We have tested several other outdoor security cameras. These are the ones we like that just missed out on a place above. Arlo Essential Wireless Security Camera for $50: This is the most affordable way to try Arlo’s wares, and it’s a solid security camera. Setup is a breeze, the 1080p footage is clear, and […]
Cold-brew makers aren’t like coffee machines. They don’t push steam through a tight puck of coffee grounds or heat water to drip over them. Most cold-brew makers are simple devices, and that’s because cold-brewing coffee is a deceptively simple process. We don’t actually need a cold-brew maker to do much. We don’t want it to […]
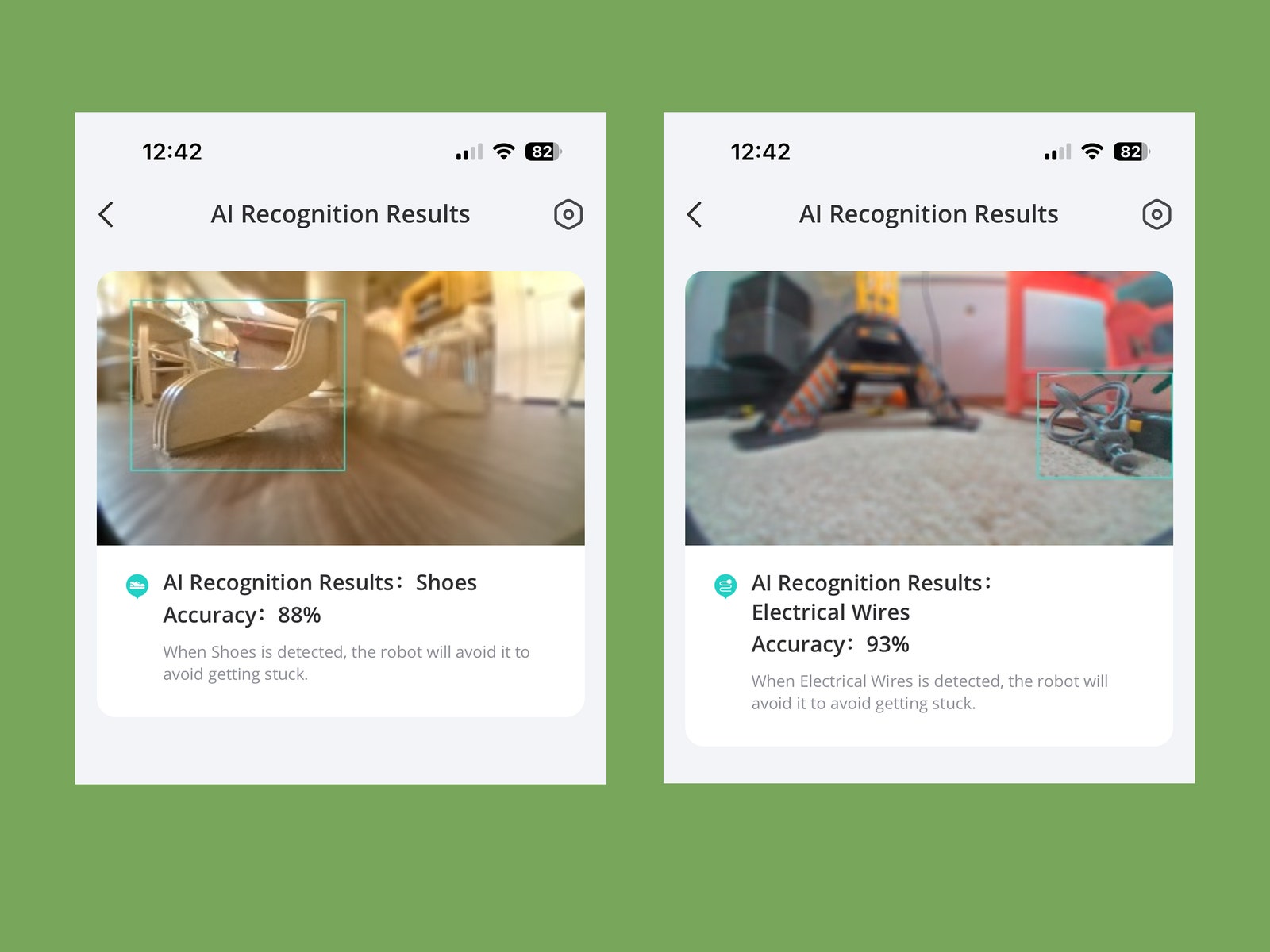
Like last year’s model, it also meets the TÜV Rheinland privacy and security certification. This is important, because it navigates via AI.See—a “visual recognition technology.” Basically, it uses a camera to steer around your house. It’s not upward-facing, and Eufy assures its customers that the photos are not stored in a server and are deleted […]
Chinese and Russian hackers have turned their focus to edge devices — like VPN appliances, firewalls, routers and Internet of Things (IoT) tools — amid a startling increase in espionage attacks, according to Google security firm Mandiant. The company published the findings as part of its annual report on cyber investigations Mandiant was involved in […]
