What is a baseboard management controller (BMC)? A baseboard management controller (BMC) is a specialized service processor that remotely monitors the physical state of a host system, such as a computer, network server or other hardware devices. A BMC is used for remote monitoring and management of a host system. It uses sensors and communicates […]
A leading UK security agency has today published a new guide for small and medium-sized businesses (SMBs) designed to help reduce the potential impact of cyber-attacks when using online services. The National Cyber Security Centre (NCSC) said its Using online services safely guide is specifically aimed at organizations that may not have access to dedicated […]
Trend Micro observed the Water Curupira actively propagating the Pikabot loader malware as part of campaigns, more aggressively in Q4 2023. Water Curupira is a Black Basta ransomware affiliate. Diving into Details Pikabot gained notoriety for its sophisticated multi-stage attack mechanism, capable of deploying a decrypted shellcode that extracts another DLL file, the actual payload. […]
HMG Healthcare disclosed a data breach Pierluigi Paganini January 10, 2024 The Healthcare services provider HMG Healthcare has disclosed a data breach that impacted 40 affiliated nursing facilities. In November 2023, the Healthcare services provider HMG Healthcare discovered a data breach that exposed personal health information related to residents and employees at HMG affiliated nursing […]
A 22-year-old Frenchman was sentenced on Tuesday to three years in U.S. federal prison for his participation in the ShinyHunters hacking group. Sebastien Raoult, also known as “Sezyo Kaizen,” was extradited to the U.S. in January 2023 after his arrest in Morocco the year before. He pleaded guilty to conspiracy to commit wire fraud and […]
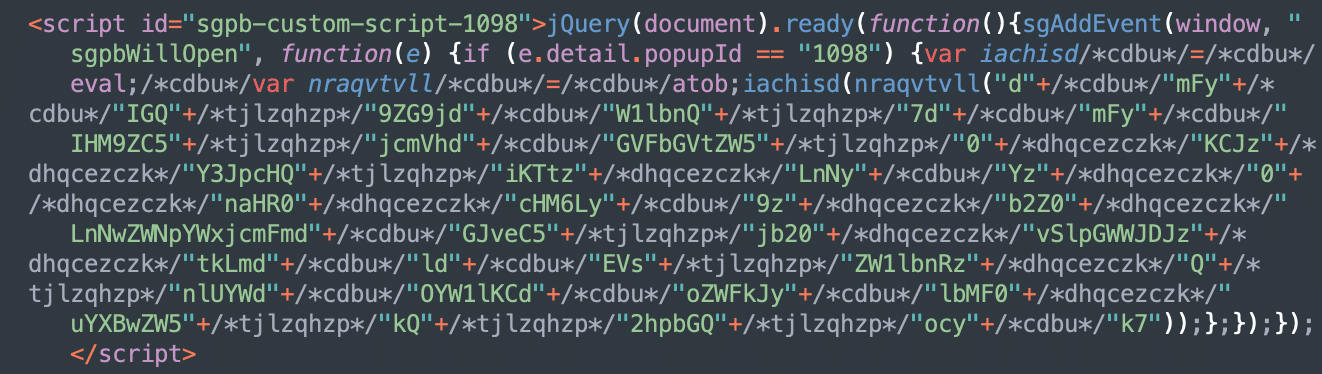
On December 11, 2023 WPScan published Marc Montpas’ research on the stored XSS vulnerability in the popular Popup Builder plugin (200,000+ active installation) that was fixed in version 4.2.3. A couple of days later, on December 13th, the Balada Injector campaign started infecting websites with older versions of the Popup Builder. The attack used a […]
ExtraHop, a Seattle, WA-based company which specialises in cloud-native network detection and response (NDR), raised $100M in Growth Capital. The round saw participation from undisclosed existing investors. The company intends to use the funds to expand operations and its business reach. Led by Greg Clark, CEO, ExtraHop provides the Reveal(x) platform that delivers 360-degree visibility […]
A well-designed operation is using a version of the infamous Mirai malware to secretly distribute cryptocurrency mining software, researchers said Wednesday. Calling it NoaBot, researchers at Akamai said the campaign has been active for about a year, and it has various quirks that complicate analysis of the malware and point to highly-skilled threat actors. The […]
As large language models (LLMs) become more prevalent, a comprehensive understanding of the LLM threat landscape remains elusive. But this uncertainty doesn’t mean progress should grind to a halt: Exploring AI is essential to staying competitive, meaning CISOs are under intense pressure to understand and address emerging AI threats. While the AI threat landscape changes […]