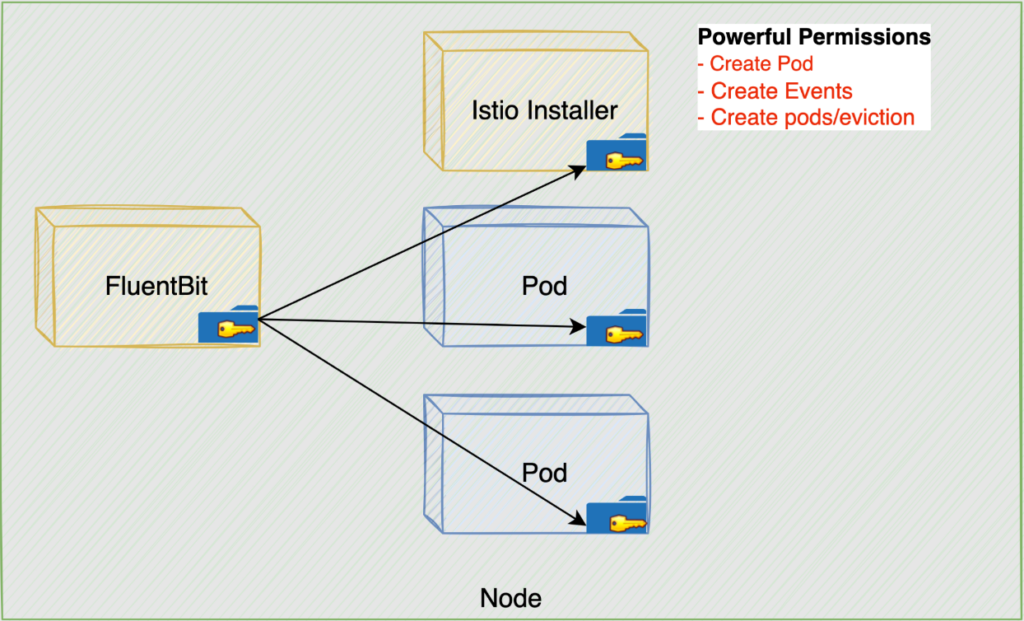
A recent Unit 42 investigation revealed a dual privilege escalation chain impacting Google Kubernetes Engine (GKE). This exploit chain arises from specific misconfigurations in GKE’s FluentBit logging agent and Anthos Service Mesh (ASM). When combined, these issues could provide attackers with existing Kubernetes cluster access an opportunity to escalate privileges. Kubernetes, a widely adopted open-source […]
As the DJing world continuously evolves, new gear is an inevitability. 2024 is likely to bring a solid set of new products to the DJ world, and we expect to see new gear that could transform how we mix, manipulate, and experience music. From stem-focused controllers to iterative updates from Pioneer DJ, we expect smart […]
Jan 01, 2024NewsroomWindows Security / Vulnerability Security researchers have detailed a new variant of a dynamic link library (DLL) search order hijacking technique that could be used by threat actors to bypass security mechanisms and achieve execution of malicious code on systems running Microsoft Windows 10 and Windows 11. The approach “leverages executables commonly found […]
Jan 01, 2024NewsroomEncryption / Network Security Security researchers from Ruhr University Bochum have discovered a vulnerability in the Secure Shell (SSH) cryptographic network protocol that could allow an attacker to downgrade the connection’s security by breaking the integrity of the secure channel. Called Terrapin (CVE-2023-48795, CVSS score: 5.9), the exploit has been described as the […]
Jan 01, 2024NewsroomMalware / Dark Web A new Go-based malware loader called JinxLoader is being used by threat actors to deliver next-stage payloads such as Formbook and its successor XLoader. The disclosure comes from cybersecurity firms Palo Alto Networks Unit 42 and Symantec, both of which highlighted multi-step attack sequences that led to the deployment […]