Apr 16, 2024NewsroomCloud Security / DevSecOps New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant risks to organizations. The vulnerability has been codenamed LeakyCLI by cloud security firm Orca. “Some commands on Azure CLI, AWS CLI, and […]
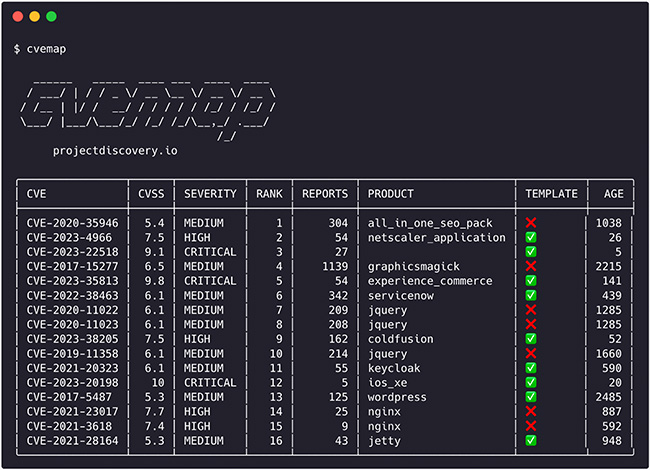
CVEMap is an open-source command-line interface (CLI) tool that allows you to explore Common Vulnerabilities and Exposures (CVEs). It’s designed to offer a streamlined and user-friendly interface for navigating vulnerability databases. Although CVEs are crucial for pinpointing and discussing security weaknesses, their rapid growth and occasional overstatement of severity often result in misleading information. Security […]
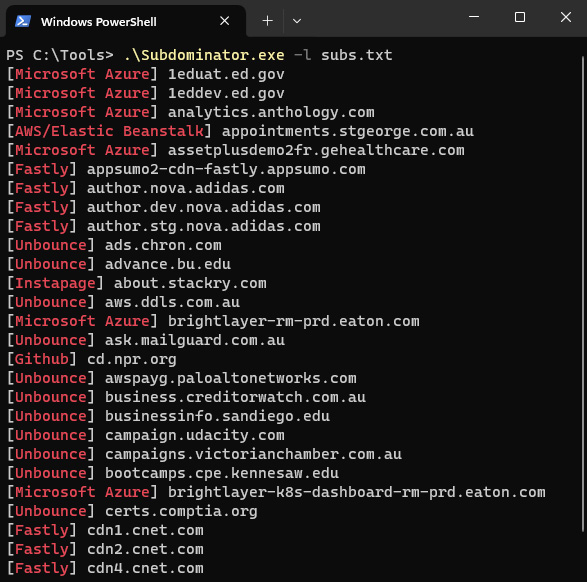
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools. “Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or features. […]
The Linux encryptor includes extensive command-line options for customization, allowing threat actors to specify exclusion and encryption criteria, as well as configure virtual machines that should not be encrypted.