Google announced it is updating the client-side encryption mechanism for Google Meet to allow external participants, including those without Google accounts, to join encrypted calls.
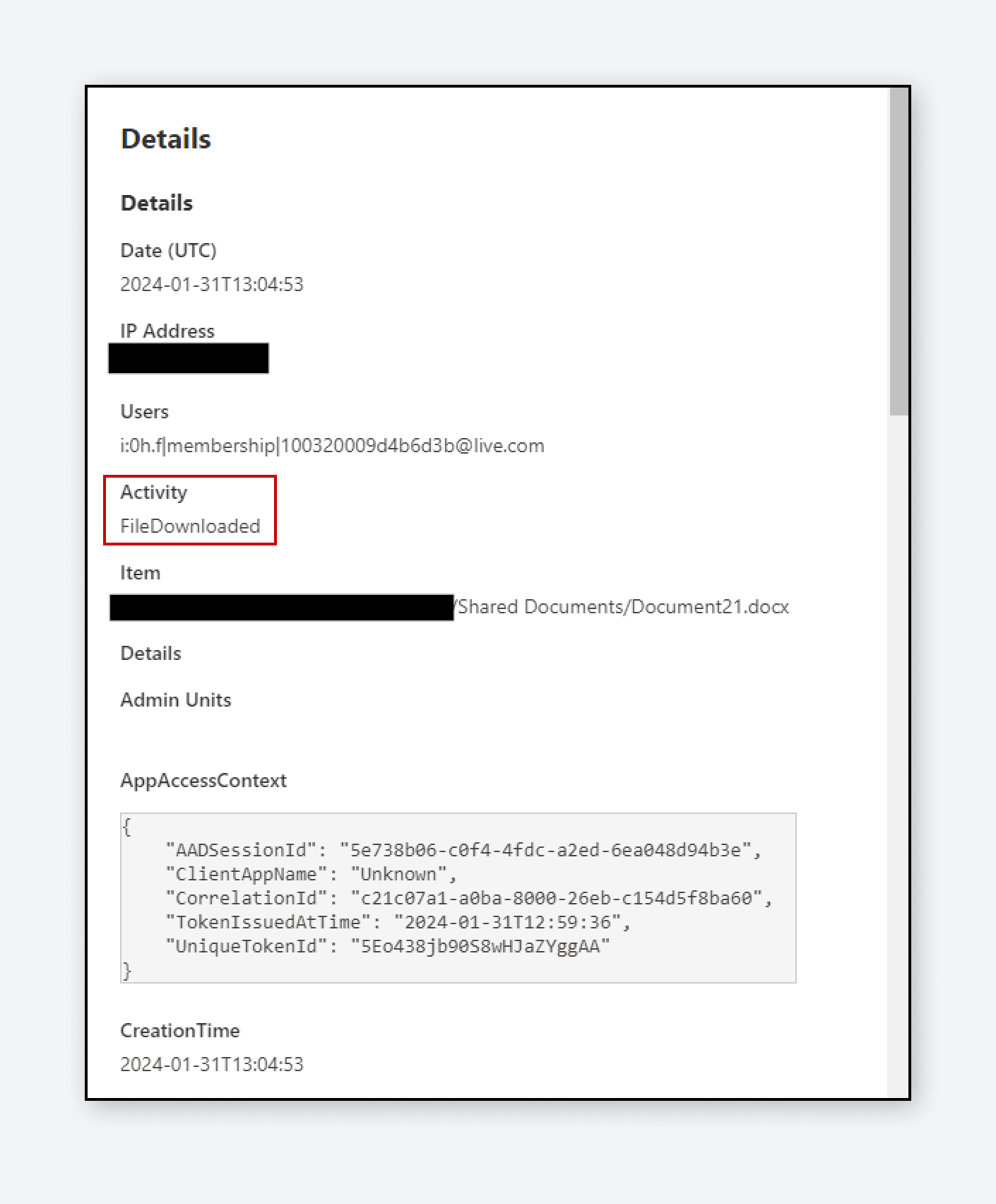
Varonis Threat Labs discovered two techniques in SharePoint that allow users to circumvent audit logs and avoid triggering download events while exfiltrating files. These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync […]
Many wireless headsets using Bluetooth technology have vulnerabilities that may allow malicious individuals to covertly listen in on private conversations, Tarlogic Security researchers have demonstrated last week at RootedCON in Madrid. “Many of the examples presented during the conference were real tests on devices that attendees – most of them cybersecurity experts – were carrying […]
Eken camera doorbells allow ill-intentioned individuals to spy on you Pierluigi Paganini March 03, 2024 Camera doorbells manufactured by the Chinese company Eken Group Ltd under the brands EKEN and Tuck are affected by major vulnerabilities. Researchers from Consumer Reports (CR) discovered severe vulnerabilities in doorbell cameras manufactured by the Chinese company Eken Group Ltd. […]
Qualcomm disclosed a critical vulnerability on New Year’s Day that would allow remote attacks via malicious voice calls over LTE networks. The January 2024 security bulletin lists a total of 26 vulnerabilities, including four critical vulnerabilities, affecting Qualcomm chipsets. Patches have already been made available to original equipment manufacturers (OEMs) whose devices use Qualcomm chips, […]
This vulnerability could allow attackers to run arbitrary PHP code on a target website. The vulnerability is a Property Oriented Programming (POP) chain that requires an attacker to control all the properties of a deserialized object.
A major vulnerability that could allow hackers to manipulate a fleet of vehicles at once — including the possibility of shutting down the vehicles — has gone ignored by the vendor for months, according to researchers that discovered the vulnerability. As the auto sector has evolved beyond a simple mode of transportation into “computers on […]
A critical vulnerability in Ray, an open source compute framework for AI, could allow unauthorized access to all nodes, cybersecurity firm Bishop Fox warns. Tracked as CVE-2023-48023, the bug exists because Ray does not properly enforce authentication on at least two of its components, namely the dashboard and client. A remote attacker can abuse this […]
Two vulnerabilities discovered earlier this year in Atos Unify products could allow malicious actors to cause disruption and even backdoor the targeted system. The flaws were found in the unified communications and collaboration solution by researchers at SEC Consult, an Austria-based cybersecurity consulting firm that is part of the Atos Group’s Eviden business. The vulnerabilities […]
- 1
- 2