With three different cameras, the Vantrue N4 allows you to get almost 360 degrees of video coverage for your car while you drive. The main camera records the road in front of your vehicle as well as the interior, while the second camera can be mounted on the back of your car to record behind […]
A security bug in the widely used Kubernetes container-management system allows attackers to remotely execute code with System privileges on Windows endpoints, potentially leading to full takeover of all Windows nodes within a Kubernetes cluster. Akamai security researcher Tomer Peled discovered the flaw, which is tracked as CVE-2023-5528 and has a CVSS score of 7.2. […]
The new DSLog backdoor allows threat actors to execute commands on compromised Ivanti servers remotely, and Orange Cyberdefense has confirmed its successful exploitation.
The flaw allows attackers to bypass authentication and access restricted resources on vulnerable devices. The exploitation volume is high, with over 170 distinct IP addresses attempting to exploit the vulnerability.
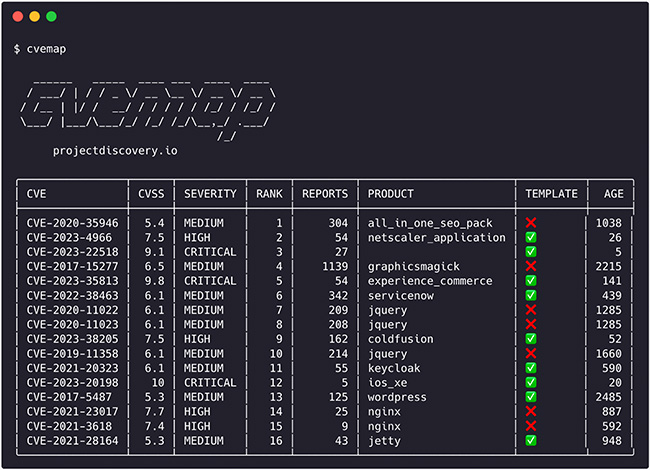
CVEMap is an open-source command-line interface (CLI) tool that allows you to explore Common Vulnerabilities and Exposures (CVEs). It’s designed to offer a streamlined and user-friendly interface for navigating vulnerability databases. Although CVEs are crucial for pinpointing and discussing security weaknesses, their rapid growth and occasional overstatement of severity often result in misleading information. Security […]
The vulnerability, tracked as CVE-2023-6933, allows unauthenticated attackers to inject a PHP object, potentially leading to code execution, data access, file manipulation, or denial of service.
iShutdown lightweight method allows to discover spyware infections on iPhones Pierluigi Paganini January 18, 2024 Researchers devised a “lightweight method,” called iShutdown, to determine whether Apple iOS devices have been infected with spyware. Cybersecurity researchers from Kaspersky have identified a “lightweight method,” called iShutdown, to identify the presence of spyware on Apple iOS devices. The method allow to discover […]
Apple fixed a bug in Magic Keyboard that allows to monitor Bluetooth traffic Pierluigi Paganini January 15, 2024 Apple addressed a recently disclosed Bluetooth keyboard injection vulnerability with the release of Magic Keyboard firmware. Apple released Magic Keyboard Firmware Update 2.0.6 to address a recently disclosed Bluetooth keyboard injection issue tracked as CVE-2024-0230. The flaw […]
The vulnerability, found in the software’s web-based management interface, allows attackers to execute commands on the underlying operating system by uploading arbitrary files.