Microsoft has released security updates for the month of April 2024 to remediate a record 149 flaws, two of which have come under active exploitation in the wild. Of the 149 flaws, three are rated Critical, 142 are rated Important, three are rated Moderate, and one is rated Low in severity. The update is aside […]
Apr 10, 2024NewsroomSoftware Security / Vulnerability A critical security flaw in the Rust standard library could be exploited to target Windows users and stage command injection attacks. The vulnerability, tracked as CVE-2024-24576, has a CVSS score of 10.0, indicating maximum severity. That said, it only impacts scenarios where batch files are invoked on Windows with […]
Advance listen from the Berlin producer’s Alluvium LP Alluvium is the third in Berlin-based experimental producer Stefan Goldmann’s series of albums exploring the “first principles” research of metric asymmetry. Exploring new structural paths for machine rhythm in irregular metres, the album seems non-binary patterns running simultaneously, moving in and out of interlocking focus, across 12 […]
A timeless journey through ambient techno The Black Dog – Silenced (Dust Science) In the ever-evolving landscape of electronic music, few acts have left as indelible a mark as The Black Dog. Formed in 1991 amidst the vibrant sound city of Sheffield, UK, after luminaries like Cabaret Voltaire, The Human League, Heaven 17, ABC and […]
Last updated 9 April, 2024 Whether you play music that’s labelled “bootleg”, “mashup”, “re-edit” or “remix” and have wondered what these terms mean, or you’re dabbling yourself in altering or making your own versions of tunes that you own, you may have wondered what the differences are between these often-used labels. So here I’m going […]
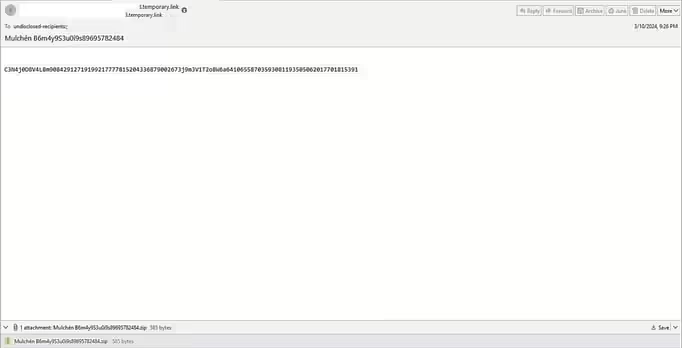
Recently, we observed a phishing campaign targeting the Latin American region. The phishing email contained a ZIP file attachment that when extracted reveals an HTML file that leads to a malicious file download posing as an invoice. Figure 1. Phishing email sample with zip file attachment Upon checking the email header, we see that […]
Apr 09, 2024NewsroomBotnet / Crypto Mining A threat group of suspected Romanian origin called RUBYCARP has been observed maintaining a long-running botnet for carrying out crypto mining, distributed denial-of-service (DDoS), and phishing attacks. The group, believed to be active for at least 10 years, employs the botnet for financial gain, Sysdig said in a report […]
The Rise of Social Media as a Browser Security Challenge In the modern workspace the lines between professional and personal digital spaces are becoming increasingly blurred. Popular social media platforms like Facebook, LinkedIn and WhatsApp, once relegated to the realm of personal interaction, have long been integrated into the fabric of daily corporate communication and […]
Apr 09, 2024NewsroomCyber Espionage / Malware Human rights activists in Morocco and the Western Sahara region are the targets of a new threat actor that leverages phishing attacks to trick victims into installing bogus Android apps and serve credential harvesting pages for Windows users. Cisco Talos is tracking the activity cluster under the name Starry […]