Apr 23, 2024NewsroomNational Security Agency / Threat Intelligence The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component to deliver a previously unknown custom malware called GooseEgg. The post-compromise tool, which is said to have been used since at least June 2020 and possibly as early […]
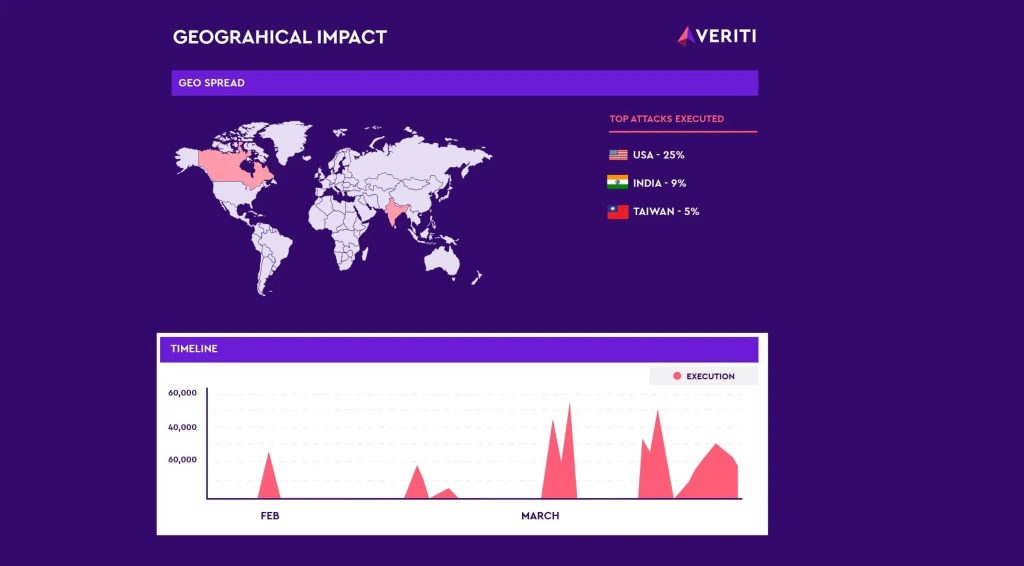
Veriti Research has discovered a surge in attacks from operators of the Androxgh0st malware family, uncovering over 600 servers compromised primarily in the U.S., India and Taiwan. According to Veriti’s blog post, the adversary behind Androxgh0st had their C2 server exposed, which could allow for a counterstrike by revealing the impacted targets. The researchers then […]
A dependency confusion vulnerability has been found within an archived Apache project. According to new data by Legit Security, who made the discovery, the finding underscores the importance of scrutinizing third-party projects and dependencies, particularly those archived and potentially neglected in terms of updates and security patches. The technical post, published today, suggests that despite […]
Affected platforms: All platforms where PyPI packages can be installedImpacted parties: Any individuals or institutions that have these malicious packages installedImpact: Leak of credentials, sensitive information, etc.Severity level: High Vigilance is paramount in cybersecurity, especially when it comes to understanding and dissecting potentially malicious code. In this blog post, we’ll delve into a piece of […]
The simplified version of this python tool is available here. IOC FileName SHA256 vcruntime140.dll 72b92683052e0c813890caf7b4f8bfd331a8b2afc324dd545d46138f677178c4 d0a8fa332950b72968bdd1c8a1a0824dd479220d044e8c89a7dea4434b741750 YARA Rule: import “pe”rule possible_wine_loader_export_function {meta:author = “@tccontre18 – Br3akp0int”description = “possible wine loader export function setup code”date = “2024-04-03″sha256 = “72b92683052e0c813890caf7b4f8bfd331a8b2afc324dd545d46138f677178c4″strings:$exp_loader = {48 83 EC 08 48 8D 0D ?? ?? ?? ?? 48 C7 C2 28 80 00 […]
Apr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky characterized the adversary as relying on various programs to harvest data on an “industrial scale” from primarily governmental organizations, […]
Threat actors created a website to impersonate UsenetClub, a subscription service for “uncensored” access to images and videos downloaded from Usenet. They claimed to provide free access to the site after the installation of a “CryptVPN” software.
Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by a cyberattack. Yes, over half. And this, in a world where enterprises deploy an average of 53 different security solutions to safeguard their digital domain. Alarming? Absolutely. A recent survey of CISOs and CIOs, commissioned […]
Apr 22, 2024The Hacker NewsNetwork Security / Cybersecurity The MITRE Corporation revealed that it was the target of a nation-state cyber attack that exploited two zero-day flaws in Ivanti Connect Secure appliances starting in January 2024. The intrusion led to the compromise of its Networked Experimentation, Research, and Virtualization Environment (NERVE), an unclassified research and […]