A 54-year-old New Jersey woman has become the second living person to receive a genetically engineered pig kidney. The surgery, carried out at NYU Langone Health on April 12, also involved transplanting the pig’s thymus gland to help prevent rejection. The patient, Lisa Pisano, had a mechanical heart pump implanted days before getting the transplant. […]
Trust in cybersecurity tools has become one of the biggest challenges facing critical national infrastructure (CNI) providers as sophisticated nation-state attacks proliferate, according to a new report from Bridewell. The IT services firm’s latest Cyber Security in Critical National Infrastructure report is based on interviews with over 1000 CISOs and equivalent at CNI providers in […]
As cyber threats loom around every corner and privileged accounts become prime targets, the significance of implementing a robust Privileged Access Management (PAM) solution can’t be overstated. With organizations increasingly migrating to cloud environments, the PAM Solution Market is experiencing a transformative shift toward cloud-based offerings. One Identity PAM Essentials stands
Superusers Need Super Protection: How to Bridge Privileged Access Management and Identity Management
Feb 28, 2024The Hacker NewsZero Trust / Cyber Threat Traditional perimeter-based security has become costly and ineffective. As a result, communications security between people, systems, and networks is more important than blocking access with firewalls. On top of that, most cybersecurity risks are caused by just a few superusers – typically one out of 200 […]
Generative AI based on large language models (LLMs) has become a valuable tool for individuals and businesses, but also cybercriminals. Its ability to process large amounts of data and quickly generate results has contributed to its widespread adoption. AI in the hands of cybercriminals According to a report from Abnormal Security, generative AI (GenAI) is […]
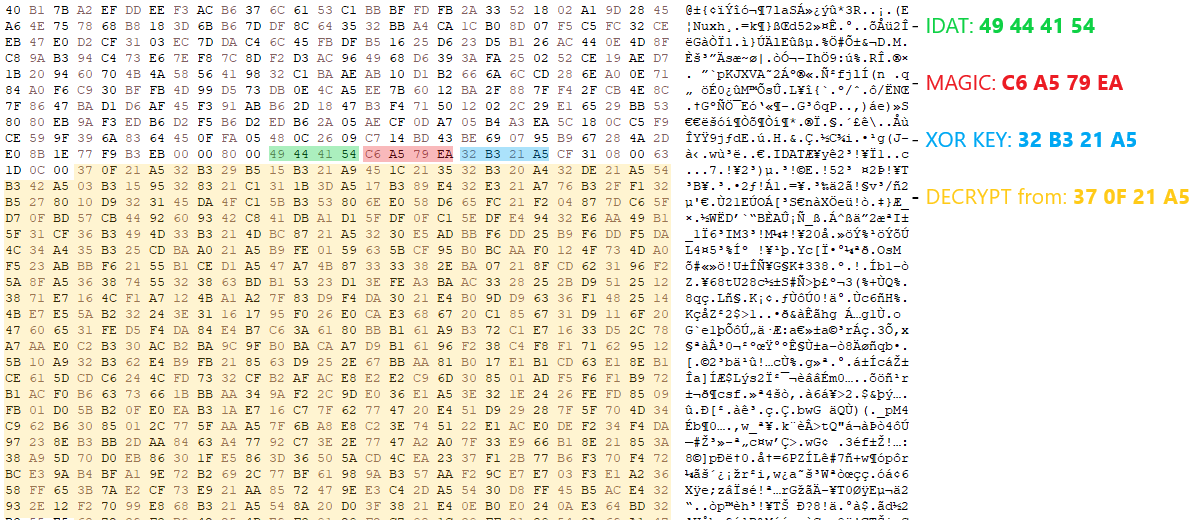
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its complexity and defense evasion CrowdStrike detects this new HijackLoader variant using machine learning and behavior-based detection capabilities CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion […]
The ransomware group known as Kasseika has become the latest to leverage the Bring Your Own Vulnerable Driver (BYOVD) attack to disarm security-related processes on compromised Windows hosts, joining the likes of other groups like Akira, AvosLocker, BlackByte, and RobbinHood. The tactic allows “threat actors to terminate antivirus processes and services for the deployment of […]
The expanding Southeast Asian casino industry has become the nexus of the region’s criminal ecosystem, including its cyber fraud industry, and it is facilitating large-scale money laundering by organized crime networks, a new United Nations report reveals. The money laundering includes the proceeds from online scams like pig-butchering schemes, where scammers develop a relationship with […]
Dive Brief: A cyber event — such as ransomware, data breaches and IT disruptions – has become the top concern for U.S. businesses, replacing business interruption, according to the annual Allianz Risk Barometer, released Tuesday. Cyber events are a leading global concern of businesses for the third-consecutive year, Allianz found. Business interruption and natural catastrophes […]