23% of Americans said they recently came across a political deepfake they later discovered to be fake, according to McAfee. The actual number of people exposed to political and other deepfakes is expected to be much higher given many Americans are not able to decipher what is real versus fake, thanks to the sophistication of […]
After failing to achieve “expected results,” Sweden’s National Cyber Security Center (NCSC) is facing a range of reforms, including being brought under the control of the country’s cyber and signals intelligence agency. The failures were assessed as part of a government review, rather than in response to a single incident, but come amid a changing […]
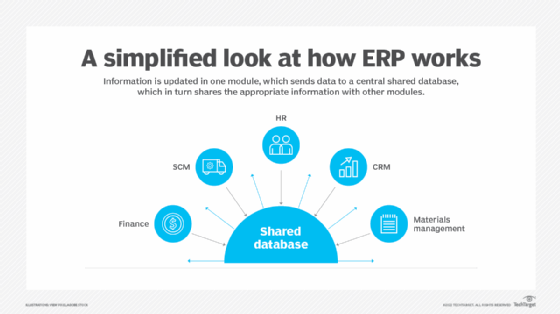
What is Electronic Data Interchange (EDI)? Electronic Data Interchange (EDI) is the transfer of data from one computer system to another by standardized message formatting without the need for human intervention. The goal of EDI is to replace manual processes that involve the exchange of documents with a fully autonomous one. EDI permits multiple companies […]
What is Electronic Data Interchange (EDI)? Electronic Data Interchange (EDI) is the transfer of data from one computer system to another by standardized message formatting without the need for human intervention. The goal of EDI is to replace manual processes that involve the exchange of documents with a fully autonomous one. EDI permits multiple companies […]
The DIB Vulnerability Disclosure Program (DIB-VDP), a joint venture between the DoD Cyber Crime Center (DC3), the Defense Counterintelligence and Security Agency (DCSA), and HackerOne, will bring better vulnerability disclosure practices to the DIB.
Apr 24, 2024NewsroomMalware / Data Security A new ongoing malware campaign has been observed distributing three different stealers, such as CryptBot, LummaC2, and Rhadamanthys hosted on Content Delivery Network (CDN) cache domains since at least February 2024. Cisco Talos has attributed the activity with moderate confidence to a threat actor tracked as CoralRaider, a suspected […]
Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Researchers Keep Prompts Under Wraps Rashmi Ramesh (rashmiramesh_) • April 22, 2024 Researchers said their GPT-4 agent performed exceptionally well at crafting exploits after being fed CVEs. (Image: Shutterstock) Academics at a U.S. university found that if you feed a GPT-4 artificial […]
Last updated 25 April, 2024 Playing your first ever DJ gig, whether that’s a mobile event, a club gig, residency, in a bar, whatever, is one of the most nerve-wracking things you could possibly imagine. It’s equally that way if it’s the first gig you’ve played in a long time, of course. Here at Digital […]