The organization is working with external IT security experts to restore its communication channels and is committed to informing affected individuals if a data compromise is confirmed.
A growing divide separates leaders with a firm grasp on digital trust from those at the bottom of the pool, according to DigiCert. While digital trust overwhelmingly remains a critical focus for all enterprises, the latest report from DigiCert shines a light on the growing divide between the ‘leaders’ (those who are getting it right), […]
The company has initiated containment measures, enlisted the help of law enforcement and cybersecurity experts, and is currently investigating the incident, with no confirmation yet on the impact to their finances or operations.
Meta, the owner of Facebook and Instagram, is ramping up its efforts to protect users from disinformation ahead of the European Parliament elections in June. The company announced on Sunday that it plans to set up a team of intelligence experts, data scientists, engineers and researchers in Europe who will be tasked with identifying and […]
Superusers Need Super Protection: How to Bridge Privileged Access Management and Identity Management
Feb 28, 2024The Hacker NewsZero Trust / Cyber Threat Traditional perimeter-based security has become costly and ineffective. As a result, communications security between people, systems, and networks is more important than blocking access with firewalls. On top of that, most cybersecurity risks are caused by just a few superusers – typically one out of 200 […]
Feb 27, 2024NewsroomVulnerability / Website Security A security vulnerability has been disclosed in the LiteSpeed Cache plugin for WordPress that could enable unauthenticated users to escalate their privileges. Tracked as CVE-2023-40000, the vulnerability was addressed in October 2023 in version 5.7.0.1. “This plugin suffers from unauthenticated site-wide stored [cross-site scripting] vulnerability and could allow any […]
Many industrial organizations lack the resources, expertise, and collaborative processes to effectively mitigate threats and ensure secure access to operational technology (OT) systems, according to Cyolo. Ensuring secure access to OT environments is about more than just cybersecurity. These environments contain highly sensitive systems and critical infrastructure responsible for keeping manufacturing lines running, water and […]
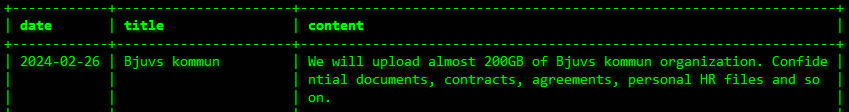
The Akira ransomware group has set its sights on yet another target: the municipality of Bjuv in Skåne County, South Sweden. The notorious hacker group, known for its brazen cyberattacks against Swedish entities, has issued a warning on the dark web, threatening to leak nearly 200GB of stolen data from Bjuv Municipality’s systems. The ransomware […]
Dive Brief: Corporate finance chiefs play a less active role compared with information technology leaders when it comes to key aspects of complying with new cybersecurity rules from the Securities and Exchange Commission, according to a recent survey by AuditBoard, a cloud-based risk management company. Among other provisions, the rules require a public company to […]