In a result of its research investigation efforts, Security Explorations, a research lab of AG Security Research company, conducted security analysis of Microsoft Warbird and Protected Media Path technologies. This section of our website presents initial information regarding the project. Microsoft Warbird and Protected Media Path description Microsoft Protected Media Path (PMP) is a set […]
WASHINGTON – Today, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and the Office of the Director of National Intelligence (ODNI) released Securing Election Infrastructure Against the Tactics of Foreign Malign Influence Operations, a guidance document that details the latest tactics employed in foreign malign influence operations to shape U.S. policies, […]
A police investigation has been launched after MPs were apparently targeted in a “spear-phishing” attack, in what security experts believe could be an attempt to compromise parliament. A police force said it had started an inquiry after receiving a complaint from an MP who was sent a number of unsolicited messages last month. Twelve people […]
During an Advanced Continual Threat Hunt (ACTH) investigation that took place in early December 2023, Trustwave SpiderLabs discovered Ov3r_Stealer, an infostealer distributed using Facebook advertising and phishing emails. SpiderLabs’ “Facebook Advertising Spreads Novel Malware Variant,” is an in-depth dive into Ov3r_Stealer, exposing what the Threat Hunt team learned about the threat actors, their techniques, tactics, […]
An investigation based on interviews, documents and forensic analysis reveals new evidence that the phones of some three dozen journalists, human rights advocates and lawyers in Jordan were infected with Pegasus spyware. In a report released Thursday, Access Now, a digital rights organization, joined forces with the Citizen Lab, a cybersecurity watchdog organization at the […]
Ransomware In this blog, we detail our investigation of the Kasseika ransomware and the indicators we found suggesting that the actors behind it have acquired access to the source code of the notorious BlackMatter ransomware. By: Emmanuel Panopio, Christian Jason Geollegue, Julius Keith Estrellado, Christian Alpuerto, Shawn Austin Santos, Emmanuel Roll, Rhio Manaog, Gerald Fernandez, […]
SUMMARY The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) are releasing this joint Cybersecurity Advisory (CSA) to disseminate known indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with threat actors deploying Androxgh0st malware. Multiple, ongoing investigations and trusted third party reporting yielded the IOCs and TTPs, […]
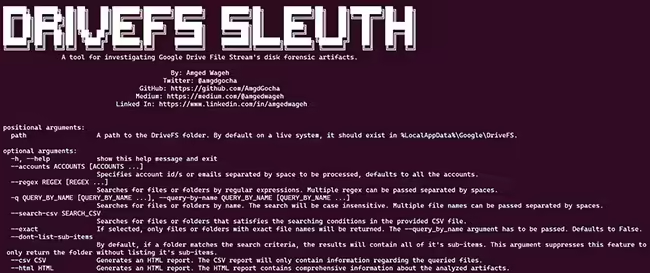
DriveFS Sleuth automates the investigation of Google Drive File Stream disk artifacts. The tool can parse the disk artifacts and build a filesystem tree-like structure enumerating the synchronized files along with their respective properties. “While engaged in a threat-hunting activity for a client to detect the misuse of file-syncing applications within their network, I identified […]
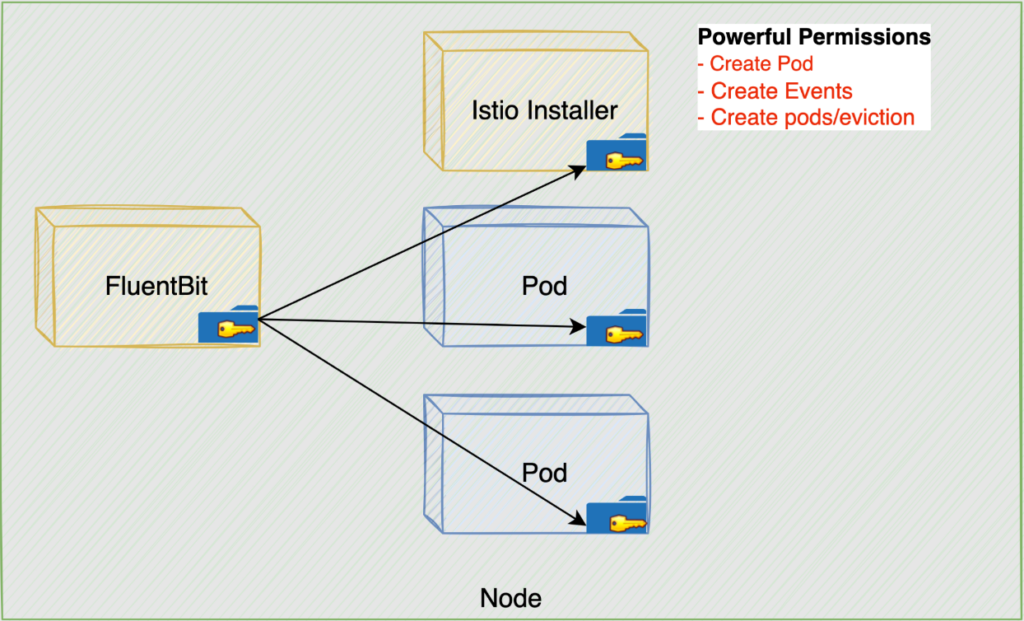
A recent Unit 42 investigation revealed a dual privilege escalation chain impacting Google Kubernetes Engine (GKE). This exploit chain arises from specific misconfigurations in GKE’s FluentBit logging agent and Anthos Service Mesh (ASM). When combined, these issues could provide attackers with existing Kubernetes cluster access an opportunity to escalate privileges. Kubernetes, a widely adopted open-source […]