Network security appliances like firewalls are meant to keep hackers out. Instead, digital intruders are increasingly targeting them as the weak link that lets them pillage the very systems those devices are meant to protect. In the case of one hacking campaign over recent months, Cisco is now revealing that its firewalls served as beachheads […]
We have tested some other routers we like and have several more in the queue. These aren’t as great as the picks above but are worth considering. Vodafone Pro II from £39 a month: Folks in the UK looking for a new internet service provider (ISP) should check out Vodafone’s Pro II. While ISPs have […]
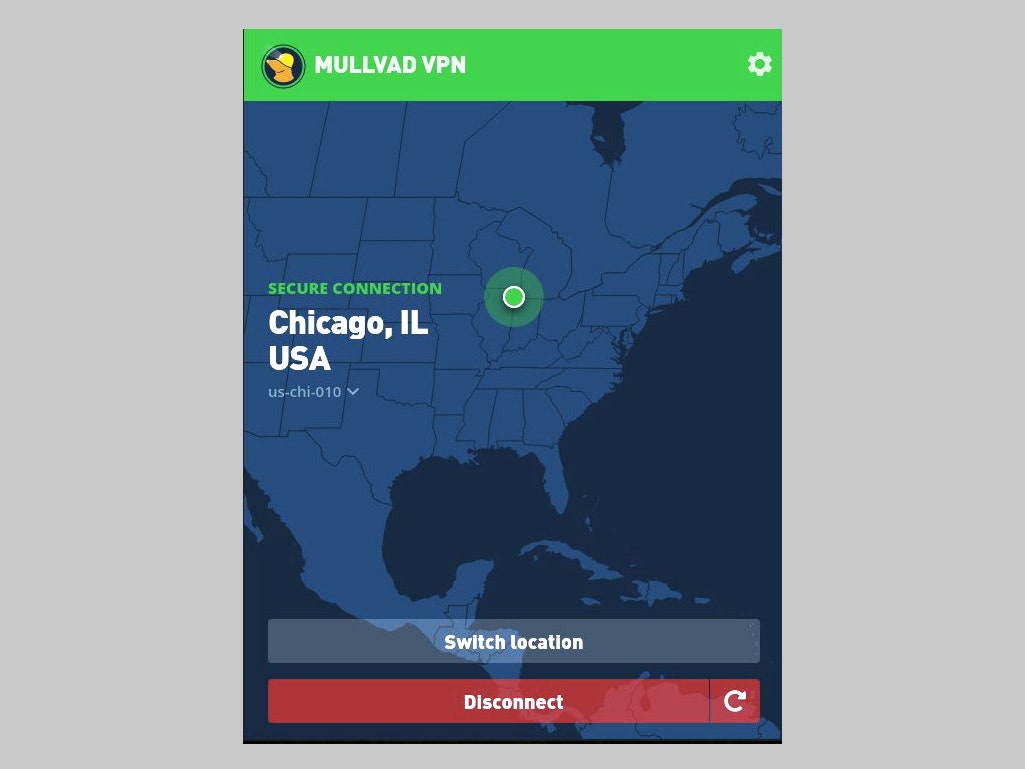
A virtual private network (VPN) is like a protective tunnel you can use to pass through a public network, protecting your data from outside eyes. Whether you’re worried about hiding your browsing activity from your internet service provider so it doesn’t sell your data to advertisers, or you want to stay safe on a public […]
PikaBot, along with other malicious loaders like QBot and DarkGate, heavily depends on spam campaigns for distribution. Its initial access strategies are intricately crafted, utilizing geographically targeted spam emails for specific countries.
The breach resulted in the theft of various sensitive information, including government identification like Medicare cards, driving licenses, passports, and tax file numbers.