In a move away from traditional phishing scams, attackers are increasingly exploiting vulnerabilities in computer systems to gain initial network access, according to Mandiant’s M-Trends 2024 Report. In 2023, attackers gained initial access through exploiting vulnerabilities in 38% of intrusions, a 6% increase from the previous year. Mandiant also found phishing’s prevalence declined from 22% […]
A notorious Russian APT group has been stealing credentials for years by exploiting a Windows Print Spooler bug and using a novel post-compromise tool known as “GooseEgg,” Microsoft has revealed. APT28 (aka Strontium, Forest Blizzard) has been using GooseEgg since potentially as far back as April 2019 to exploit CVE-2022-38028, Microsoft said in a new […]
The Cybersecurity and Infrastructure Security Agency is targeting a Sept. 30 deadline to give federal agencies a list of example software products deemed critical for the federal government’s cyber posture. The target date comes from the agency’s responses to a Thursday Government Accountability Office oversight report that examines implementation of a major 2021 cybersecurity executive […]
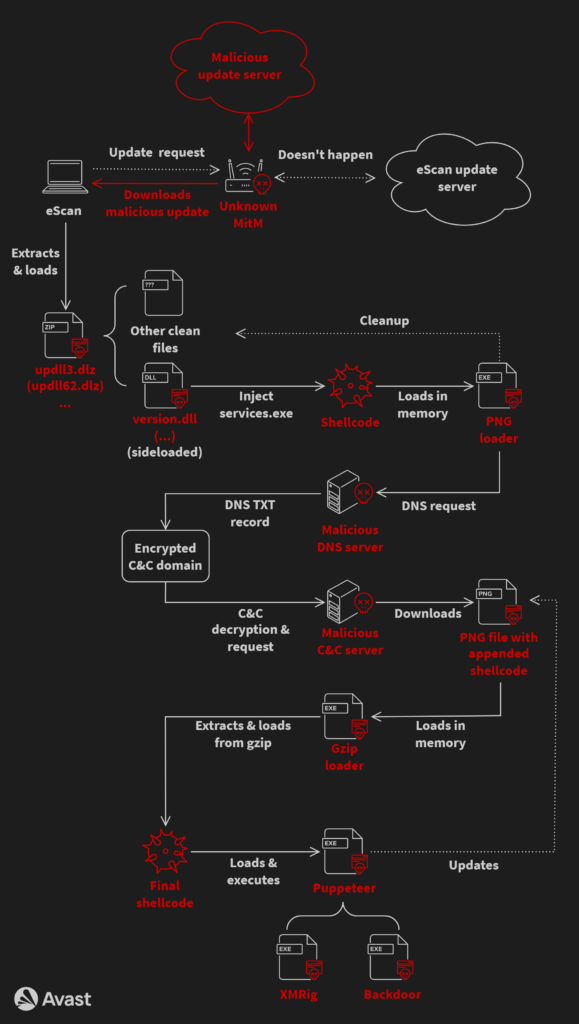
Key Points Avast discovered and analyzed a malware campaign hijacking an eScan antivirus update mechanism to distribute backdoors and coinminers Avast disclosed the vulnerability to both eScan antivirus and India CERT. On 2023-07-31, eScan confirmed that the issue was fixed and successfully resolved The campaign was orchestrated by a threat actor with possible ties to […]
Last updated 23 April, 2024 We’ve teamed up with AlphaTheta to offer you the chance to win a pair of their brand-new Wave Eight portable battery-powered PA speakers. The Wave Eights come complete with AlphaTheta’s cable-free SonicLink wireless technology, meaning DJing from ANY DJ gear without cables is fully possible with these, with no additional […]
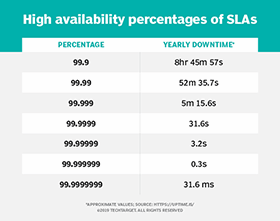
What is high availability (HA)? High availability (HA) is the ability of a system to operate continuously for a designated period of time even if components within the system fail. A highly available system meets an agreed-upon operational performance level by eliminating single points of failure. This is accomplished by including redundant components that serve […]
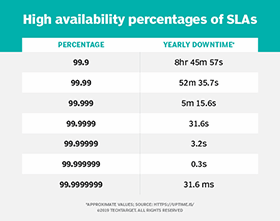
What is high availability (HA)? High availability (HA) is the ability of a system to operate continuously for a designated period of time even if components within the system fail. A highly available system meets an agreed-upon operational performance level by eliminating single points of failure. This is accomplished by including redundant components that serve […]
Juno Daily favourites PREGOBLIN and more to play Strap Originals shows Peter Doherty is hosting three special celebratory nights in Manchester and London in May to mark his Strap Originals label’s fifth anniversary. Each night will feature Strap Originals artists live in concert on all three nights and Doherty will do a Q&A with a journalist about his life, his music […]
Apr 23, 2024NewsroomSupply Chain Attack / Application Security Researchers have identified a dependency confusion vulnerability impacting an archived Apache project called Cordova App Harness. Dependency confusion attacks take place owing to the fact that package managers check the public repositories before private registries, thus allowing a threat actor to publish a malicious package with the […]