Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord bot discovery site. “The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with verified commits, setting up a custom Python […]
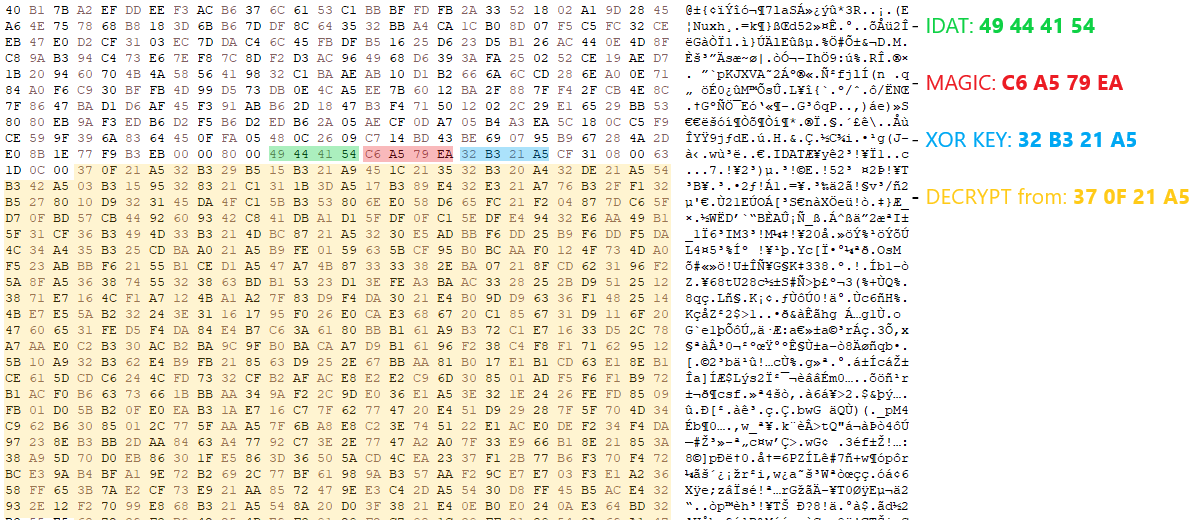
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its complexity and defense evasion CrowdStrike detects this new HijackLoader variant using machine learning and behavior-based detection capabilities CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion […]
Dec 13, 2023NewsroomCryptocurrency / Threat Analysis Microsoft has warned that adversaries are using OAuth applications as an automation tool to deploy virtual machines (VMs) for cryptocurrency mining and launch phishing attacks. “Threat actors compromise user accounts to create, modify, and grant high privileges to OAuth applications that they can misuse to hide malicious activity,” the […]
Dec 06, 2023The Hacker NewsBrowser Security / Privacy Compromising the browser is a high-return target for adversaries. Browser extensions, which are small software modules that are added to the browser and can enhance browsing experiences, have become a popular browser attack vector. This is because they are widely adopted among users and can easily turn […]
In the ever-changing landscape of cybersecurity, where threats morph, adversaries grow increasingly sophisticated, and new technology is adopted at ever greater speed, organizations are continually challenged to evaluate the effectiveness of their defenses. Traditional metrics such as the raw number of security incidents, mean time to detect, mean time to respond, or mean time to […]
As we realize exciting new advancements in the application of generative pre-trained transformer (GPT) technology, our adversaries are finding ingenious ways to leverage these capabilities to inflict harm. There’s evidence to suggest that offensive actors are using AI and machine learning techniques to carry out increasingly sophisticated, automated attacks. Rather than running from the potential […]