In a move away from traditional phishing scams, attackers are increasingly exploiting vulnerabilities in computer systems to gain initial network access, according to Mandiant’s M-Trends 2024 Report. In 2023, attackers gained initial access through exploiting vulnerabilities in 38% of intrusions, a 6% increase from the previous year. Mandiant also found phishing’s prevalence declined from 22% […]
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing to touch the endpoint or conventional networked systems and services. Before getting into the details of the attack techniques being used, let’s discuss why these attacks are becoming more […]
As development environments grow more complex, applications increasingly communicate with many external services. When a software development project communicates with an external service, it utilizes a token or “secret” for authentication. These tokens are the glue that keeps any modern application together, and there is a staggering volume and variety of them in code today. […]
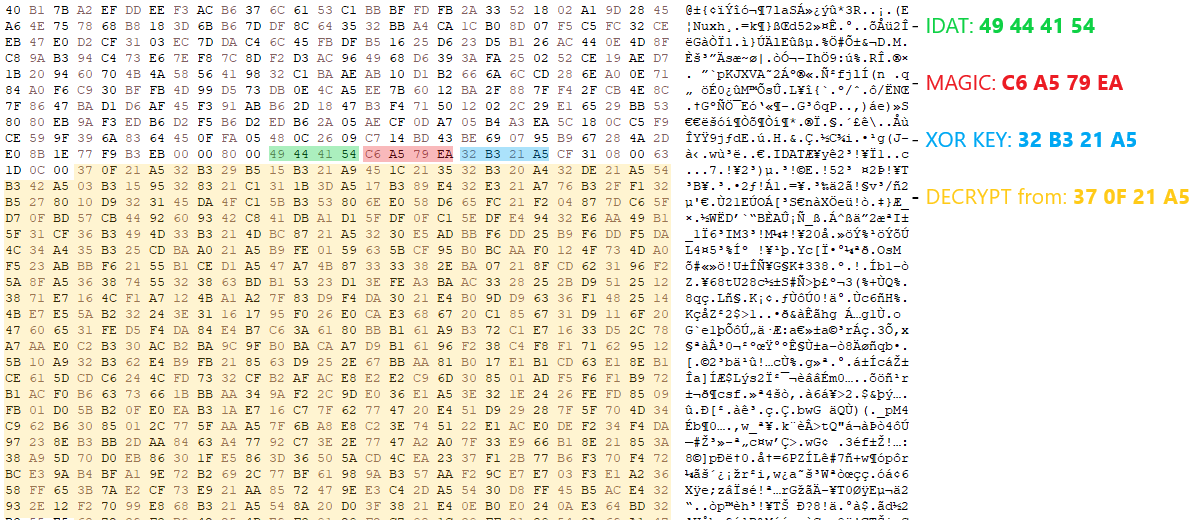
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its complexity and defense evasion CrowdStrike detects this new HijackLoader variant using machine learning and behavior-based detection capabilities CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion […]
Working at the speed of digital business is a constant challenge. But in today’s increasingly automated operational environment, crypto agility—i.e., an organization’s ability to (at the moment of compromise) switch rapidly and seamlessly between certificate authorities, encryption standards and keys and certificates with minimal disruption to one’s digital infrastructure—becomes essential to business. Crypto agility is […]
Hackers are increasingly targeting verified Twitter accounts of businesses and government organizations to promote cryptocurrency scams and steal assets from unsuspecting users.
Managing and allocating budgets for cybersecurity and IT has become an increasingly critical aspect of organizational strategy. Organizations recognize the need to invest significantly in cybersecurity to safeguard sensitive data, protect against ransomware attacks, and ensure the integrity of their IT infrastructure. A well-structured cybersecurity budget is crucial for staying ahead of emerging threats and […]
Dec 20, 2023NewsroomNetwork Security / Data Breach Ransomware groups are increasingly switching to remote encryption in their attacks, marking a new escalation in tactics adopted by financially motivated actors to ensure the success of their campaigns. “Companies can have thousands of computers connected to their network, and with remote ransomware, all it takes is one […]
Dec 19, 2023The Hacker NewsSoftware Security / Threat intelligence Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands via git commit messages. “Malware authors occasionally place their samples in services like Dropbox, Google Drive, OneDrive, and Discord to host second stage malware […]
- 1
- 2