Threat actors use pentesting tools to identify vulnerabilities and weaknesses in target systems or networks. These tools provide a simulated environment for testing potential attack vectors that allow threat actors to exploit security gaps and gain unauthorized access. By using pentesting tools, threat actors can assess the effectiveness of their methods and refine their strategies […]
The Joint Ransomware Task Force aims to enhance collaboration to identify ransomware groups and drive a comprehensive government and societal response to protect critical infrastructure and businesses.
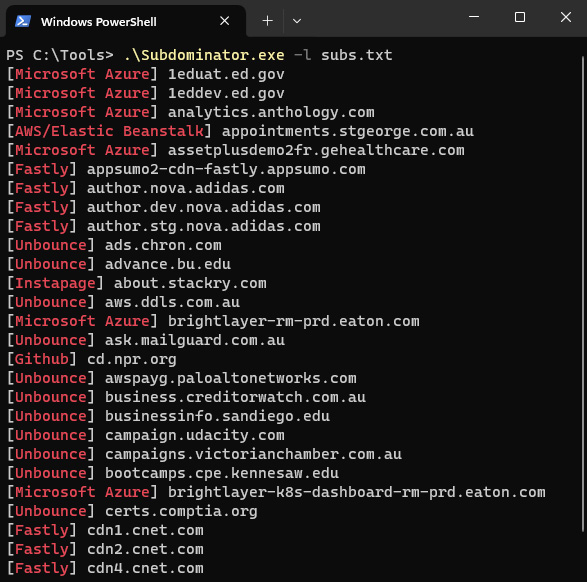
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools. “Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or features. […]
Lumu, a startup that helps enterprises identify and isolate security compromises, today announced that it raised $30 million in a Series B round led by Forgepoint Capital, $6 million of which is debt. Ricardo Villadiego, Lumu’s founder and CEO, says that the new cash will be put toward growing Lumu’s sales team in the U.S., […]
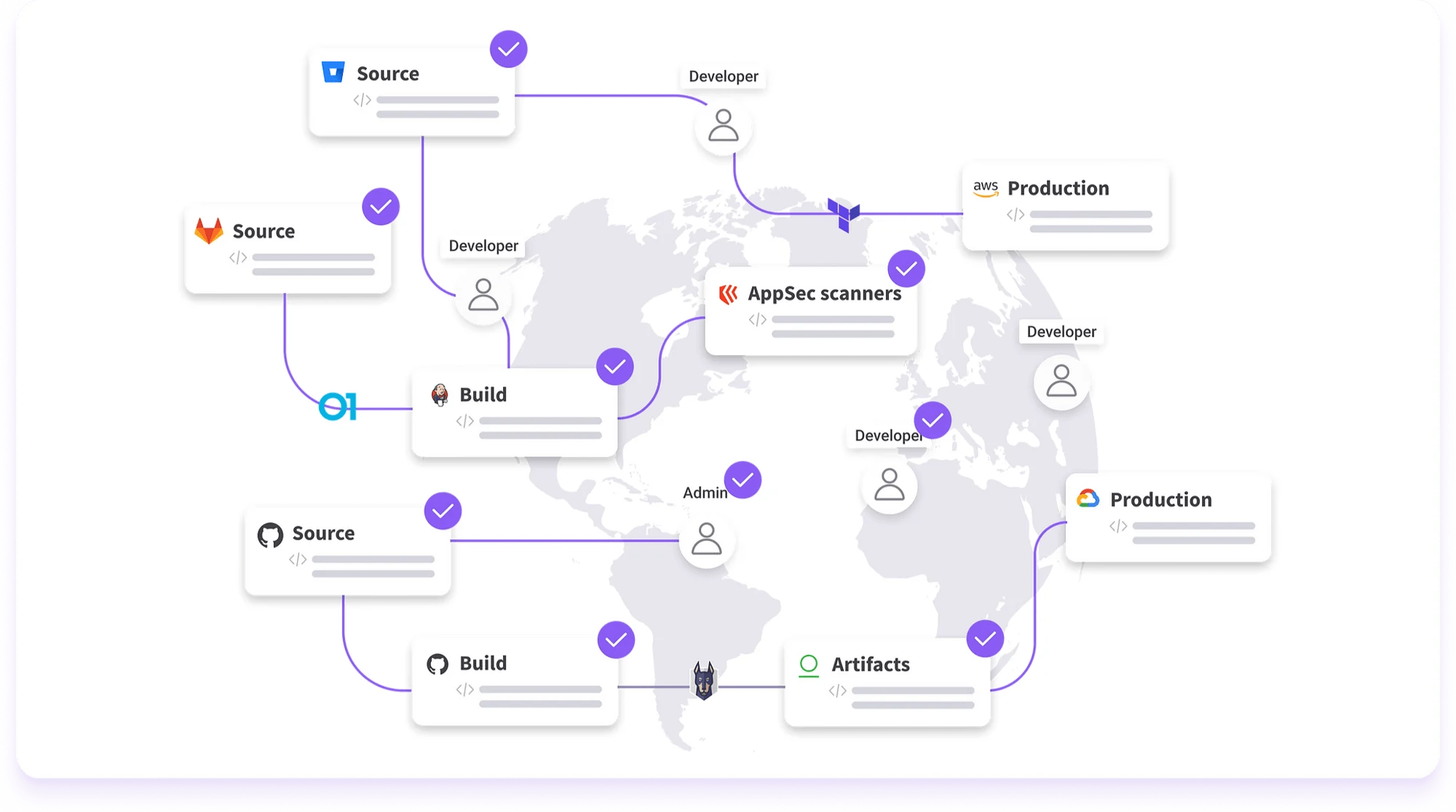
Legit Security, a cybersecurity company developing a platform to identify app vulnerabilities from code, has raised $40 million in a Series B funding round led by CRV with participation from Cyberstarts, Bessemer Venture Partners and TCV. Co-founder and CEO Roni Fuchs says that the funds, which bring Legit’s total raised to $77 million, will be […]