The mid-90s classic, originally released on Rephlex, is back after a quarter of a century Bochum Welt’s classic 1996 album Module 2, originally released on Aphex Twin’s Rephlex label, has just been reissued on vinyl with five bonus tracks via BMG. Bochum Welt – a combination of the German word for ‘world’ (welt) and the […]
A recent analysis by Cyble has revealed a concerning escalation in the fake e-shop campaign, signaling a looming threat to banking security across various regions. Initially focused on Malaysian banks, this e-shop phishing campaign has now extended its reach to financial institutions in Vietnam and Myanmar. What sets this phishing campaign apart from others on […]
Sam Purcell and Tammo Hesselink take a trip back to the early 90s Sam Purcell Blissed Out Breakbeat Hardcore 1991-94 takes a trip back to a very particular time in dance music history. Acid house, rave and techno had been with us for a while, but jungle and drum & bass culture was in its […]
Martin Schobert at Swiss security firm Pentagrid discovered that an attacker could input a series of six consecutive dashes (——) in place of a booking reference number and the terminal would return an extensive list of room details.
Hackers are using Facebook advertisements and hijacked pages to promote fake Artificial Intelligence services, such as MidJourney, OpenAI’s SORA and ChatGPT-5, and DALL-E, to infect unsuspecting users with password-stealing malware.
Two China-based Android app developers are being sued by Google for an alleged scam targeting 100,000 users worldwide through fake cryptocurrency and other investment apps. The company is taking action after scammers reportedly tricked victims with bogus promises of high returns from Android apps offering cryptocurrency investment opportunities. At least 87 fake apps on Google […]
Apr 08, 2024NewsroomSoftware Security / Cybersecurity Google has announced support for what’s called a V8 Sandbox in the Chrome web browser in an effort to address memory corruption issues. The sandbox, according to V8 Security technical lead Samuel Groß, aims to prevent “memory corruption in V8 from spreading within the host process.” The search behemoth […]
Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development A Fake Software Library Made Up by a ChatBot Was Downloaded More Than 35,000 Times Rashmi Ramesh (rashmiramesh_) • April 5, 2024 Generative artificial intelligence can hallucinate its way into providing an opportunity for hackers. (Image: Shutterstock) Generative artificial intelligence is good […]
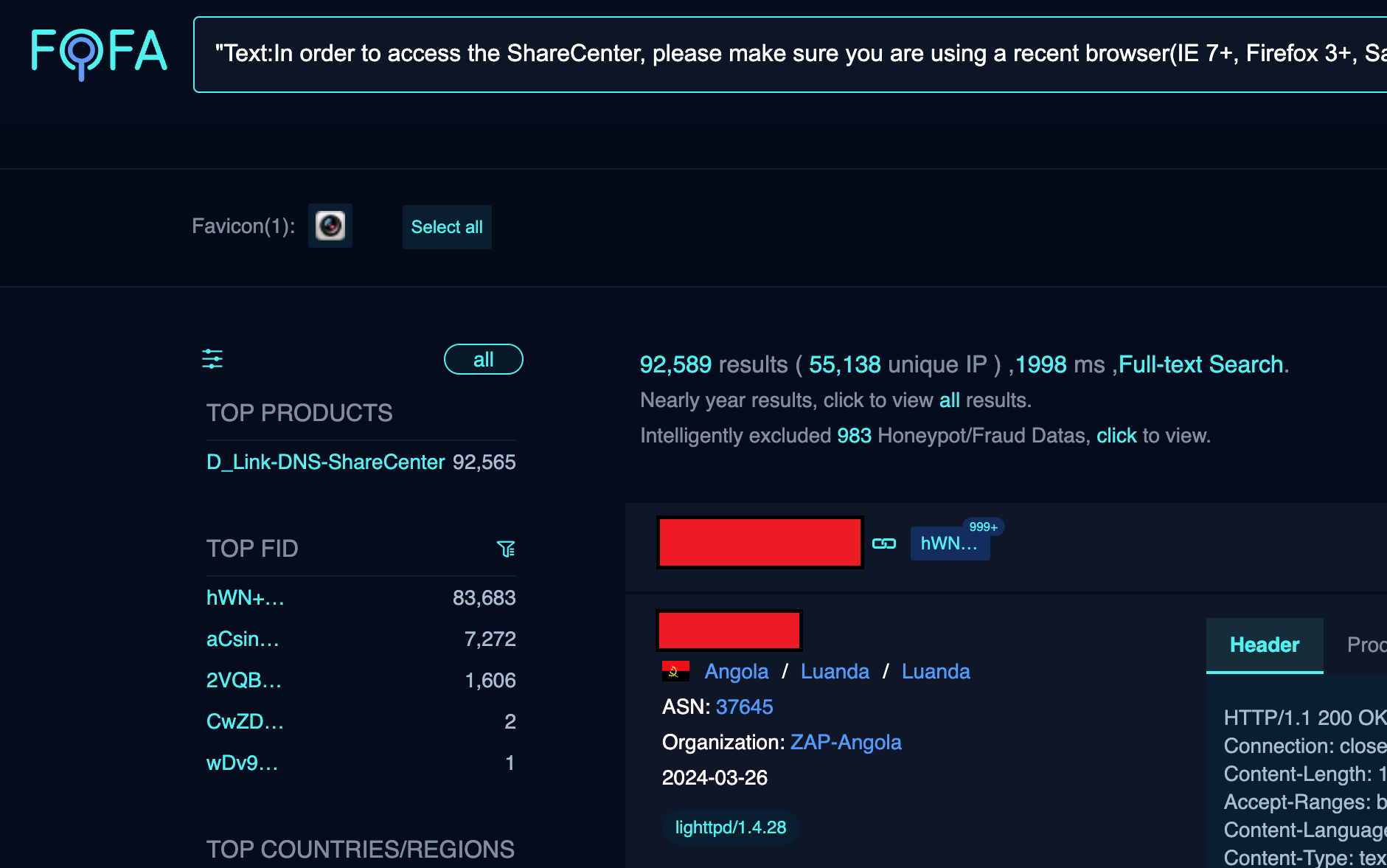
Over 92,000 Internet-facing D-Link NAS devices can be easily hacked Pierluigi Paganini April 07, 2024 A researcher disclosed an arbitrary command injection and hardcoded backdoor issue in multiple end-of-life D-Link NAS models. A researcher who goes online with the moniker ‘Netsecfish’ disclosed a new arbitrary command injection and hardcoded backdoor flaw, tracked as , tracked […]
- 1
- 2