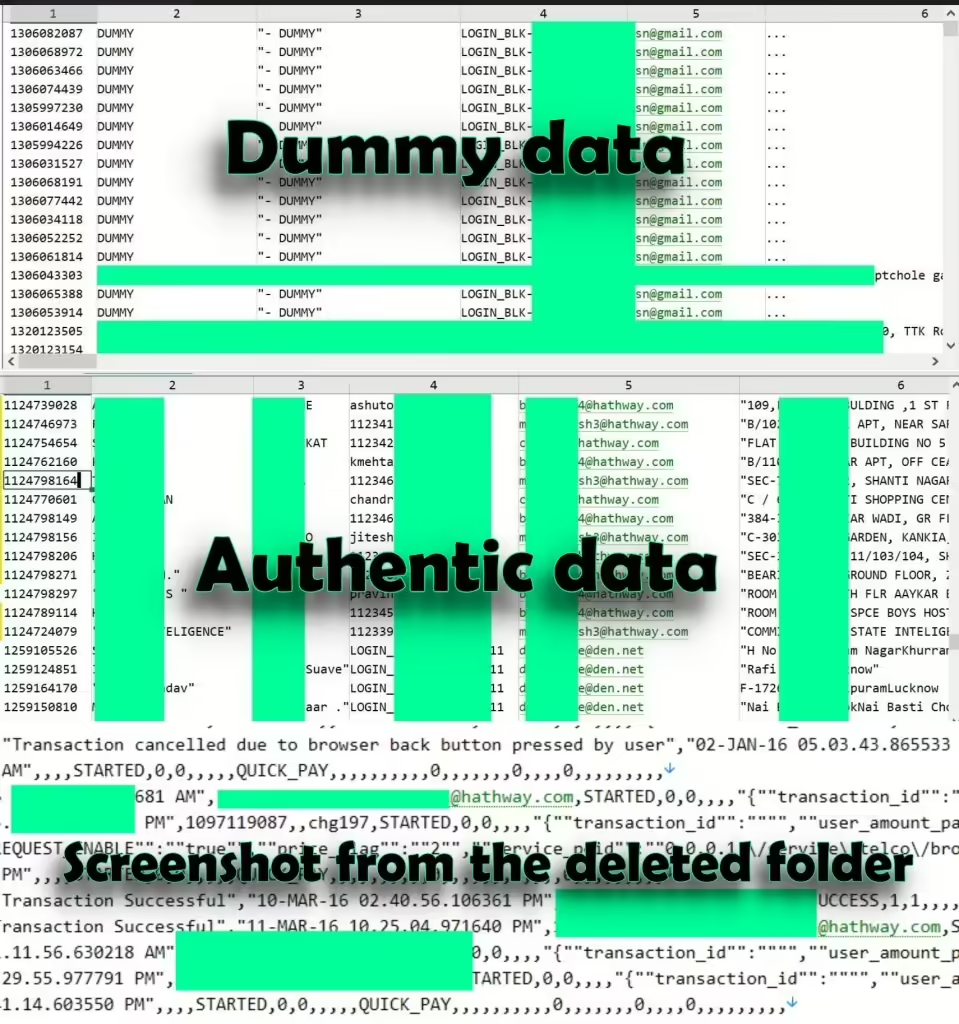
In an unusual move, the hacker behind the Hathway data breach has developed a dark web search engine for potential victims. This tool allows them to search for their email addresses and phone numbers to check if their data was exposed. A hacker operating under the alias ‘dawnofdevil’ has recently leaked a database, alleging it […]
anecdotes, a Palo Alto, CA-based enterprise GRC (Governance, Risk and Compliance) technology company, raised $25M in Series B funding. The round was led by Glilot Capital Partners, with participation from existing investors Red Dot Capital Partners, Vintage Investment Partners, and Shasta Ventures, with participation from Vertex and DTCP. The company intends to use the funds […]
Entire population of Brazil possibly exposed in massive data leak Pierluigi Paganini January 10, 2024 The private data of hundreds of millions of Brazilian individuals were publicly accessible to threat actors, putting individuals at risk. Cybernews research revealed a publicly accessible Elasticsearch instance, which contained a staggering amount of private data belonging to Brazilian individuals. […]
A coalition of rebel groups in Myanmar is now in control of the city of Laukkaing — a notorious hub of online scamming operations near the border with China. Late on Thursday, Myanmar’s military government relinquished control of the city to the Three Brotherhood Alliance, which launched a surprise operation in Shan state, along the […]
The pro-Ukrainian hacker group Blackjack is claiming that it breached a Moscow internet provider to seek revenge for a Russian cyberattack on Ukraine’s largest telecom company, Kyivstar. The attack on M9com was carried out in cooperation with Ukraine’s security forces (SBU), said a source in Ukraine’s law enforcement agency who requested anonymity because he is […]
Why is it that when a company becomes aware of a potential data security incident, the team working on it (and others who are made aware that “something” is going on) have an immediate and overwhelming feeling that the company is doomed? And yet, when there’s another kind of high-risk event, such as an ethics […]
Pikabot seems to have a binary version and a campaign ID. The keys 0fwlm4g and v2HLF5WIO are present in the JSON data, with the latter seemingly being a campaign ID. The malware creates a named pipe and uses it to temporarily store the additional information gathered by creating the following processes: whoami.exe /all ipconfig.exe /all […]
Identity & Access Management , Security Operations Company Makes Bid for Multi-Cloud Security David Perera (@daveperera) • January 9, 2024 Delinea will incorporate Authomize cross-cloud identity capabilities into its access management platform. (Image: Shutterstock) California privileged access management vendor Delinea announced Tuesday its acquisition of Israeli startup Authomize in a bid to extend […]
When organizations get hit by ransomware and pay the crooks to decrypt the encrypted data and delete the stolen data, they can never be entirely sure the criminals will do as they promised. And even if an organization gets its data decrypted, they cannot be sure the stolen data has indeed been wiped and won’t […]