The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical infrastructure networks in the country for at least five years. Targets of the threat actor include communications, energy, transportation, and water and wastewater systems sectors in the U.S. and Guam. “Volt Typhoon’s choice of […]
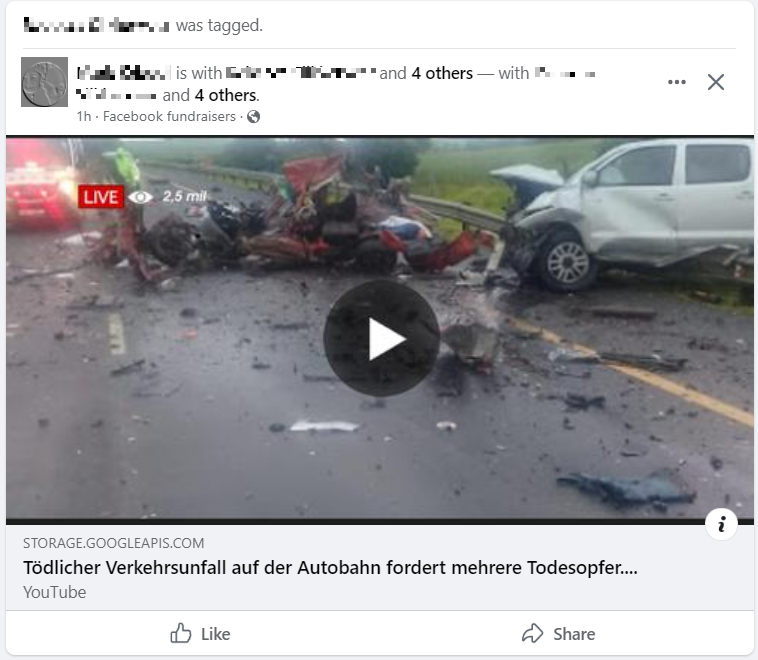
Recently I wrote about a malvertising campaign on Facebook that has been going on for almost a year. Apparently Facebook is struggling to stop this campaign, so now this type of campaign is showing up in other languages than English. I have seen two different types in German. First Facebook scam Translation: Deadly accident on […]
Data serialization languages, like Extensible Markup Language and YAML Ain’t Markup Language, are typically found in infrastructure-as-code management software. Understand the differences and use cases between XML and YMAL to maximize your automation potential in application development. XML and YAML provide administrators with many options to automate and structure data. However, knowing the differences enables […]
NinjaOne, an Austin, TX-based provider of an IT platform for endpoint management, security, and visibility, raised $231.5M in Series C funding. The round was led by ICONIQ Growth. Frank Slootman, Chairman and CEO of Snowflake, and Amit Agarwal, President of Datadog, among others, also participated. This minority investment valued the company at $1.9 Billion. With […]
Feb 08, 2024The Hacker NewsUnified Identity / Cyber Security If you’ve listened to software vendors in the identity space lately, you will have noticed that “unified” has quickly become the buzzword that everyone is adopting to describe their portfolio. And this is great! Unified identity has some amazing benefits! However (there is always a however, […]
The Chinese threat group Volt Typhoon, also known as Bronze Silhouette, attempted to revive a botnet used in attacks on critical infrastructure in the U.S. after the FBI dismantled it.
Feb 08, 2024NewsroomEndpoint Security / Cyber Threat The threat actors behind a loader malware called HijackLoader have added new techniques for defense evasion, as the malware continues to be increasingly used by other threat actors to deliver additional payloads and tooling. “The malware developer used a standard process hollowing technique coupled with an additional trigger […]
Feb 08, 2024NewsroomData Protection / Mobile Securit Google has unveiled a new pilot program in Singapore that aims to prevent users from sideloading certain apps that abuse Android app permissions to read one-time passwords and gather sensitive data. “This enhanced fraud protection will analyze and automatically block the installation of apps that may use sensitive […]
CISA adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 07, 2024 U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Google Chromium V8 Type Confusion bug, tracked as […]