Chip vendor Intel is sticking with its vision of being the alternative to Nvidia and its AI processors while maintaining its messaging that it helps enterprises avoid vendor lock-in. At its Intel Vision conference in Phoenix on April 9, the vendor introduced its latest AI accelerator, Gaudi 3. While Intel has been teasing Gaudi 3 […]
Apr 10, 2024NewsroomCyber Crime / Malvertising Cybersecurity researchers have discovered a new Raspberry Robin campaign wave that propagates the malware through malicious Windows Script Files (WSFs) since March 2024. “Historically, Raspberry Robin was known to spread through removable media like USB drives, but over time its distributors have experimented with other initial infection vectors,” HP […]
Apr 10, 2024NewsroomSoftware Security / Supply Chain Attack Threat actors are now taking advantage of GitHub’s search functionality to trick unsuspecting users looking for popular repositories into downloading spurious counterparts that serve malware. The latest assault on the open-source software supply chain involves concealing malicious code within Microsoft Visual Code project files that’s designed to […]
A new threat actor dubbed “Starry Addax” is targeting human rights activists associated with the Sahrawi Arab Democratic Republic (SADR) cause in North Africa using a novel mobile malware named “FlexStarling.” Starry Addax’s modus operandi involves conducting phishing attacks, enticing victims into installing malicious Android apps that are disguised as legitimate tools. The apps impersonate […]
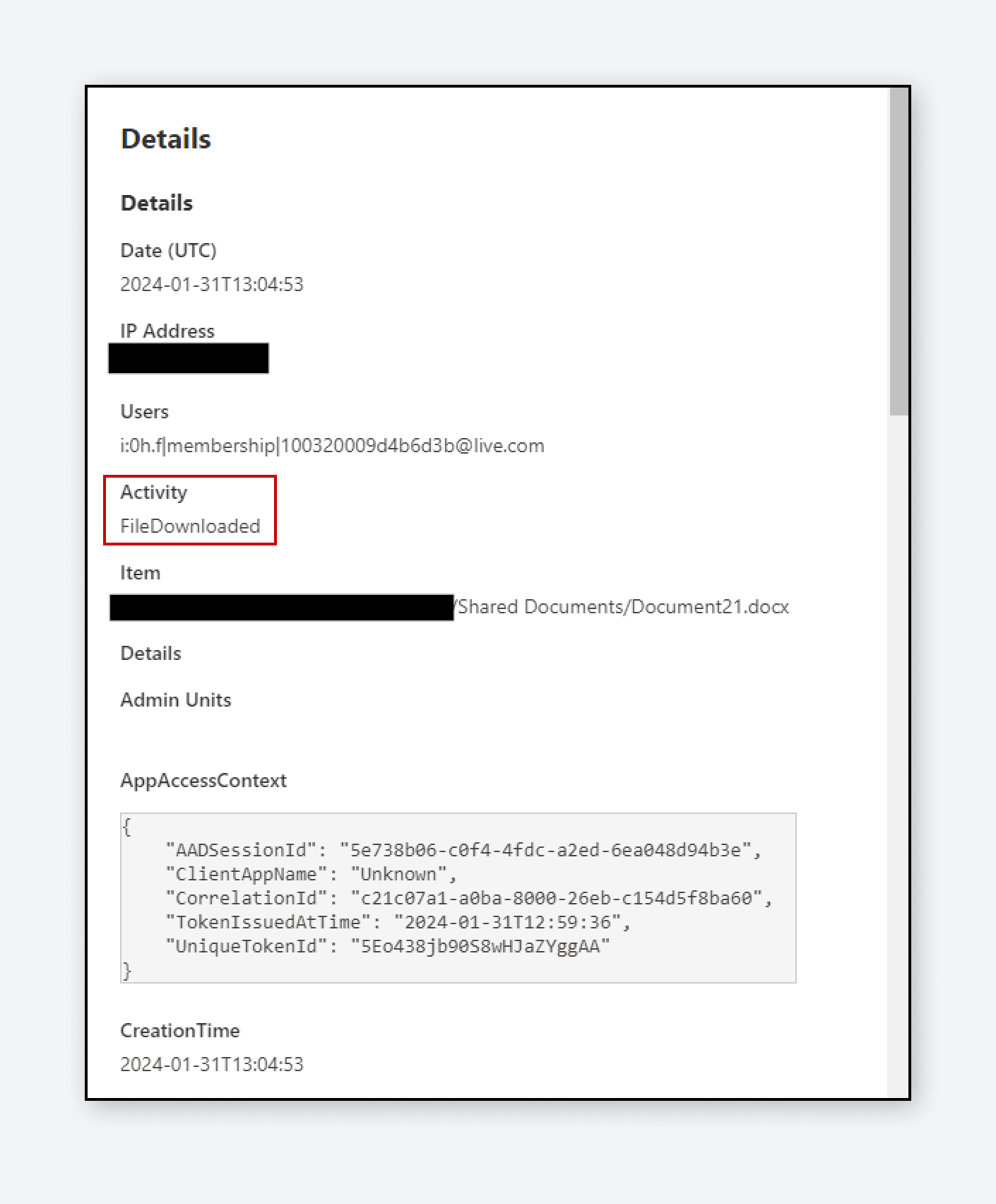
Varonis Threat Labs discovered two techniques in SharePoint that allow users to circumvent audit logs and avoid triggering download events while exfiltrating files. These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync […]
A recent research study has shed light on the decade-long activities of a Romanian cyber threat group known as RUBYCARP, which uses techniques such as cryptocurrency mining and phishing. One of the key findings from the technical write-up, published by Sysdig today, is the group’s use of a script capable of simultaneously deploying multiple cryptocurrency […]
The need for vCISO services is growing. SMBs and SMEs are dealing with more third-party risks, tightening regulatory demands and stringent cyber insurance requirements than ever before. However, they often lack the resources and expertise to hire an in-house security executive team. By outsourcing security and compliance leadership to a vCISO, these organizations can more […]
A previously unknown ransomware gang has been attacking Russian businesses with malware based on the leaked source code from the Conti hacking group. The gang, which researchers at the Moscow-based cybersecurity company F.A.C.C.T. have dubbed “Muliaka,” or Muddy Water in English, has left minimal traces from its attacks but has likely been active since at […]
Cybersecurity researchers from Bitdefender discovered critical vulnerabilities in LG TVs running webOS versions 4 through 7. These vulnerabilities could allow attackers to gain complete control over the TV, steal data, or install malware. The vulnerabilities were identified by Bitdefender as part of their research into the security of popular IoT devices. They found that attackers […]