 2023NewsroomThreat Analysis / Dark Web More details have emerged about a malicious Telegram bot called Telekopye that’s used by threat actors to pull off large-scale phishing scams. “Telekopye can craft phishing websites, emails, SMS messages, and more,” ESET security researcher Radek Jizba said in a new analysis. The threat actors behind the operation […]
Our investigations on potential security threats uncovered a malicious Google Chrome extension that we named “ParaSiteSnatcher.” The ParaSiteSnatcher framework allows threat actors to monitor, manipulate, and exfiltrate highly sensitive information from multiple sources. ParaSiteSnatcher also utilizes the powerful Chrome Browser API to intercept and exfiltrate all POST requests containing sensitive account and financial information before […]
Microsoft has uncovered a supply chain attack by North Korean hackers who attached a malicious file to a legitimate photo and video editing application installer. In a blog on Wednesday, Microsoft Threat Intelligence said it attributed the activity to a group it calls Diamond Sleet — a hacking group within the North Korean government that […]
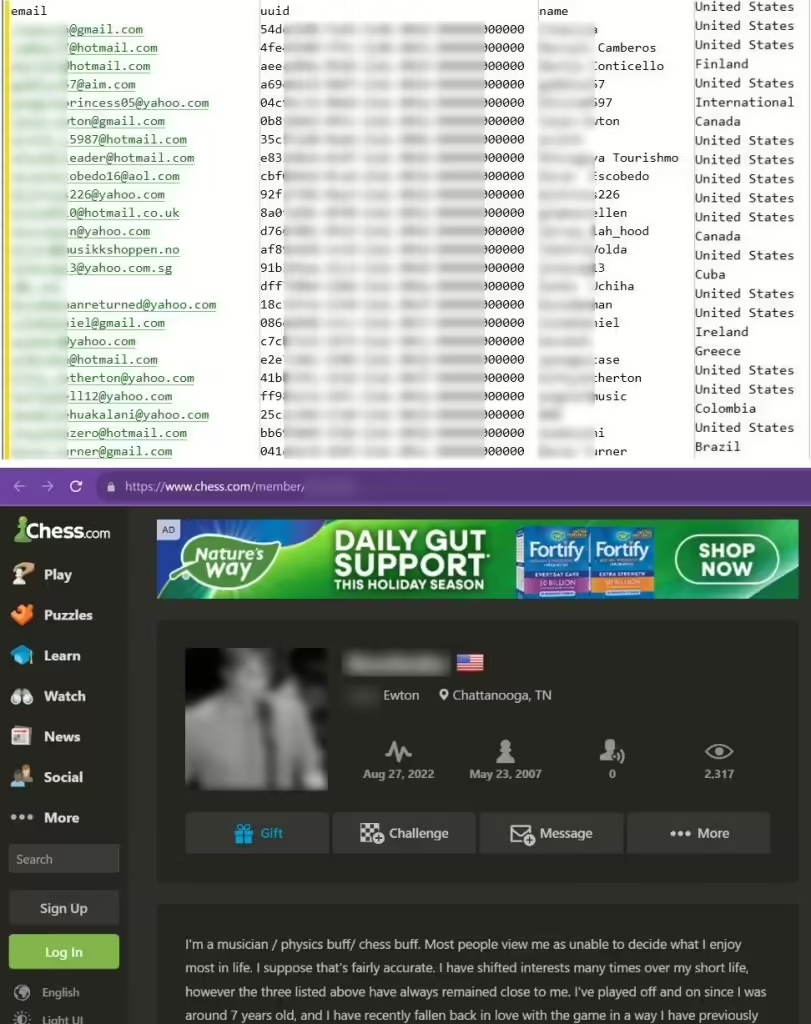
Earlier, Chess.com confirmed to Hackread.com that malicious threat actors exploited the “find friends” feature in the platform’s API to extract publically available user data. On November 10th, 2023, Hackread.com exclusively reported that threat actors had disclosed a scraped database containing information from Chess.com users. The database, containing approximately 828,327 users, was leaked on the notorious […]