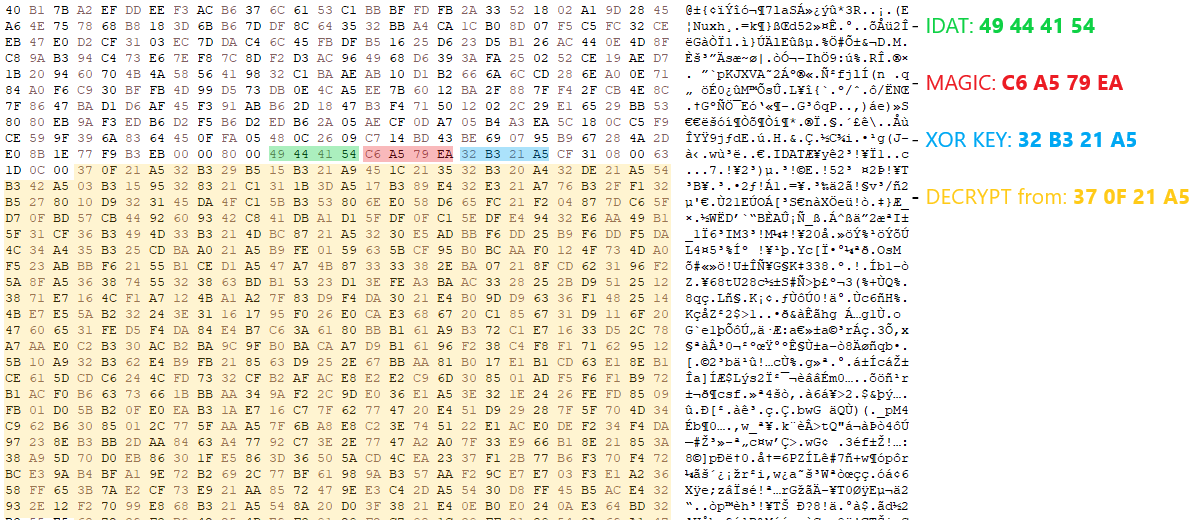
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its complexity and defense evasion CrowdStrike detects this new HijackLoader variant using machine learning and behavior-based detection capabilities CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion […]
Cybercriminals are targeting vulnerable Docker servers by deploying two containers: a standard XMRig miner and the 9Hits viewer application—an automated traffic exchange system. Cado Security researchers have discovered a new campaign targeting vulnerable Docker servers, deploying two containers – a regular XMRig miner and the 9hits viewer application. This is the first documented case of malware deploying the […]
It is speculated that the threat actors behind the attacks may be deploying an update to hide their presence, or a grey-hat hacker could be rebooting the devices to clear the implant.
Cybercriminals are now deploying ransomware within the first day of initially compromising their targets, a dramatic drop on the 4.5 days that the task had been taking last year, according to a new threat report. Cybersecurity company Secureworks warns that “2023 may be the most prolific year for ransomware attacks to date” with three times […]
Aiming to give users more flexibility in deploying mainframes, IBM delivered a new rack-mounted Z16 system containing the same capabilities of its standalone Z16, including AI inferencing and quantum-safe cryptography. The single-frame and rack-mounted designs of the new Z16, available with LinuxOne Rockhopper 4 options, makes the system more practical for space-constrained data centers and […]