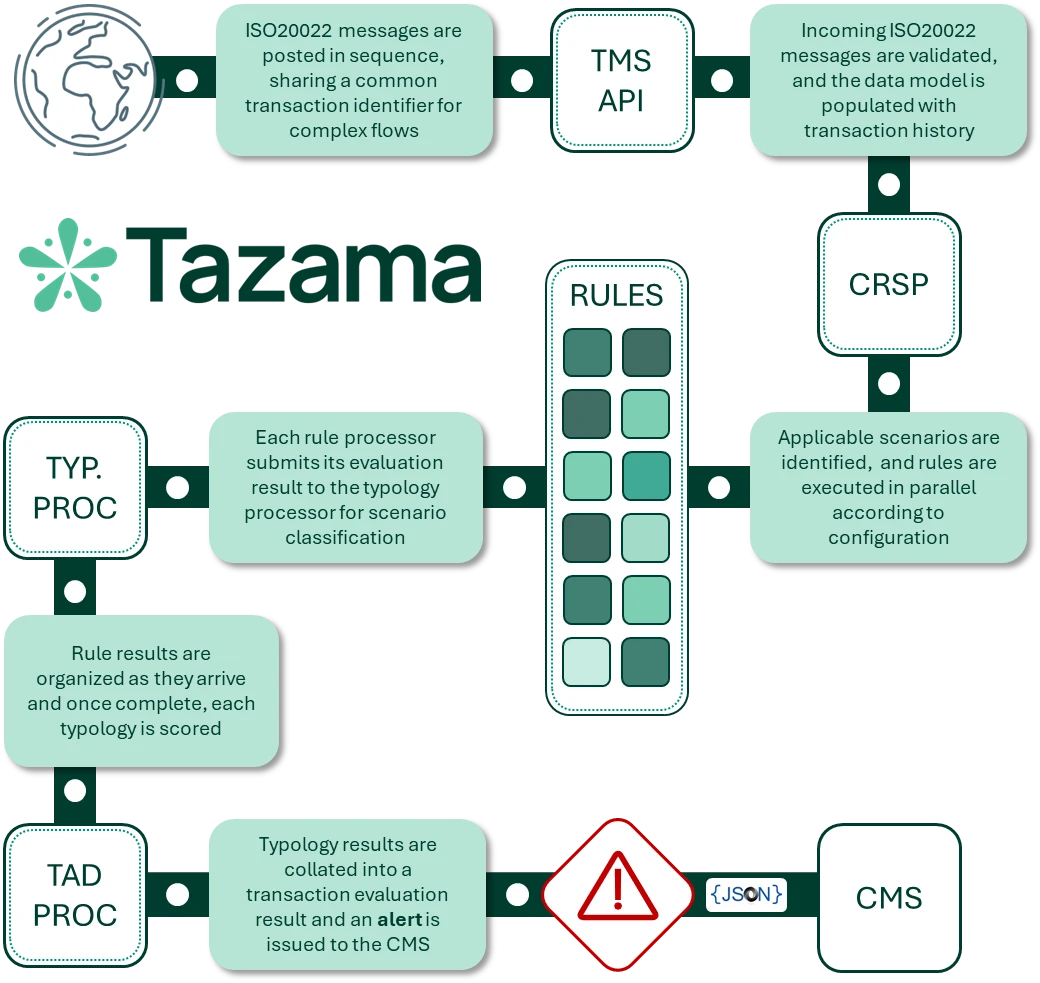
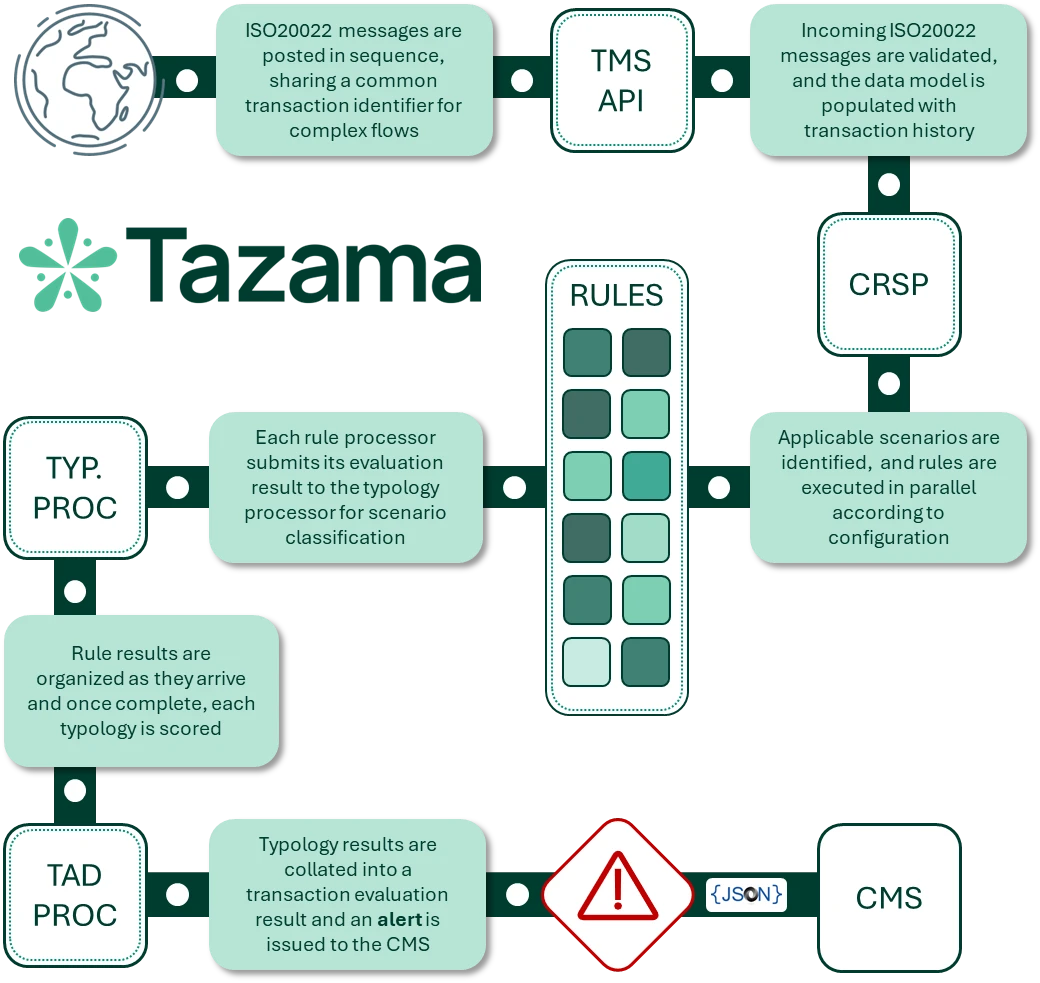
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in the approach to financial monitoring and compliance worldwide. Previously, the financial sector struggled with proprietary solutions that were both expensive and restrictive, impeding access and flexibility, particularly in developing economies. Tazama challenges this status quo […]
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in the approach to financial monitoring and compliance worldwide. Previously, the financial sector struggled with proprietary solutions that were both expensive and restrictive, impeding access and flexibility, particularly in developing economies. Tazama challenges this status quo […]
Developer-focused security company Snyk said it has acquired Helios, a startup focused on helping developers troubleshoot applications in runtime and production. The acquisition enhances Snyk’s “cloud-to-code risk visibility” by combining Helios’ full-stack runtime data collection and insights with the Snyk Developer Security Platform, Snyk said in a statement. While security testing, such as static analysis […]
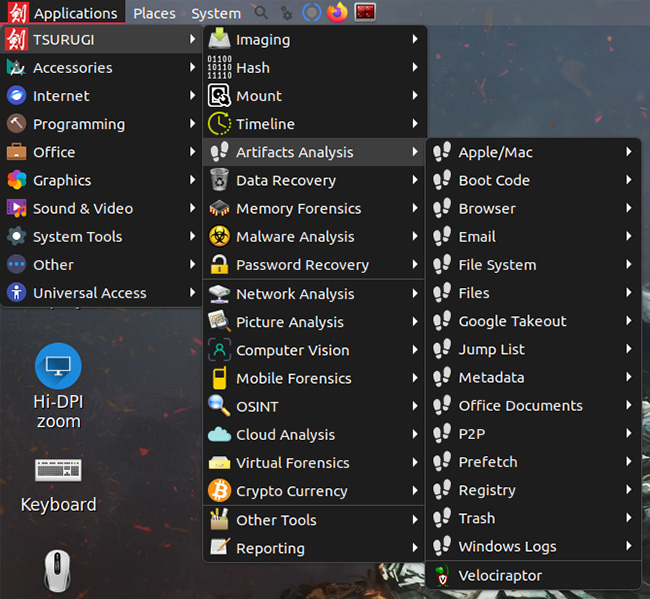
Tsurugi Linux is a heavily customized open-source distribution focused on supporting DFIR investigations. The project focuses mainly on live forensics analysis, post-mortem analysis, and digital evidence acquisition. Users can also perform malware analysis, OSINT and computer vision activities. “We’ve crafted a user-friendly experience, organizing the main menu in a logical forensic analysis sequence. Our menu […]
Google’s research team has launched v8CTF, a capture-the-flag (CTF) challenge focused on its Chrome browser’s V8 JavaScript engine. The competition opened on October 6, 2023, and is accessible to any exploit writers. “Once you have identified a vulnerability present in our deployed version, exploit it, and grab the flag,” Google software engineers Stephen Roettger and […]
Dive Brief: The Cybersecurity and Infrastructure Security Agency is sharply focused on threat activity tied to the People’s Republic of China as that country has become the top nation-state cyber adversary to the U.S. China is actively targeting more critical infrastructure, CISA Director Jen Easterly said Wednesday at the Secureworks Threat Intelligence Summit. China-linked threat […]