Dozens of environments and hundreds of individual user accounts have already been compromised in an ongoing campaign targeting Microsoft Azure corporate clouds. The activity is in some ways scattershot — involving data exfiltration, financial fraud, impersonation, and more, against organizations in a wide variety of geographic regions and industry verticals — but also very honed, […]
Files encrypted by Rhysida ransomware can be successfully decrypted, due to a implementation vulnerability discovered by Korean researchers and leveraged to create a decryptor. Rhysida and its ransomware Rhysida is a relatively new ransomware-as-a-service gang that engages in double extortion. First observed in May 2023, it made its name by attacking the British Library, the […]
Cohesity is buying Veritas’ data protection business, combining both into a single company operating under the Cohesity name. The blended company, which holds an estimated combined value of $7 billion, will focus on data security and data management, uniting Cohesity’s focus on SaaS applications with Veritas’ continued support of protecting on-premises data. It will be […]
Today, CISA partnered with the Open Source Security Foundation (OpenSSF) Securing Software Repositories Working Group to publish the Principles for Package Repository Security framework. Recognizing the critical role package repositories play in securing open source software ecosystems, this framework lays out voluntary security maturity levels for package repositories. This publication supports Objective 1.2 of CISA’s […]
The Hipocrate Information System (HIS) used by hospitals to manage medical activity and patient data was targeted over the weekend and is now offline after its database was encrypted.
UNITED NATIONS (AP) — U.N. experts say they are investigating 58 suspected North Korean cyberattacks between 2017 and 2023 valued at approximately $3 billion, with the money reportedly being used to help fund its development of weapons of mass destruction. And the high volume of cyberattacks by North Korean hacking groups who report to the […]
National Cyber Director Harry Coker this week reiterated prior warnings that hackers linked to the People’s Republic of China are actively working to gain access to critical infrastructure in the U.S. to potentially launch malicious attacks. Coker, in his first major speech in Washington since he was confirmed in December, said the state-linked threat actors […]
Feb 12, 2024NewsroomVulnerability / Data Recovery Cybersecurity researchers have uncovered an “implementation vulnerability” that has made it possible to reconstruct encryption keys and decrypt data locked by Rhysida ransomware. The findings were published last week by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA). “Through a comprehensive analysis […]
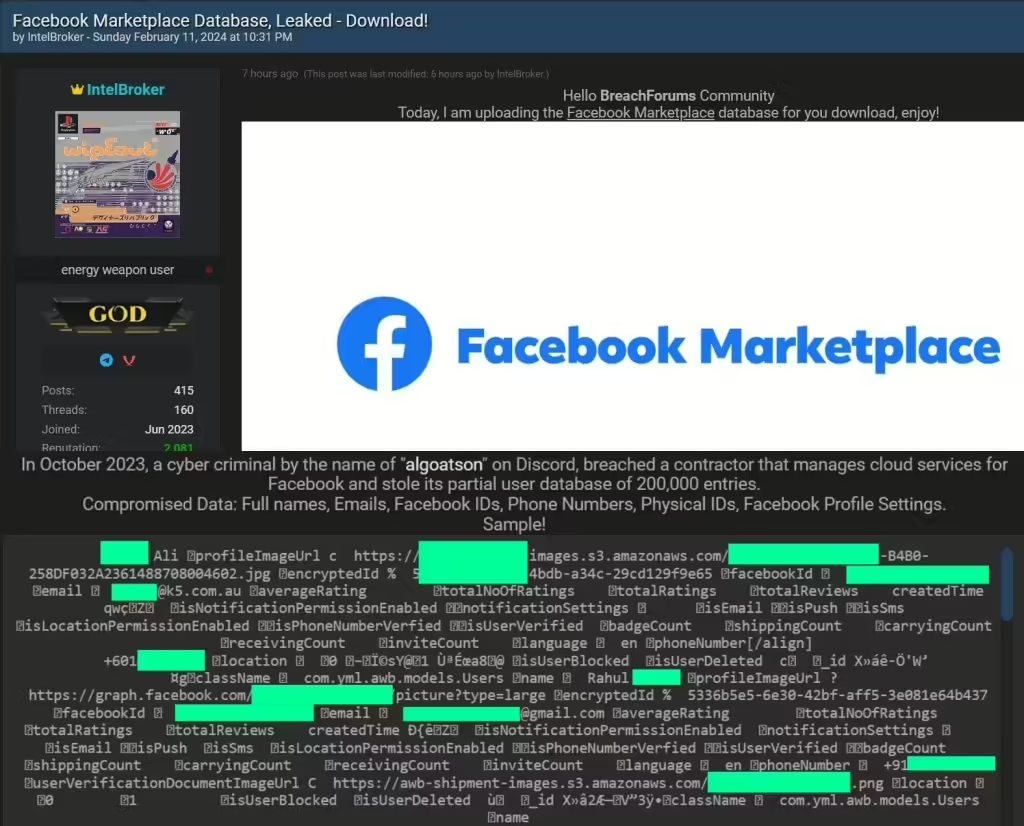
The alleged partial Facebook Marketplace database has been leaked on Breach Forums by the infamous threat actor IntelBroker. They claim that another actor, using the alias “algoatson,” stole the database from a contractor responsible for managing cloud services for Facebook. The infamous threat actor known as IntelBroker has claimed responsibility for leaking a partial database […]