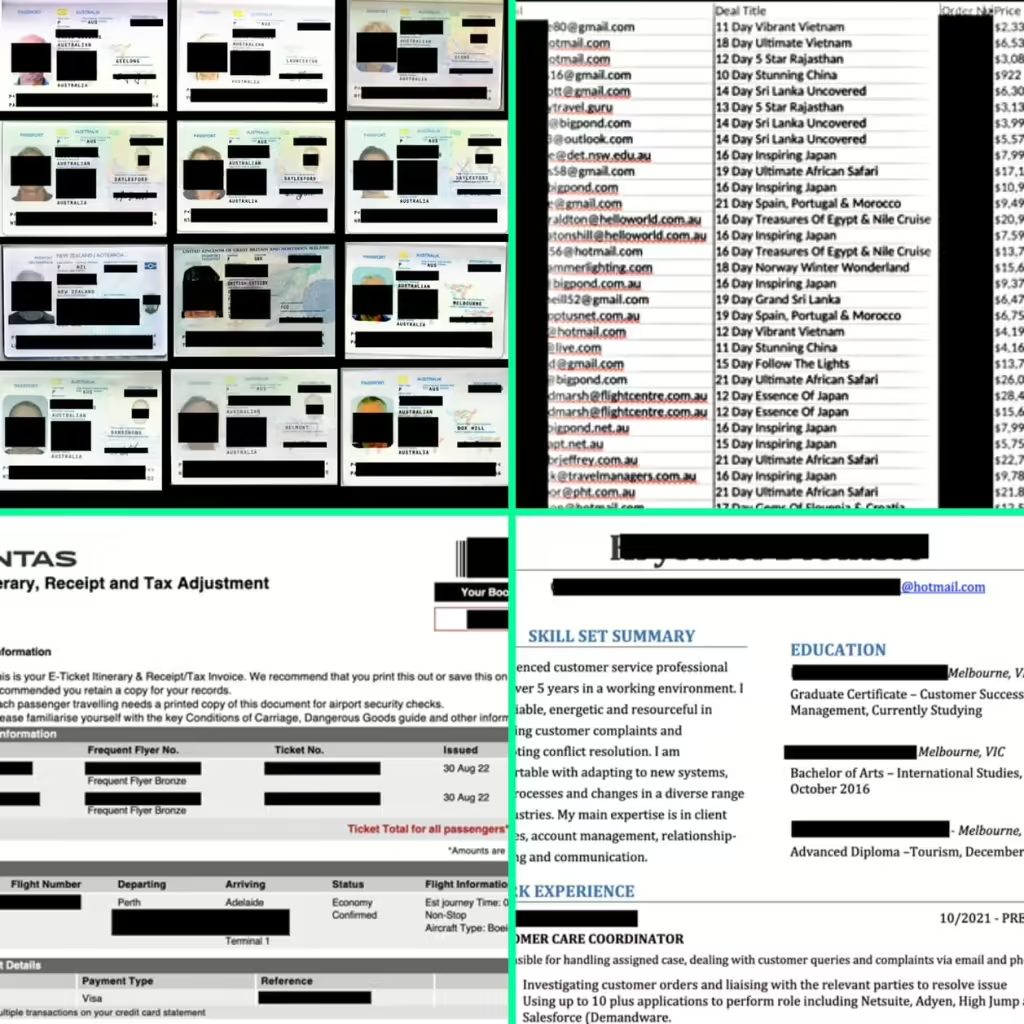
Melbourne-based travel agency, Inspiring Vacations, left a massive 26.8 GB database publicly exposed, devoid of any security measures like authentication or passwords. A data leak at a Melbourne-based travel agency has exposed the personal information of thousands of tourists, raising concerns about online security and privacy in the travel industry. The leak was discovered by […]
The US Cybersecurity and Infrastructure Security Agency (CISA) has urged critical infrastructure organizations to address vulnerabilities affecting nine industrial control systems (ICS) products. The report, dated January 11, 2024, highlighted a series of high and critical severity vulnerabilities in products widely used in sectors like energy, manufacturing and transportation. Users and administrators in these sectors […]
The Federal Communications Commission (FCC) is urging automakers and wireless providers to do more to protect domestic abuse survivors from stalking tools enabled by connected cars and requesting the details of their location data-sharing practices. Connected cars are now loaded with sensors and other tools which allow real-time geolocation tracking. A recent Reuters report revealed […]
Key takeaways AgentTesla (also known as OriginLogger) remains a prevalent commodity stealer, being daily distributed, mainly via email attachments; The primary method for exfiltrating data remains the usage of mail servers, although Telegram utilization is increasing; Available infection telemetry suggests that the most targeted countries are the United States, China and Germany. Malware as a […]
Critical Infrastructure Security DHS Office of Inspector General Finds Lack of Coordination With EPA David Perera (@daveperera) • January 12, 2024 A U.S. federal watchdog urged the Cybersecurity and Infrastructure Security Agency to coordinate more on water system cybersecurity. (Image: Shutterstock) A U.S. federal watchdog said government agencies could better synchronize efforts to […]
A 29-year-old man in Ukraine was arrested for using hacked accounts to create 1 million virtual servers and mine $2 million in cryptocurrency, highlighting the growing threat of cryptojacking.
As we reflect on the cybersecurity landscape and the trajectories of threat vectors, it’s evident that we’re on the cusp of a paradigm shift in cloud security. Businesses and cybersecurity professionals must stay abreast of these changes, adapting their strategies to ensure a robust, effective, and resilient security posture. Amidst rising cybersecurity challenges, SMBs and […]
Jan 15, 2024NewsroomOperational Technology / Network Security Multiple security vulnerabilities have been disclosed in Bosch BCC100 thermostats and Rexroth NXA015S-36V-B smart nutrunners that, if successfully exploited, could allow attackers to execute arbitrary code on affected systems. Romanian cybersecurity firm Bitdefender, which discovered the flaw in Bosch BCC100 thermostats last August, said the issue could be […]
Apple fixed a bug in Magic Keyboard that allows to monitor Bluetooth traffic Pierluigi Paganini January 15, 2024 Apple addressed a recently disclosed Bluetooth keyboard injection vulnerability with the release of Magic Keyboard firmware. Apple released Magic Keyboard Firmware Update 2.0.6 to address a recently disclosed Bluetooth keyboard injection issue tracked as CVE-2024-0230. The flaw […]