Several public and popular libraries abandoned but still used in Java and Android applications have been found susceptible to a new software supply chain attack method called MavenGate. “Access to projects can be hijacked through domain name purchases and since most default build configurations are vulnerable, it would be difficult or even impossible to know […]
Klaus Benedek is our Fortunea teller WHAT’S THE NAME OF YOUR LABEL, AND WHO RUNS IT? I am Klaus Benedek, the founder of Fortunea Records. WHEN & WHY DID THE LABEL START? I started the label originally only for my own output in Hune 2014. At that time I had a lot of tracks signed […]
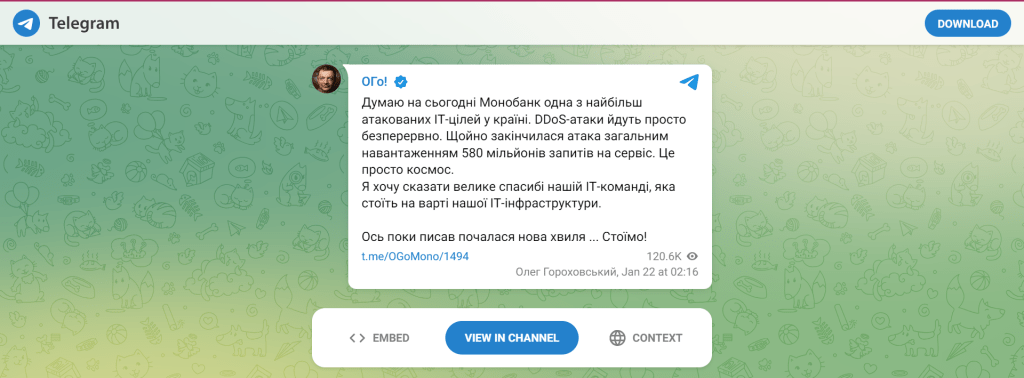
Monobank, Ukraine’s largest mobile-only bank, faced a barrage of denial of service (DDoS) attacks on January 21, crippling its operations and causing widespread disruption. Co-founder and CEO Oleh Horokhovskyi took to Telegram to confirm the Monobank cyberattack, revealing that the bank was targeted with a staggering 580 million service requests in one of the attacks. […]
This post is also available in: 日本語 (Japanese) Executive Summary A traffic direction system (TDS) nicknamed Parrot TDS has been publicly reported as active since October 2021. Websites with Parrot TDS have malicious scripts injected into existing JavaScript code hosted on the server. This TDS is easily identifiable by keywords found in the injected JavaScript […]
In an exclusive statement to The Cyber Express team, DENHAM the Jeanmaker, the renowned denim brand founded in Amsterdam in 2008, confirmed falling victim to a cyberattack. The denim giant disclosed that the DENHAM cyberattack was first discovered on December 27, 2023. Subsequently, The Cyber Express (TCE) reported that DENHAM the Jeanmaker had been targeted […]
Medication’s what you need – if you want to be a record maker Jon Carter, a prominent name in the big beat movement and Heavenly Records artist, is to return to music production with the release of his new album, Medication Time on Irvine Welsh’s Jack said What label on February 16. A prominent figure […]
Technical Analysis In the following sections, we dive into the technical details surrounding Zloader’s new updates to their anti-analysis techniques, embedded configuration, DGA, and network encryption. Anti-analysis techniques Zloader uses a combination of API import hashing, junk code, a filename check, and string obfuscation. The following sections analyze each technique. Imports and API resolution The […]
Cybercriminals leaked massive volumes of stolen PII data from Thailand in Dark Web Pierluigi Paganini January 22, 2024 Resecurity researchers warn of massive leak of stolen Thai personally identifiable information (PII) on the dark web by cybercriminals. Resecurity has detected a noticeable increase in data leaks from consumer-focused platforms in Thailand, confirming that threat actors […]
Finnish IT services and cloud hosting provider Tietoevry was hit by a ransomware attack, affecting a data center in Sweden and causing outages for multiple customers, including Filmstaden, Rusta, Moelven, and Grangnården.