AlphaTheta – Pioneer DJ’s owners and now a brand onto themselves – are taking on low-latency wireless audio. Today they’re introducing the WAVE-EIGHT, a portable wireless DJ speaker that aims to make setting up a party without running cables that much easier. [embedded content] The easiest way to explain the WAVE-EIGHT to DJs who already […]
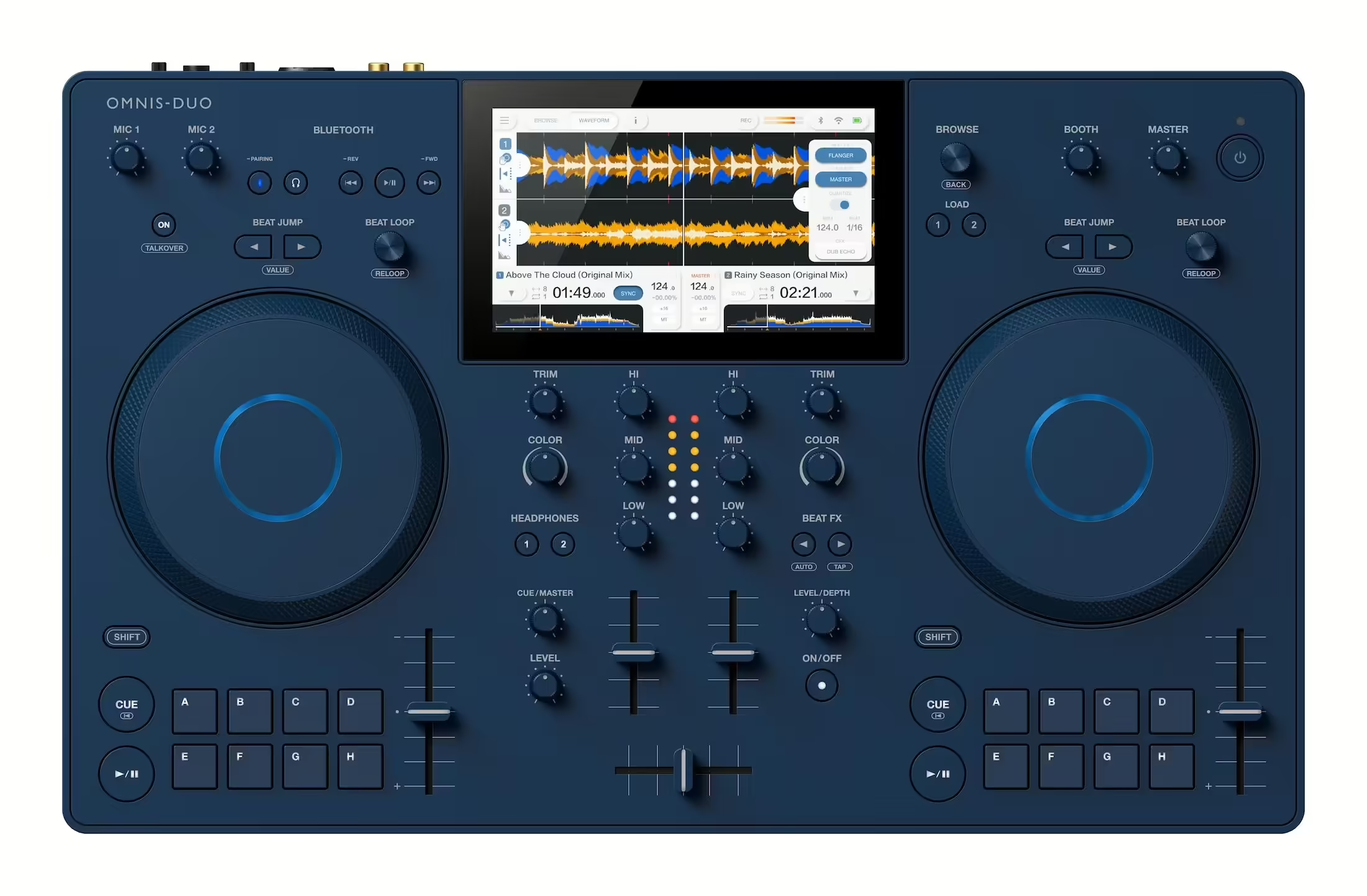
Meet the brand new OMNIS-DUO from AlphaTheta. The battery-powered all-in-one standalone market – previously occupied only by the Denon DJ’s Prime Go and Numark’s Mixstream Pro – gains a new member today. The well-leaked device will be the first DJ product to bear the AlphaTheta logo and word mark on it. Yesterday, diligent internet sleuths […]
CISA adds Atlassian Confluence Data Center bug to its Known Exploited Vulnerabilities catalog Pierluigi Paganini January 25, 2024 U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Atlassian Confluence Data Center and Server Template Injection bug to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added an Atlassian Confluence Data Center and Server Template […]
As a bit of a kick-off to the NAMM 2024 news cycle in terms of released gear, Reloop this morning announced the Mixtour Pro. It’s a slim, small form-factor mixer controller with a built-in audio interface, designed to control four decks in Algoriddim djay Pro (although we’re sure you’ll be able to use it with […]
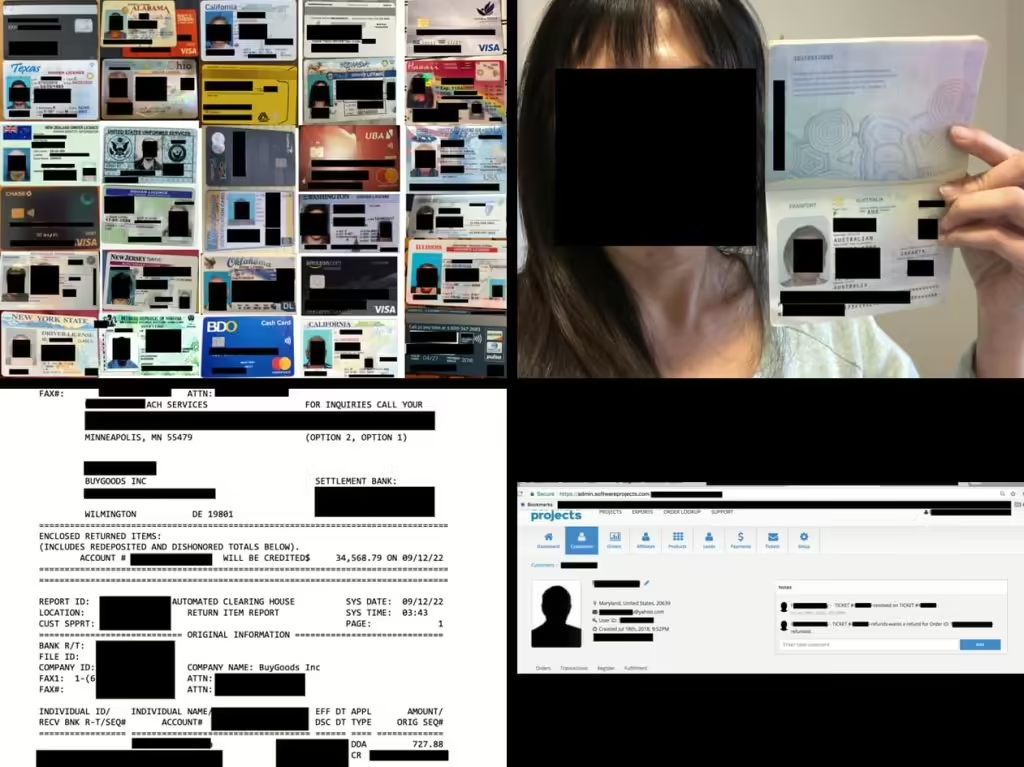
The staggering 198.3 gigabytes of misconfigured database contained more than 260,000 records including customer selfies with unredacted credit cards. Cybersecurity researcher Jeremiah Fowler recently uncovered a misconfigured cloud database that had left a wealth of sensitive data exposed. The affected database contained records attributed to customers of BuyGoods.com, alternatively recognized in the industry as Softwareproject. […]
Following our discovery of a critical loophole in Google Kubernetes Engine (GKE) dubbed Sys:All, we decided to conduct research into the real-world impacts of this issue. Our initial probe already revealed over a thousand vulnerable GKE clusters due to admins configuring RBAC bindings making the system:authenticated group overprivileged, which could potentially allow any Google account […]
The company has discovered a limited number of individuals whose personal information may have been impacted during the breach and is working with a third-party forensics firm to assess the extent of the attack’s impact on its operations and systems.
KB5034204 also fixes an issue caused by a deadlock that prevents search from working on the Start menu for some users and addresses a bug affecting the OpenType font driver, affecting how text renders for third-party applications.
ReversingLabs researchers have discovered two malicious packages on the npm open source package manager that leverages GitHub to store stolen Base64-encrypted SSH keys lifted from developer systems that installed the malicious npm packages.