This post is also available in: 日本語 (Japanese) Executive Summary Unit 42 has identified malicious Chinese APT infrastructure masquerading as cloud backup services. Monitoring telemetry associated with two prominent Chinese APT groups, we observed network connections predominately originating from the country of Cambodia, including inbound connections originating from at least 24 Cambodian government organizations. We […]
VMware Carbon Black’s Threat Analysis Unit (TAU) has identified dozens of previously unknown vulnerable kernel drivers that could be exploited by attackers to alter firmware or escalate privileges. It’s not uncommon for threat actors, including cybercriminals and state-sponsored groups, to abuse kernel drivers in their operations. Such drivers can allow malicious hackers to manipulate system […]
Researchers have identified an ongoing cryptojacking campaign, EleKtra-Leak, that targets exposed Identity and Access Management (IAM) credentials on GitHub repositories. The campaign has been active since December 2020, with as many as 474 unique Amazon EC2 instances found being used to mine Monero cryptocurrency between August 30 and October 6. Moreover, threat actors use these […]
What happened Proofpoint researchers identified TA571 delivering the Forked variant of IcedID in two campaigns on 11 and 18 October 2023. Both campaigns included over 6,000 messages, each impacting over 1,200 customers in a variety of industries globally. Emails in the campaigns purported to be replies to existing threads. This is known as thread hijacking. […]
ReversingLabs has identified connections between a malicious campaign that was recently discovered and reported by the firm Phylum and several hundred malicious packages published to the NuGet package manager since the beginning of August. The latest discoveries are evidence of what seems to be an ongoing and coordinated campaign. Furthermore, ReversingLabs research shows how malicious […]
Oct 04, 2023THNMobile Security / Spyware New findings have identified connections between an Android spyware called DragonEgg and another sophisticated modular iOS surveillanceware tool named LightSpy. DragonEgg, alongside WyrmSpy (aka AndroidControl), was first disclosed by Lookout in July 2023 as a strain of malware capable of gathering sensitive data from Android devices. It was attributed […]
ReversingLabs researchers have identified a new, malicious supply chain attack affecting the npm platform. The “typosquatting” campaign first appeared in August and pushed a malicious package, node-hide-console-windows, which downloaded a Discord bot that facilitated the planting of an open source rootkit, r77. This is the first time ReversingLabs researchers have discovered a malicious open source […]
Key Takeaways Proofpoint identified a new malware called ZenRAT being distributed via fake installation packages of the password manager Bitwarden. The malware is specifically targeting Windows users and will redirect people using other hosts to a benign webpage. At this time, it is unknown how the malware is being distributed. The malware is a modular […]
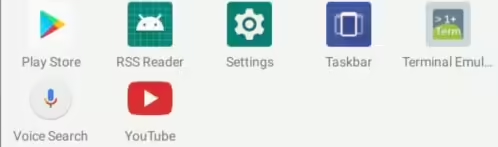
Executive Summary SentinelLabs identified three Android application packages (APK) linked to Transparent Tribe’s CapraRAT mobile remote access trojan (RAT). These apps mimic the appearance of YouTube, though they are less fully featured than the legitimate native Android YouTube application. CapraRAT is a highly invasive tool that gives the attacker control over much of the data […]