Consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore of magna aliqua. Ut enim ad minim veniam, made of owl the quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea dolor commodo consequat. Duis aute irure and dolor in reprehenderit. The is ipsum dolor sit amet consectetur adipiscing elit. Fusce eleifend […]
Clash of Clans gamers at risk while using third-party app Pierluigi Paganini December 29, 2023 An exposed database and secrets on a third-party app puts Clash of Clans players at risk of attacks from threat actors. The Cybernews research team has discovered that the Clash Base Designer Easy Copy app exposed its Firebase database and […]
Two New York hospitals are seeking a court order to retrieve stolen data stored on a cloud storage company’s servers after a ransomware attack. The stolen data includes sensitive information such as patients’ personal and health information.
Organizations of all sizes rely on servers to support their workloads, and small businesses are no exception. However, purchasing a server can be a daunting task as there are many factors to consider beyond just the server. Here, we examine these considerations and present five servers from Asus, Dell, HPE, Fujitsu and Lenovo. SMB server […]
Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data Pierluigi Paganini December 28, 2023 Leaksmas: On Christmas Eve, multiple threat actors released substantial data leaks, Resecurity experts reported. On Christmas Eve, Resecurity protecting Fortune 100 and government agencies globally, observed multiple actors on the Dark Web releasing […]
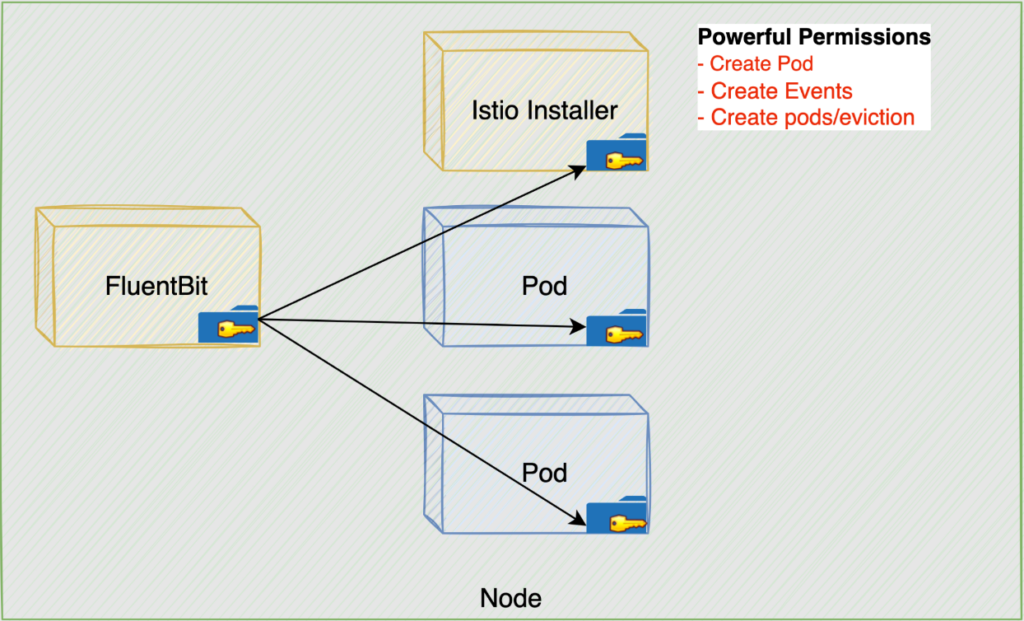
A recent Unit 42 investigation revealed a dual privilege escalation chain impacting Google Kubernetes Engine (GKE). This exploit chain arises from specific misconfigurations in GKE’s FluentBit logging agent and Anthos Service Mesh (ASM). When combined, these issues could provide attackers with existing Kubernetes cluster access an opportunity to escalate privileges. Kubernetes, a widely adopted open-source […]
As the DJing world continuously evolves, new gear is an inevitability. 2024 is likely to bring a solid set of new products to the DJ world, and we expect to see new gear that could transform how we mix, manipulate, and experience music. From stem-focused controllers to iterative updates from Pioneer DJ, we expect smart […]
Jan 01, 2024NewsroomWindows Security / Vulnerability Security researchers have detailed a new variant of a dynamic link library (DLL) search order hijacking technique that could be used by threat actors to bypass security mechanisms and achieve execution of malicious code on systems running Microsoft Windows 10 and Windows 11. The approach “leverages executables commonly found […]
Jan 01, 2024NewsroomEncryption / Network Security Security researchers from Ruhr University Bochum have discovered a vulnerability in the Secure Shell (SSH) cryptographic network protocol that could allow an attacker to downgrade the connection’s security by breaking the integrity of the secure channel. Called Terrapin (CVE-2023-48795, CVSS score: 5.9), the exploit has been described as the […]