Backdoor Details – Binary Analysis Stage 1 injector The analysis in this blog is based on this ZIP archive: Advanced-ip-scanner.zip (SHA256:7966ee1ae9042e7345a55aa98ddeb4f39133216438d67461c7ee39864292e015). The ZIP archive contains two files: Advanced-ip-scanner.exe: A renamed copy of the legitimate Microsoft EXE oleview.exe. IVIEWERS.dll: A 22 MB DLL, which contains the stage two payload. This DLL is padded with an unused […]
Sandboxes are synonymous with dynamic malware analysis. They help to execute malicious files in a safe virtual environment and observe their behavior. However, they also offer plenty of value in terms of static analysis. See these five scenarios where a sandbox can prove to be a useful tool in your investigations. Detecting Threats in PDFs […]
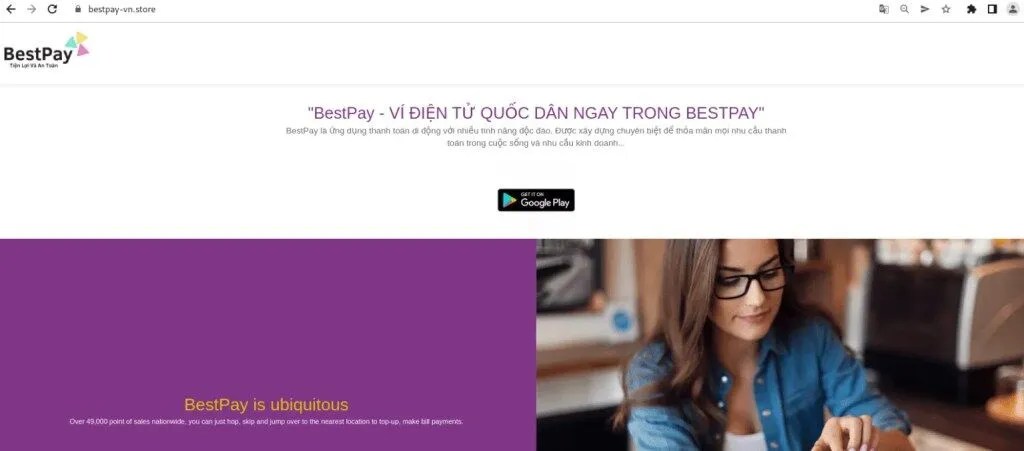
A recent analysis by Cyble has revealed a concerning escalation in the fake e-shop campaign, signaling a looming threat to banking security across various regions. Initially focused on Malaysian banks, this e-shop phishing campaign has now extended its reach to financial institutions in Vietnam and Myanmar. What sets this phishing campaign apart from others on […]
Technical Analysis The following analysis covers the technical characteristics of Case Study 1 and Case Study 2 for Tweaks. Case Study 1 1. BAT files establish webhooks: To start, once the user downloads the BAT file and executes it, the malware establishes the necessary webhook URLs using the Powershell commands below: “$payload = [PSCustomObject]@{ embeds […]
RiskInDroid (Risk Index for Android) is an open-source tool for quantitative risk analysis of Android applications based on machine learning techniques. How RiskInDroid works “A user should be able to quickly assess an application’s level of risk by simply glancing at RiskInDroid’s output, and they should be able to compare the app’s risk with others […]
Technical Analysis In this section, we provide a detailed analysis of each component of the attack chain initiated when a victim receives and clicks on the link within the PDF. PDF analysis The PDF file is a fake invitation to a wine-tasting event purported to take place at the Indian ambassador’s residence on February 2nd, […]
A recent analysis by Fortinet’s FortiGuard Labs has unveiled a sophisticated Python-based info-stealer distributed through a malicious Excel document. The attack exemplifies the innovative techniques cybercriminals employ to breach personal and organizational data. Diving into Details At the core of this campaign is the use of Excel 4.0 macros, a legacy feature that remains supported […]
An investigation based on interviews, documents and forensic analysis reveals new evidence that the phones of some three dozen journalists, human rights advocates and lawyers in Jordan were infected with Pegasus spyware. In a report released Thursday, Access Now, a digital rights organization, joined forces with the Citizen Lab, a cybersecurity watchdog organization at the […]
The 2023/2024 Axur Threat Landscape Report provides a comprehensive analysis of the latest cyber threats. The information combines data from the platform’s surveillance of the Surface, Deep, and Dark Web with insights derived from the in-depth research and investigations conducted by the Threat Intelligence team. Discover the full scope of digital threats in the Axur […]