Apr 12, 2024NewsroomWeb Security / WordPress Cybersecurity researchers have discovered a credit card skimmer that’s concealed within a fake Meta Pixel tracker script in an attempt to evade detection. Sucuri said that the malware is injected into websites through tools that allow for custom code, such as WordPress plugins like Simple Custom CSS and JS […]
In a recent attack campaign, cybercriminals were discovered cleverly manipulating GitHub’s search functionality, and using meticulously crafted repositories to distribute malware. Key Points GitHub search manipulation: Attackers create malicious repositories with popular names and topics, using techniques like automated updates and fake stars to boost search rankings and deceive users. Malicious code is often hidden […]
Apr 10, 2024NewsroomCyber Crime / Malvertising Cybersecurity researchers have discovered a new Raspberry Robin campaign wave that propagates the malware through malicious Windows Script Files (WSFs) since March 2024. “Historically, Raspberry Robin was known to spread through removable media like USB drives, but over time its distributors have experimented with other initial infection vectors,” HP […]
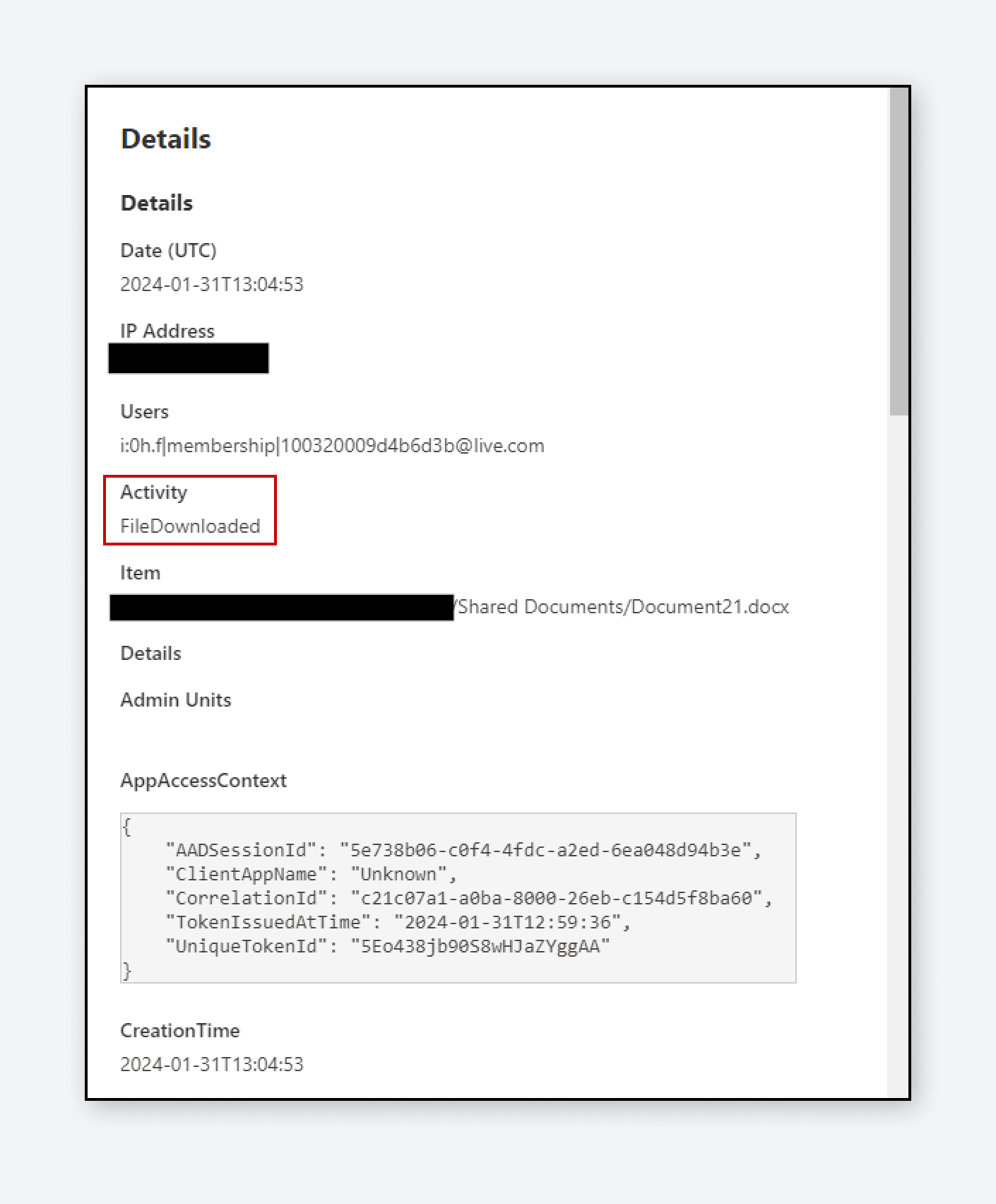
Varonis Threat Labs discovered two techniques in SharePoint that allow users to circumvent audit logs and avoid triggering download events while exfiltrating files. These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync […]
Cybersecurity researchers from Bitdefender discovered critical vulnerabilities in LG TVs running webOS versions 4 through 7. These vulnerabilities could allow attackers to gain complete control over the TV, steal data, or install malware. The vulnerabilities were identified by Bitdefender as part of their research into the security of popular IoT devices. They found that attackers […]
Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver a wide range of malware such as Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and a stealer that targets crypto wallets.
Apr 09, 2024NewsroomMalware / Cryptojacking Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver a wide range of malware such as Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and a stealer that targets crypto wallets. The email messages come with Scalable Vector Graphics (SVG) file attachments that, when clicked, […]
Martin Schobert at Swiss security firm Pentagrid discovered that an attacker could input a series of six consecutive dashes (——) in place of a booking reference number and the terminal would return an extensive list of room details.
Apr 08, 2024NewsroomCybercrime / Network Security Threat hunters have discovered a new malware called Latrodectus that has been distributed as part of email phishing campaigns since at least late November 2023. “Latrodectus is an up-and-coming downloader with various sandbox evasion functionality,” researchers from Proofpoint and Team Cymru said in a joint analysis published last week, […]