The end of support for these older Windows versions is due to the reliance on an embedded version of Google Chrome that no longer functions on them, as well as the need for Windows feature and security updates only available on Windows 10 and above.
What is a configuration management database (CMDB)? A configuration management database (CMDB) is a file — usually in the form of a standardized database — that contains all relevant information about the hardware and software components used in an organization’s IT services and the relationships among those components. A CMDB stores information that provides an […]
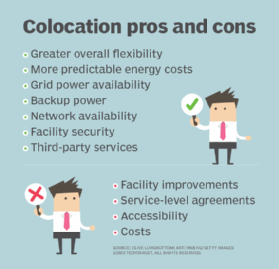
What is colocation (colo)? A colocation facility (colo) is a data center or telecommunications facility in which a business can rent space for servers, storage devices and other computing and networking hardware. Typically, a colo provides the building, cooling, power supply, voice and data network bandwidth, internet access and physical security, while the customer provides […]
Managing and allocating budgets for cybersecurity and IT has become an increasingly critical aspect of organizational strategy. Organizations recognize the need to invest significantly in cybersecurity to safeguard sensitive data, protect against ransomware attacks, and ensure the integrity of their IT infrastructure. A well-structured cybersecurity budget is crucial for staying ahead of emerging threats and […]
Xerox said a subsidiary is dealing with a cyberattack that may have involved the theft of personal information. Last week a ransomware gang named INC claimed it attacked the company — which earned over $7 billion in 2022 from selling printers in more than 160 countries. When asked about the claims, a spokesperson for Xerox […]
Court cases and tribunals in Australia have been impacted by a cybersecurity incident, with attackers potentially accessing recordings of hearings, according to the Court Services Victoria (CSV). The CSV revealed the incident in a statement on January 2, 2024. This public notice came some 12 days after the CSV was first alerted to the cyber […]
Android Game Developer’s Google Drive Misconfiguration Leaks Information on Nearly One Million Users
A simple Google Drive configuration mistake by Japanese game developer Ateam resulted in the potential exposure of sensitive information for nearly one million individuals, highlighting the importance of properly securing cloud services.
The classics that techno was Modelled on The mid-1980s was a crucial time in Detroit techno history: a rapidly fluctuating scene on the horizon with the likes of +8, Underground Resistance and Octave One all waiting around the corner and due to rapidly shift the sound of techno and electronic music in the early 90s. […]
While the decryptor only works on older versions of Black Basta and has been patched in newer attacks, it provides hope for victims who were affected between November 2022 and the recent bug fix.