Engineers have partially restored a 1970s-era computer on NASA’s Voyager 1 spacecraft after five months of long-distance troubleshooting, building confidence that humanity’s first interstellar probe can eventually resume normal operations. Several dozen scientists and engineers gathered Saturday in a conference room at NASA’s Jet Propulsion Laboratory, or connected virtually, to wait for a new signal […]
Researchers have developed a computer worm that targets generative AI (GenAI) applications to potentially spread malware and steal personal data. The new paper details the worm dubbed “Morris II,” which targets GenAI ecosystems through the use of adversarial self-replicating prompts, leading to GenAI systems delivering payloads to other agents. Once unleashed, the worm is stored […]
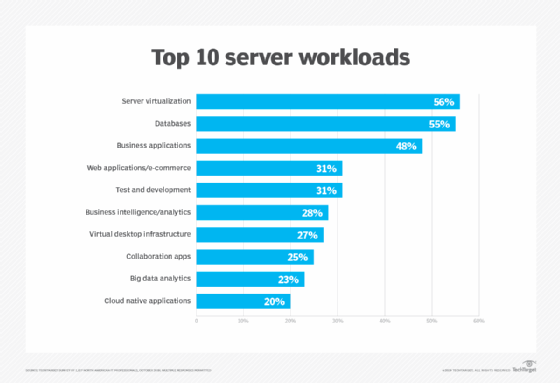
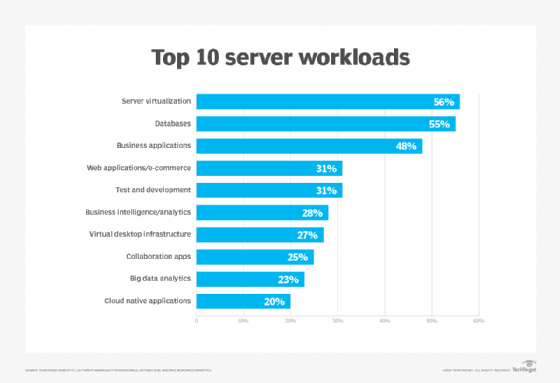
What is a workload? In computing, a workload is typically any program or application that runs on a computer. A workload can be a simple alarm clock or contact app running on a smartphone. Or it can be a complex enterprise application hosted on one or more servers with thousands of clients, or user systems […]
What is a workload? In computing, a workload is typically any program or application that runs on a computer. A workload can be a simple alarm clock or contact app running on a smartphone. Or it can be a complex enterprise application hosted on one or more servers with thousands of clients, or user systems […]
Feb 07, 2024NewsroomCyber Espionage / Network Security Chinese state-backed hackers broke into a computer network that’s used by the Dutch armed forces by targeting Fortinet FortiGate devices. “This [computer network] was used for unclassified research and development (R&D),” the Dutch Military Intelligence and Security Service (MIVD) said in a statement. “Because this system was self-contained, […]
Chinese state-sponsored hackers broke into an internal computer network used by the Dutch Ministry of Defence last year, the Netherlands said Tuesday. In a rare announcement, both the country’s military (MIVD) and civilian (AIVD) security services said the ministry had been hacked for espionage purposes after the threat actor exploited a vulnerability in FortiGate devices, […]
A cyberattack targeted a major Maine healthcare provider’s computer servers over the weekend, leading the company to temporarily take all of its patient records offline. Northern Light Health told News Center Maine that its patient records were not on the affected servers, but they took down all of their servers as a precaution while the […]
Feb 02, 2024NewsroomCryptojacking / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned that more than 2,000 computers in the country have been infected by a strain of malware called DirtyMoe. The agency attributed the campaign to a threat actor it calls UAC-0027. DirtyMoe, active since at least 2016, is capable of carrying […]
A team of computer scientists led by the University of Massachusetts Amherst recently announced a new method for automatically generating whole proofs that can be used to prevent software bugs and verify that the underlying code is correct. This new method, called Baldur, leverages the artificial intelligence power of LLMs, and, when combined with the […]