Last updated 18 January, 2024 In this replay of our live Q&A lesson, we discussed the sound quality of stems, whether DJs should pre-plan their sets or mix on the fly, how to easily make mashups, and more! About this lesson This is a recording of one of our free Thursday Q&A Live DJ lessons […]
In with the in(mate) crowd Maria W Horn is a Swedish composer whose work explores the inherent spectral properties of sound. Using everything from analogue synthesisers to choirs, string instruments, pipe organ and various chamber music formats, she loves to mix synthetic sound with acoustic instruments. Horn combines spectralist techniques and site-specific source material in […]
The bot gains access to the databases, deletes all tables and databases, and leaves a ransom note demanding payment for data recovery. However, the bot only saves a small portion of the data, even if the ransom is paid.
What happened Proofpoint researchers identified the return of TA866 to email threat campaign data, after a nine-month absence. On January 11, 2024, Proofpoint blocked a large volume campaign consisting of several thousand emails targeting North America. Invoice-themed emails had attached PDFs with names such as “Document_[10 digits].pdf” and various subjects such as “Project achievements”. The […]
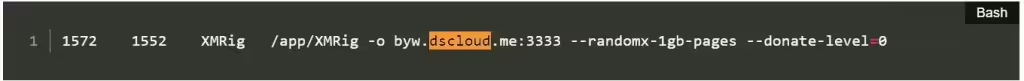
Jan 18, 2024NewsroomServer Security / Cryptocurrency Vulnerable Docker services are being targeted by a novel campaign in which the threat actors are deploying XMRig cryptocurrency miner as well as the 9Hits Viewer software as part of a multi-pronged monetization strategy. “This is the first documented case of malware deploying the 9Hits application as a payload,” […]
Cybercriminals are targeting vulnerable Docker servers by deploying two containers: a standard XMRig miner and the 9Hits viewer application—an automated traffic exchange system. Cado Security researchers have discovered a new campaign targeting vulnerable Docker servers, deploying two containers – a regular XMRig miner and the 9hits viewer application. This is the first documented case of malware deploying the […]
Jan 18, 2024NewsroomSupply Chain Attacks / AI Security Continuous integration and continuous delivery (CI/CD) misconfigurations discovered in the open-source TensorFlow machine learning framework could have been exploited to orchestrate supply chain attacks. The misconfigurations could be abused by an attacker to “conduct a supply chain compromise of TensorFlow releases on GitHub and PyPi by compromising […]
Three-quarters (75%) of organizations suffered at least one ransomware attack last year, according to Veeam’s Data Protection Trends Report 2024. The researchers showed that more organizations got hit four or more times in 2023 (26%) than those who said they didn’t experience any ransomware attacks. Speaking during a virtual pre-briefing, Jason Buffington, VP, Market Strategy […]
The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver its first-ever custom malware written in the Rust programming language. Google’s Threat Analysis Group (TAG), which shared details of the latest activity, said the attack chains leverage PDFs as decoy documents to trigger the infection […]