Regular cyber security breaches have become an unwelcome reality in the ever-evolving landscape of digital interconnectedness. Across the Asia-Pacific (APAC) region, all kinds of businesses have found themselves in the crosshairs of malicious cyber actors, challenging their resilience and exposing vulnerabilities wherever they are found. However, amid the chaos and disruption, a notable narrative begins […]
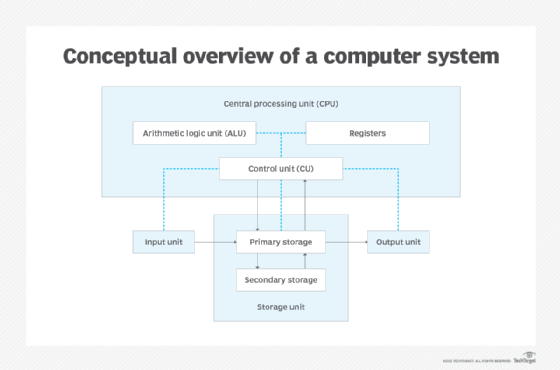
What is I/O (input/output)? I/O (input/output), pronounced “eye-oh,” describes any operation, program or device that transfers data to or from a computer. Common I/O devices include printers, hard disks, keyboards and mice. Input/output devices play a crucial role in computer programming by streamlining how computing devices communicate across a network. Why is I/O important? In […]
A data breach that impacted car manufacturer Tesla in May of this year has been confirmed as the result of “insider wrongdoing”, according to a data breach notice filed by the company. The data breach was discovered in May after German publication Handelsplatt broke the news of the cyber security incident, which saw 100GB worth […]
Last updated 30 August, 2023 We’ve teamed up with AIAIAI to offer you the chance to win one of five pairs of their brand-new TMA-2 DJ XE headphones in this free prize draw. The AIAIAI TMA-2 DJ XE are designed to appeal specifically to DJs who need durable design and custom-tuned audio for practising and […]
What is off-site backup? Off-site backup is a method of backing up data to a remote server or to media that’s transported off site. The two most common forms of off-site backup are cloud backup and tape backup. During cloud backup, also referred to as online backup, a copy of the data is sent over […]
In 2001, I switched to DJing with Traktor because it allowed me to use MIDI controllers and customize them to create new ways of playing. The modularity they offered was exciting and very innovative. Then MIDI controllers became standardized, and sadly, no custom mapped them anymore. As the years went by, DJ hardware became just […]
The Asia-Pacific (APAC) region has long been at the forefront of technological advancement and digital transformation. However, the relentless threat of malware looms larger than ever, necessitating robust strategies and measures for organizations to protect their systems and networks. Malware – encompassing malicious software such as viruses, ransomware, spyware and other threats – poses a […]
Here, Cyber Security Hub takes a look at the top cyber attacks, data breaches and cyber security incidents across the globe that happened in July, 2023. Contents: Hackers steal $20 million from Revolut Fanfiction site targeted by DDoS attack Microsoft hack sees emails stolen from US agencies HCA Healthcare data breach […]
There are many different types of malware in existence and unfortunately the number is increasing year-on-year. According to a report by software company Symantec there were almost 670 million malware variants in 2017, with researchers estimating this has risen to more than 1 billion malware programs today. While the presence of so many malware variants […]