Threat actors created a website to impersonate UsenetClub, a subscription service for “uncensored” access to images and videos downloaded from Usenet. They claimed to provide free access to the site after the installation of a “CryptVPN” software.
Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by a cyberattack. Yes, over half. And this, in a world where enterprises deploy an average of 53 different security solutions to safeguard their digital domain. Alarming? Absolutely. A recent survey of CISOs and CIOs, commissioned […]
Apr 22, 2024The Hacker NewsNetwork Security / Cybersecurity The MITRE Corporation revealed that it was the target of a nation-state cyber attack that exploited two zero-day flaws in Ivanti Connect Secure appliances starting in January 2024. The intrusion led to the compromise of its Networked Experimentation, Research, and Virtualization Environment (NERVE), an unclassified research and […]
Cybersecurity researchers have found almost 30 phishing websites spoofing the electronic toll collection service E-ZPass following an FBI warning last week. The FBI said in an alert that since early March the Internet Crime Complaint Center (IC3) has received over 2,000 complaints reporting smishing texts impersonating road toll collection services from at least three states. […]
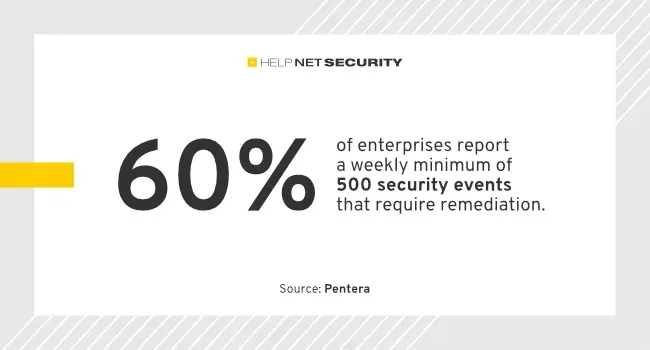
Threat actors are continuing to successfully breach across the entire attack surface and the stakes are only getting higher: 93% of enterprises who admitted a breach reported unplanned downtime, data exposure, or financial loss as a result, according to Pentera. Pentera surveyed 450 CISOs, CIOs, and IT security leaders at enterprise companies with more than […]
Between crossovers – Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that have experienced a Cyber Extortion / Ransomware attack, we noticed that some victims re-occur. Consequently, the question arises why we observe a re-victimization and whether or not this is an actual second attack, an affiliate crossover […]
A flaw in the Forminator plugin impacts hundreds of thousands of WordPress sites Pierluigi Paganini April 22, 2024 Japan’s CERT warns of a vulnerability in the Forminator WordPress plugin that allows unrestricted file uploads to the server. Japan’s CERT warned that the WordPress plugin Forminator, developed by WPMU DEV, is affected by multiple vulnerabilities, including a […]
Fraud Management & Cybercrime , Ransomware Domestic Teen Groups Demand ‘Nip the Bud’ and ‘Alternative Pathways,’ Experts Say Mathew J. Schwartz (euroinfosec) • April 19, 2024 Ransomware experts are concerned about the rise of Western affiliates of mostly Russian ransomware groups. (Image: Shutterstock) Western law enforcement agencies are battling a rising ransomware threat: […]
Apr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and processes. “When a user executes a function that has a path argument in Windows, the DOS path at which the file or […]