As development environments grow more complex, applications increasingly communicate with many external services. When a software development project communicates with an external service, it utilizes a token or “secret” for authentication. These tokens are the glue that keeps any modern application together, and there is a staggering volume and variety of them in code today. […]
On February 23, 2024, medQ, Inc. filed a notice of data breach with the Attorney General of Maine after discovering that hackers accessed and encrypted a software platform used by medQ. In this notice, medQ explains that the incident resulted in an unauthorized party being able to access consumers’ sensitive information, which includes their names, […]
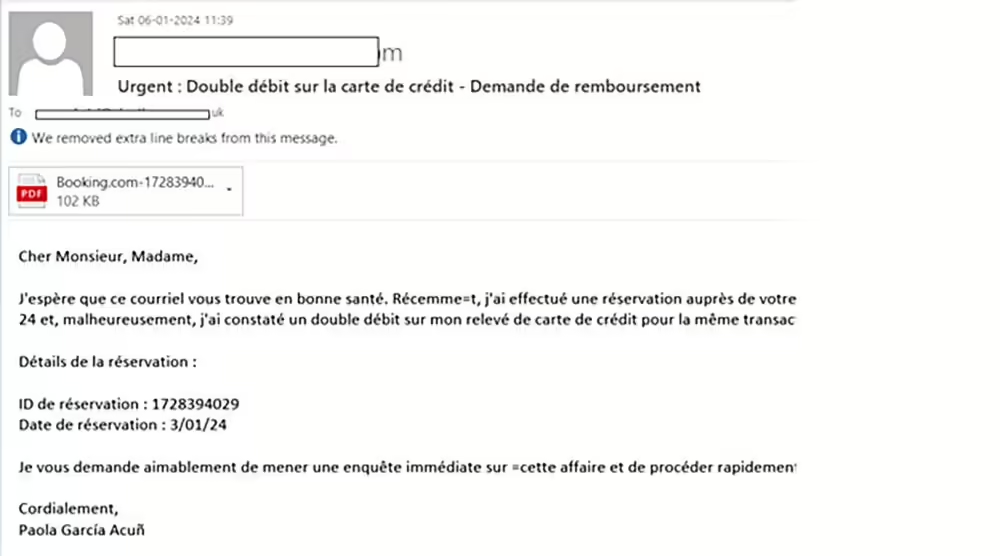
Today, we are going to look at one of the similar campaigns which is delivered via email as a PDF attachment and ends up downloading a RAT leaving the system infected. The email here is an example of scamming and brand impersonation where sender is seeking a refund of a reservation made at Booking.com and […]
What is a printed circuit board (PCB)? A printed circuit board (PCB) is a structure for assembling electronic components and their connections into a unified circuit that allows electrical current to pass between components. The PCB baseboard is typically made of a rigid nonconductive material, although it can also be built on a flexible base […]
Feb 28, 2024NewsroomPhishing Attack / Malware Mexican users have been targeted with tax-themed phishing lures at least since November 2023 to distribute a previously undocumented Windows malware called TimbreStealer. Cisco Talos, which discovered the activity, described the authors as skilled and that the “threat actor has previously used similar tactics, techniques and procedures (TTPs) to […]
Morphisec Threat Labs has shared details of a new campaign that used steganography techniques to deliver the Remcos RAT onto the systems of a Ukrainian entity operating in Finland. The campaign, attributed to a hacking group named UAC-0184, used a relatively new IDAT Loader to drop the trojan. Modus operandi According to researchers, the attack […]
Feb 28, 2024NewsroomFirmware Security / Vulnerability In a new joint advisory, cybersecurity and intelligence agencies from the U.S. and other countries are urging users of Ubiquiti EdgeRouter to take protective measures, weeks after a botnet comprising infected routers was felled by law enforcement as part of an operation codenamed Dying Ember. The botnet, named MooBot, […]
What is a context switch? A context switch is an operation that a computer’s central processing unit (CPU) carries out when alternating between processes or threads while ensuring that the processes do not conflict. Effective context switching makes it possible to support a multitasking environment. Each time the CPU makes a switch, the system temporarily […]
2ManyDJs also on the bill Underworld are to headline a massive beach party in Brighton hosted by Manchester clubbing institution Bugged Out. Bugged On The Beach, a party to celebrate the club’s 30th birthday, is on Saturday July 20 and will run from 1.30pm-10.30pm. 2manyDJs, Boys Noize, Eats Everything, Mall Grab, Chloé Robinson, Emerald and […]