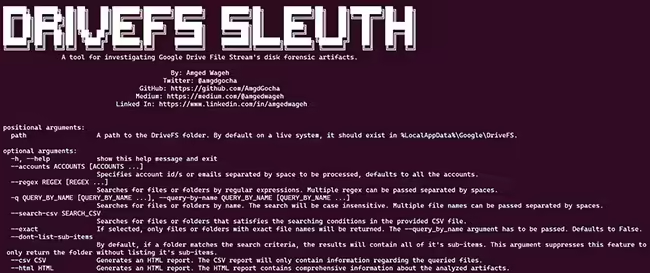
DriveFS Sleuth automates the investigation of Google Drive File Stream disk artifacts. The tool can parse the disk artifacts and build a filesystem tree-like structure enumerating the synchronized files along with their respective properties. “While engaged in a threat-hunting activity for a client to detect the misuse of file-syncing applications within their network, I identified […]
Airbus is expected to offer between €1.5 to 1.8 billion (~$1.64 to 1.97 billion) for Atos’ Big Data & Security division, in line with its goal of growing its cybersecurity arm and enhancing its defense and security portfolio.
Attackers need to be in an adversary-in-the-middle position to intercept and modify the handshake exchange, making network compromise a key factor in executing the Terrapin attack.
The Twitter account of cybersecurity firm Mandiant, which is owned by Google, was hacked and used to promote a cryptocurrency scam. The attacker impersonated the Phantom crypto wallet and shared a fake website offering free tokens.
Suits you, maam Gone are the days when underground dance sub-cultures stayed in their own territory – and a good thing too. Check a DJ set by Tailor Jae – her Boiler Room session for example – and you’ll hear everything from the dancehall-infused bass of Omaar to Lenny De Ice’s timeless rave classic We […]
The mayor of Pays Fouesnantais, a coastal township in Brittany in northwestern France, announced his municipal authority had been hit by a “large-scale” cyberattack that had taken down all of its community services. The nature of the attack has not yet been confirmed. Roger Le Goff, the mayor, told local newspaper Ouest-France that the incident […]
A surge of fake or stolen X (Twitter) Gold accounts has been flooding marketplaces and forums both on the surface web and the dark web over the past year, according to CloudSEK. Threat actors have used multiple techniques to forge or steal X Gold accounts since Elon Musk’s firm introduced its new verified accounts program […]
Qualcomm disclosed a critical vulnerability on New Year’s Day that would allow remote attacks via malicious voice calls over LTE networks. The January 2024 security bulletin lists a total of 26 vulnerabilities, including four critical vulnerabilities, affecting Qualcomm chipsets. Patches have already been made available to original equipment manufacturers (OEMs) whose devices use Qualcomm chips, […]
Security vendor SonicWall is expanding its zero-trust network offerings with the acquisition of Banyan Security. On Wednesday, SonicWall announced that it acquired Banyan Security, a startup founded in 2015 that provides a cloud-based zero-trust network access (ZTNA) security architecture through its security service edge (SSE) platform. SonicWall purchased Banyan for an undisclosed amount on Dec. […]