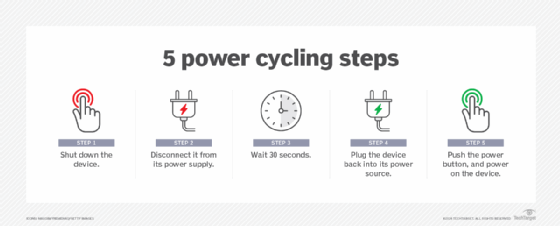
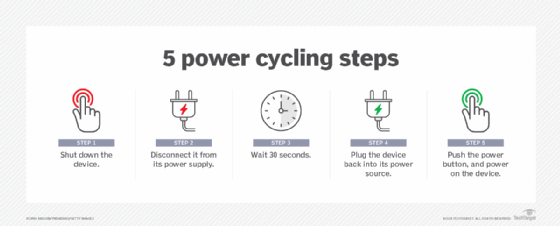
What is power cycling? Power cycling is the process of turning hardware off and then turning it on again. In the data center, technicians use power cycling to test the durability and reliability of network components. It is commonplace for servers to operate for months or even years without a reboot or disruption. These long […]
What is power cycling? Power cycling is the process of turning hardware off and then turning it on again. In the data center, technicians use power cycling to test the durability and reliability of network components. It is commonplace for servers to operate for months or even years without a reboot or disruption. These long […]
Operational Technology (OT) refers to the hardware and software used to change, monitor, or control the enterprise’s physical devices, processes, and events. Unlike traditional Information Technology (IT) systems, OT systems directly impact the physical world. This unique characteristic of OT brings additional cybersecurity considerations not typically present in conventional IT security architectures. The convergence of […]
What is RAM (random access memory)? Random access memory (RAM) is the hardware in a computing device that provides temporary storage for the operating system (OS), software programs and any other data in current use so they’re quickly available to the device’s processor. RAM is often referred to as a computer’s main memory, as opposed […]
The code embedded inside devices that bridges interactions between hardware and software is frequently exposed to security vulnerabilities, but lawmakers and federal officials have not paid enough attention to them, a national security think tank analysis argues. The report, released Wednesday by the Foundation for Defense of Democracies, contends that firmware vulnerabilities remain largely unaddressed, […]
Dec 28, 2023NewsroomSpyware / Hardware Security The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections erected by the company. Russian cybersecurity firm Kaspersky, which discovered the campaign at the beginning of 2023 after becoming one of the targets, described it as […]
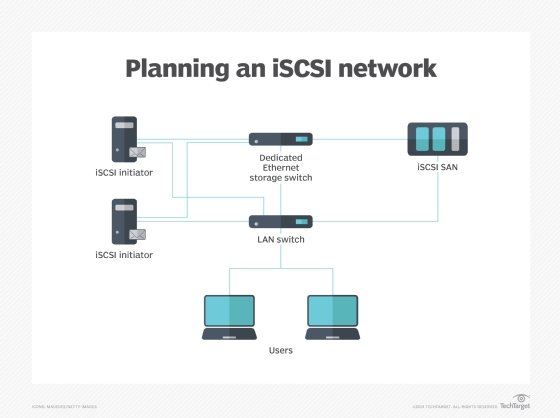
What is an iSCSI initiator? An Internet Small Computer System Interface initiator is software or hardware that lets a host computer send data to an external iSCSI-based storage array through an Ethernet network adapter over a TCP-based IP network. ISCSI is a protocol for sharing block storage and communicating with input/output (I/O) devices over a TCP/IP network. […]
Server hardware vendors offer servers of all shapes and sizes, providing a wide range of options for organizations. Most of the major players include rack servers in their inventories, but many also provide blade servers. And some even offer mainframe computers. Server hardware vendors usually offer other types of systems, such as towers, converged infrastructures, […]
Lenovo has introduced new hardware to support its hybrid cloud platform for AI, giving customers added performance for enterprise workloads. Lenovo’s new AI-focused hyperconverged appliances include ThinkAgile VX with VMware Cloud Foundation reference architecture, ThinkAgile MX450 Edge Integrated System and the ThinkAgile HX1021 AI for the Edge with Nutanix. The vendor also released ThinkSystem SR650 […]