Follow this real-life network attack simulation, covering 6 steps from Initial Access to Data Exfiltration. See how attackers remain undetected with the simplest tools and why you need multiple choke points in your defense strategy. Surprisingly, most network attacks are not exceptionally sophisticated, technologically advanced, or reliant on zero-day tools that exploit edge-case vulnerabilities. Instead, […]
President Joe Biden signed a bill on Wednesday that could ban TikTok from operating within the United States as early as next year. After years of trying, the US House of Representatives and the Senate managed to pass a measure that would force TikTok to divest from ByteDance, its Chinese owner, within a year, or […]
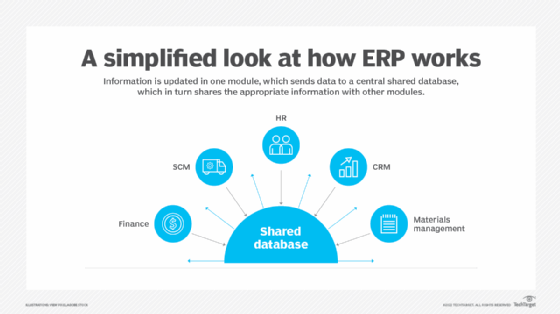
What is Electronic Data Interchange (EDI)? Electronic Data Interchange (EDI) is the transfer of data from one computer system to another by standardized message formatting without the need for human intervention. The goal of EDI is to replace manual processes that involve the exchange of documents with a fully autonomous one. EDI permits multiple companies […]
What is Electronic Data Interchange (EDI)? Electronic Data Interchange (EDI) is the transfer of data from one computer system to another by standardized message formatting without the need for human intervention. The goal of EDI is to replace manual processes that involve the exchange of documents with a fully autonomous one. EDI permits multiple companies […]
In a move away from traditional phishing scams, attackers are increasingly exploiting vulnerabilities in computer systems to gain initial network access, according to Mandiant’s M-Trends 2024 Report. In 2023, attackers gained initial access through exploiting vulnerabilities in 38% of intrusions, a 6% increase from the previous year. Mandiant also found phishing’s prevalence declined from 22% […]
Scammers have been observed employing a sophisticated tactic to steal Toncoins (TON) from Telegram users globally. This scheme, uncovered by researchers at Kaspersky and described in a report published today, has been operational since November 2023 and exploits the growing popularity of both TON and the messaging platform Telegram. Targets from various regions have fallen […]
Q1 saw substantial shifts in activity from some of the most prolific Ransomware-as-a-Service (RaaS) groups, according to GuidePoint Security. RaaS groups attempt to recruit disaffected or displaced affiliates In addition to revealing a nearly 20% year-over-year increase in the number of ransomware victims, the GRIT Q1 2024 Ransomware Report observes major shifts in the behavioral […]
The malware does not try to hide its presence in the system from antivirus programs and has not gained much popularity in the underground yet, indicating that it is a new player in the market.
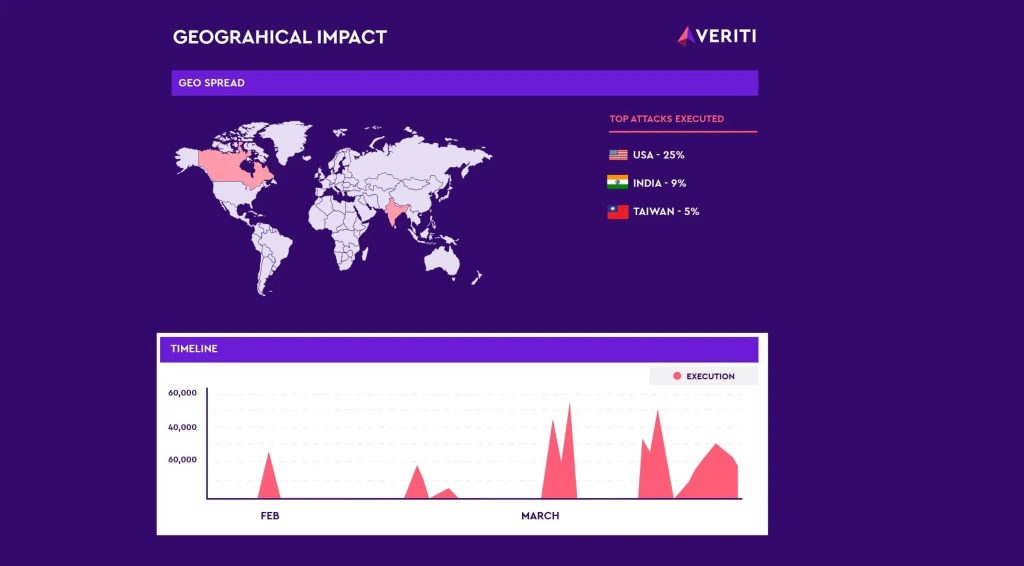
Veriti Research has discovered a surge in attacks from operators of the Androxgh0st malware family, uncovering over 600 servers compromised primarily in the U.S., India and Taiwan. According to Veriti’s blog post, the adversary behind Androxgh0st had their C2 server exposed, which could allow for a counterstrike by revealing the impacted targets. The researchers then […]